

Soni Singh
A leading advanced cyber security service provider company LTS Secure and CyberStone team up to capture growth opportunities to provide a comprehensive Cyber Security Solutions with continuous monitoring at all layers of the IT stack.
Chicago, USA- February 25, 2021 – LTS Secure, a leading provider of advanced cyber security services, today announced that it has formed a strategic MSSP partnership with CyberStone, an international IT consulting, advisory and technologies services company headquartered in Riyadh with a global reach. By partnering with LTS Secure, as a Managed Security Service Providers (MSSPs), CyberStone will provide the Middle East based customers a comprehensive Cyber Security Solutions with continuous monitoring at all layers of the IT stack i.e. network packets, OS activities, content, and user behaviours.
CyberStone has been using leading platforms to deliver value to clients for more than two decades. Evaluate Company - Level Controls Every user action and activities onto an application is tracked and stored, All textual metadata logs are tied to the specific user, providing visibility into who is doing what and when.
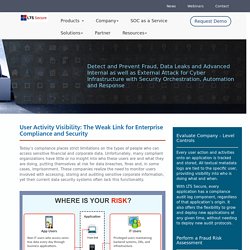
With LTS Secure, every application has a compliance audit log component, regardless of that application’s origin. It also offers the flexibility to grow and deploy new applications at any given time, without needing to deploy new audit protocols. Perform a Fraud Risk Assessment. LTS Secure AMPLIFY MSSP Partner Managed Security Services Provider Program MSSP Program is tailored to meet the needs of partners like you who want to provide Security offerings to their clients. The program gives you a framework for pricing models, simple reporting, licenses, onboarding resellers, and optimized partner support to help you extend business growth and the value you offer your customers. Ideal MSSP’s Include Pure-play managed security service providers looking to incorporate world-class solutions.
MSSP Benefits. LTS Secure launches 'AMPLIFY' aiming towards more profitable partnerships. “LTS Secure, a leading provider of advanced cyber security services, unveiled a new partnership program ‘AMPLIFY’. Zero Trust Security: The answer to an increasingly challenging environment. Organizations today face an increasingly challenging environment where they have to manage employees using their own laptops, smart phones and tablets to work remotely.
On top of that, cyber threats are becoming ever-more cultured and wide spread. A number of digital transformation initiatives are forcing businesses to rethink their enterprise security architecture. A strategic initiative by LTS Secure - “FORTIFY” You are signed out.
Pin on cyber security solutions. Strengthen Security Ecosystem with LTS Secure - COME, E-MEET, AND EMBRACE THE NEW RELATIONSHIP. LTS Secure Intelligence Driven SOC is integrated Context-aware Security protection platform that provides and integrates prediction, prevention, detection and response capabilities by leveraging adaptive security framework.
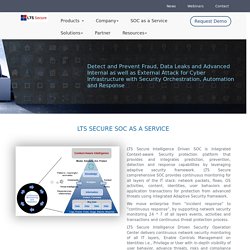
LTS Secure comprehensive SOC provides continuous monitoring for all layers of the IT stack: network packets, flows, OS activities, content, identities, user behaviors and application transactions for protection from advanced threats using integrated Adaptive Security framework. Establishing Access Management for Finance Industry: LTS Secure VSOC Box − Establishing controls around privileged access continues to be a focus of attention for organizations and auditors.

With hacking and cyber-attacks at peak, companies need to be vigilant at every entry point that can possibly act as vulnerability in their business structure. Our client creates value for finance industry pyramid with enormous clientele and converting dreams into reality for numerous customers, while striving to serve common people through ‘quality non-banking’ financial services. Our client approached us to protect their IT network by detecting and mitigating all potential vulnerabilities.
A large customer base for our client meant a large amount of valuable data, and protecting this data was of prime importance. Data loss, misuse, leaks and breaches through many entry points threatened the client’s business structure every single day. Cyber Risk Quantification: LTS Secure VSOC Box for Insurance Sector − Our Client, an established and profitable chain of companies in insurance sector serving about 1.5Million customers and managing assets in millions of dollars.

With their parent company, our client gives us an opportunity to serve the insurance domain yet again with an interesting project. LTS Secure “VSOC” Box 5.0: Empowering the Gen Z cyber security − Pune: 31/03/2020 Though times needs though soldiers, we are very proud of our development & testing team who finished LTS Secure VSOC Box 5.0 release battling all difficulties and paved stepping stone of features for latest version of LTS Secure’s flagship product V-SOC BOX version 5.0.

The new and improved V-SOC BOX provides stronger multilayer IT security preventing cyber-attacks by proactive monitoring of networks and immediate response to mitigate risks. Enhancing business wide security by proactively monitoring vulnerabilities through multiple IT layers, the improved V-SOC BOX 5.0 provides new features in addition to improved existing features from the earlier version. Following is non exhaustive list of improved features of V-SOC BOX version 5.0: Alarm Labelling: Duplicate alarms are labelled automatically following the defined algorithms of previously traced and labelled alarm with module implementation to open tickets.
Why you need Intelligence Driven SOC to Stay Secure − Webinar on - Why you need Intelligence Driven SOC to Stay Secure Tickets, Thu, Mar 19, 2020 at 8:30 AM. Security threats are evolving and cyber-criminals are innovating quickly with the advent of advanced persistent threats.
In response, cyber-security is evolving too and that is where the advantages of using the SOC as a Service lie/remain. LTS Secure’s SOC as a Service delivers capabilities such as 24/7 security monitoring services using SIEM (Security Information and Event Management) technology, targeted threat intelligence, vulnerability management and critical incident response, integrates prediction, prevention, detection and response capabilities by leveraging adaptive security framework. Key Highlights of SOC as a Service Webinar: How Threat Intelligence Can Help Combat Cybercrime Tickets, Wed, Mar 11, 2020 at 5:00 PM. With the rise in cyber-attacks & the sophistication with which cybercriminals are caring out their attacks, organizations from all domains are turning to intelligence driven security analytics & threat intelligence to drive their cybersecurity program.
Knowing the ins & outs of the current threat landscape is key in order for SOC teams to take appropriate response to high profile attacks & breaches. Attend this webinar to learn about how actionable threat intelligence looks like. Key highlights of the Webinar: Importance of threat intelligence Types of threat intelligence When & where it is being used. Enterprise data breaches continue to increase at an alarming pace. Organizations have too many alerts, too many technologies and not enough people.
Security teams are overwhelmed, and it has become clear that traditional controls are no longer enough to keep data safe. Enabling Threat Detection & Risk Management Tickets by Shyam Nair, 11 Dec, 2019, online Event. Enabling Threat Detection & Risk Management Tickets, Wed, Dec 11, 2019 at 5:00 PM. Risk management is the ability to mitigate the organization’s risk, which encompasses multiple risks including compliance and threat risk. This use case is roughly the average of the compliance management requirements and the threat management requirements. This use case highlights management of the entire organization’s risk, not just that of information security .
Join us to know details on: Correlation and analysis of event data. Configure monitoring for all critical assets. Speaker Details – Sagar – Security Analyst. Identity And Access Governance. Access Governance Access Governance is a combined model of process and technology to manage and secure access for the enterprise resources. It plays a key role in developing security infrastructure. IT professionals with evolving roles recognize that managing and controlling security environment can be more challenging.
LTS Secure recognizes that, Access Governance capabilities will continue to leverage technologies to realize higher benefits versus the costs incurred. User demand will continue to drive the discipline to transform from a compliance-based program into a true business enabler (e.g., Access Recertification and Identity Management is a key component for rolling out B2C applications, that will drive operational efficiencies and improve the user experience) while helping to reduce risks created by emerging technologies and threats. Core Features. There are two kinds of platforms that can be used to build an app, Hybrid or Cross platforms and Native platforms.
Hybrid and Native technologies have their own pros and cons although it is still debatable which framework is better. Businesses fail to take an apt decision when it comes to Mobile App Development as it is difficult to determine which technology is better or suits their needs. If the budget and time are constraints for you Hybrid Apps may be a better choice. Hybrid Apps are multi-platform apps developed using Cross Compatible technology. Developing an app using Hybrid technology requires lesser time as there is no need to develop separate codes for different Operating Systems.