

After burglaries, mystery car unlocking device has police stumped. It's February, about an hour after midnight, and three men in oversized clothing and hats walk silently down a deserted residential street in Long Beach, California.
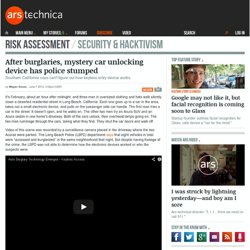
Each one goes up to a car in the area, takes out a small electronic device, and pulls on the passenger side car handle. The first man tries a car in the street. It doesn't open, and he walks on. The other two men try an Acura SUV and an Acura sedan in one home's driveway. Both of the cars unlock, their overhead lamps going on. Video of this scene was recorded by a surveillance camera placed in the driveway where the two Acuras were parked. In April, the Long Beach Police posted the surveillance video on YouTube , desperate to figure out just how the electronic device used by the three suspects works. Create and print secure tickets with barcodes or qr codes. Printing secure tickets or badges, which cannot be forged or copied, has never been easier and cheaper!
Just use the TicketCreator Barcode edition to create and print tickets with a unique barcode on each ticket. TicketCreator prints on each ticket a unique 10-digit number as a barcode, which is checked at the entrance with the BarcodeChecker software and a simple barcode scanner (USB or PS/2, starting at € 50,-/ $ 60,-/ £ 45,-), a webcam or an Android phone. Each barcode can only be used once to enter.
Therefore, copied or forged tickets are rejected and your revenues are protected. Long Range WiFi Antennas USB Adapters Coaxial Cables and WiFi Tutorials. Long Range WiFi Antennas USB Adapters Coaxial Cables and WiFi Tutorials. DEF CON 21 Presentation By ZOZ - Hacking Driverles. DEFCON 20: Bypassing Endpoint Security for $20 or Less. Katy Levinson, Don't Fix It In Software, Defcon 19. DEFCON 20: The Art Of The Con. Defcon 18 - Programmable HID USB keystroke Dongle - Adrian Crenshaw - Part.mov.
Pwned again: An exclusive look at Pwnie Express’ newest hack-in-a-box. Tomorrow at the Black Hat security conference in Las Vegas, the Pwnie Express will officially unleash Pwn Plug R2, the next generation in its arsenal of penetration testing and hacking hardware.
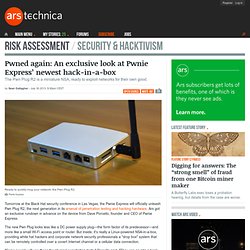
Ars got an exclusive rundown in advance on the device from Dave Porcello, founder and CEO of Pwnie Express. Power strip or network hacking tool? It’s both, actually. Pwnie Express drew a lot of attention earlier this year with its Pwn Plug, a stealthy, small computer loaded with network hacking tools disguised in an innocuous, white power brick that resembles an air freshener—albeit one with Ethernet and USB ports. Now, with funding from the Defense Advanced Research Projects Agency’s Cyber Fast Track program, the company has created an even stealthier tool for testing and cracking networks: one disguised as a power strip. The Power Pwn, now available for preorder, looks and works like a surge-protecting power strip, with eight functional 120 volt outlets. But it is also a Linux-based computer loaded with hacking software, including high-gain WiFi and Bluetooth antennas as well as dual Ethernet ports.
Professor fools $80M superyacht’s GPS receiver on the high seas. One of the world’s foremost academic experts in GPS spoofing—University of Texas assistant professor Todd Humphreys—released a short video on Monday showing how he and his students deceived the GPS equipment aboard an expensive superyacht.
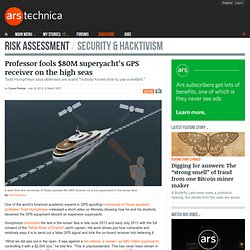
Humphreys conducted the test in the Ionian Sea in late June 2013 and early July 2013 with the full consent of the “White Rose of Drachs” yacht captain. His work shows just how vulnerable and relatively easy it is to send out a false GPS signal and trick the on-board receiver into believing it. “What we did was out in the open. It was against a live vehicle, a vessel—an $80 million superyacht, controlling it with a $2,000 box,” he told Ars. “This is unprecedented. Trusting iPhones plugged into bogus chargers get a dose of malware. Plugging your phone into a charger should be pretty safe to do.
It should fill your phone with electricity, not malware. But researchers from Georgia Institute of Technology have produced fake chargers they've named Mactans that do more than just charge your phone: they install custom, malicious applications onto iPhones. Their bogus chargers—which do, incidentally, charge the phone—contain small computers instead of mere transformers. The iPhone treats these computers just as it does any other computer, but instead of just charging, it responds to USB commands.
Pwned again: An exclusive look at Pwnie Express’ newest hack-in-a-box. Tomorrow at the Black Hat security conference in Las Vegas, the Pwnie Express will officially unleash Pwn Plug R2, the next generation in its arsenal of penetration testing and hacking hardware.
Ars got an exclusive rundown in advance on the device from Dave Porcello, founder and CEO of Pwnie Express. Teensy USB Development Board. The Teensy is a complete USB-based microcontroller development system, in a very small footprint, capable of implementing many types of projects.

All programming is done via the USB port. DEFCON 19: Hacking Victims Over Power Lines. Teensy USB Development Board. The Teensy is a complete USB-based microcontroller development system, in a very small footprint, capable of implementing many types of projects.
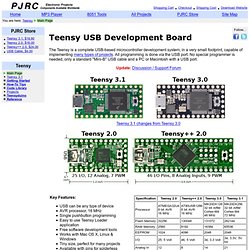
All programming is done via the USB port. DEFCON 20: Hacker + Airplanes = No Good Can Come Of This. BONUS- BLACK HAT- Barnaby Jack - Jackpotting Automated Teller Machines Redux - Video.
GSM. How to make a DIY home alarm system with a raspberry pi and a webcam. Step #1: Make your webcam stealth I wanted to hide the camera in an inconspicuous place outside my door, so I removed the webcam’s casing.
The Pen Test Drop Box Distro for the Raspberry Pi. Pentesting Appliance – Pwnie Express. On-demand Security Assessments for Remote Sites and Branch Offices Pwnie Express provides innovative and easy-to-use security testing products for today’s distributed enterprises and their hard-to-reach branch offices.

Our products are designed for: Penetration Testers: You can easily assess your security on demand.Third Party Security Assessors: Easy anytime, anyplace access without associated travel costs that take you out of the office and away from other engagements for daysAuditing Professionals: Test and assess standard applications and custom web applications to expose security weaknesses It allows you to test all of the organization’s potential threat vectors, simply and rapidly demonstrating their vulnerabilities. Pwnie Express’s products are purpose-built on open source technology that is proven and known to you and come in multiple form factors that include the Power Pwn, Pwn Plug and Pwn Pad. Pwn Pad – Pwnie Express. Pwn Plug Elite – Pwnie Express.
FareBot – Lire les cartes de transports NFC avec Android. Le NFC permet de prendre le train gratuitement. La technologie NFC, "Near Field Communication" ("Communication en champ proche"), fait ses débuts sur les smartphones les plus récents. Radio-frequency identification. Radio-frequency identification (RFID) is the wireless use of electromagnetic fields to transfer data, for the purposes of automatically identifying and tracking tags attached to objects. The tags contain electronically stored information. Some tags are powered by electromagnetic induction from magnetic fields produced near the reader.
Some types collect energy from the interrogating radio waves and act as a passive transponder. Other types have a local power source such as a battery and may operate at hundreds of meters from the reader. Unlike a barcode, the tag does not necessarily need to be within line of sight of the reader and may be embedded in the tracked object. Since RFID tags can be attached to cash, clothing, and possessions, or implanted in animals and people, the possibility of reading personally-linked information without consent has raised serious privacy concerns.[2] These concerns resulted in standard specifications development addressing privacy and security issues. Recharger son passe Navigo de chez soi ! Tout parisien aura connu l'horreur du premier jour du mois, celui où il fait la queue à 8h du matin pour recharger son passe Navigo... Déjà qu'il n'est pas aimable dans les transports en temps normal, c'est le pompon !
Désormais, il est possible de le faire bien tranquillement depuis chez soi. Des capteurs de mouvement et température sans fil. Si vous êtes un accroc de la sécurité, ou simplement un bricoleur en manque de petits joujoux, les petits capteurs qui suivent devraient vous intéresser. Hacker Opens High Security Handcuffs With 3D-Printed And Laser-Cut Keys. Comment voler une BMW en moins de 3 minutes. Le piratage de drones américains relance les débats. Les drones, ces appareils volants commandés à distance, prennent petit à petit place dans notre société.
Qu'ils soient de simples gadgets ou véritables machines de guerre, ils restent vulnérables au piratage. Commercial Drones and GPS Spoofers a Bad Mix. Researchers at the University of Texas at Austin Radionavigation Laboratory have successfully demonstrated that a drone with an unencrypted GPS system can be taken over by a person wielding a GPS spoofing device. You can see a video accompanying a Fox News story on it, as well as a video here of an experiment conducted by the researchers, led by Professor Todd Humphreys. Humphreys and company were recently invited by the U.S. Department of Homeland Security (DHS) to demonstrate whether their capability to successfully spoof commercial GPS systems in the laboratory could work in the field. Spoofing, as defined in this article by UT researchers, is “the transmission of matched-GPS-signal-structure interference in an attempt to commandeer the tracking loops of a victim receiver and thereby manipulate the receiver’s timing or navigation solution.
Les imprimantes 3D : un véritable problème pour les constructeurs de menottes. Des hackers volent une BMW sans clé en 180 secondes. N'allons pas faire de ce cas une généralité. Une porte dérobée dans le matériel militaire. Le domaine militaire est ultra sécurisé et c’est tant mieux. Mais s’il l’est tant au niveau logiciel, il l’est peut-être moins quand on plonge dans les composants des missiles ou des bombes nucléaires...
Sergei Skorobogatov, un chercheur de Cambridge, vient de publier un rapport affirmant que de nombreux appareils militaires, des systèmes d’armement aux centres nucléaires, pourraient être compromis à cause de la présence d’un composant bien particulier: le FPGA. Des tags NFC programmables pour Samsung. CrackingCreditCode.jpg (Image JPEG, 600x1708 pixels) How To Win Over Your Boss. How to Turn Your Webcam Into a Streaming, Motion-Detecting Surveillance System. L’écran spécial vie privée. At Turntable.fm, SMS texts, not keys, open doors. - Shareables. Cammster Uses Your Browser and Webcam For Motion-Sensitive Home Security.
Hacking from the sky with the W.A.S.P - Part 1. DIY UAVs for Cyber Warfare – Wireless Aerial Surveillance Platform. Hack Attack: Turn your $60 router into a $600 router. Une caméra thermique pour dérober un code secret. Si vous êtes le genre de personne à cacher d'une main le clavier des distributeur de banque pour éviter qu'on vous pique votre code secret grâce à une petit caméra planquée dans un coin : bravo ! Mais cela ne suffit plus vraiment car des chercheurs ont mis au point une technique assez simple, je trouve, à base de caméra thermique, qui permet simplement en filmant le clavier du DAB, de deviner le code utilisé par la personne qui vient juste de passer.
Les touches utilisées emmagasinent de la chaleur, qui s'estompe de 80% après 10 secondes, à 60% après 45 secondes, ce qui permet directement de deviner l'ordre dans lequel ont été tapées les touches. La technique ne fonctionne pas avec des claviers en métal mais cartonne sur les claviers en plastique. Du coup, une caméra thermique planquée sera diablement efficace car une fois le code tapé, les gens qui cachent le clavier avec leur autre main, la retire, laissant apparaitre ces points de chaleur. Suffisait d'y penser. Livebox 2 Unlocker. Apparemment, ce serait la panique en ce moment chez Orange car des développeurs espagnols ont diffusé une application permettant d'exploiter les Livebox 2 espagnoles et françaises directement en mode root. C'est à dire, très simplement via une interface graphique, de dévérouiller des menus cachées concernant la visio, livezoom, le VPN, le fax, la sauvegarde...etc.
De dévérouiller des options de paramétrage réseau comme le DHCP, FTLock, TVrouted...etc ainsi que les paramètre de certains services concernant la téléphonie ou le wifi. Bref, une floppée de choses qu'on ne peut pas faire en temps normal sur une LiveBox. How To Coke Machine Jackpot Hack - a News &Politics video. How to hack a vending machine - a Sports et Extrême video. This Cheap Air Drone Can Break Into Your Computer and Own It. Man In The Middle Attack - Ethical Hacking Example.
Q&A: New Fraud and Identity Theft Rules. Are your customers safe from online scamsters? How to comply with the FTC's new 'Red Flags' program. Q: I recently learned about the Federal Trade Commission's Red Flags Rule, requiring businesses to plan a response to identity theft and fraud. SELECTRONIC : Composants Electroniques, Systèmes d’Alarme, Matériel Electronique. A Crimping Tool For Making Your Own Speaker Wire. OpenPCR – Du biohacking open source.