

Mashable. 6 Google Secret URLs that You Didn’t Know About.
5 Disposable Web Accounts to Keep Your Identity Safe. Identity theft is on the rise.
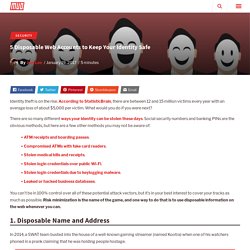
According to StatisticBrain, there are between 12 and 15 million victims every year with an average loss of about $5,000 per victim. Default Router Passwords - The internets most comprehensive router password database. How to Set Up Your Own Home VPN Server. Virtual Private Networks (VPNs) are very useful, whether you’re traveling the world or just using public Wi-Fi at a coffee shop in your hometown.
But you don’t necessarily have to pay for a VPN service—you could host your own VPN server at home. Your home Internet connection’s upload speed will really matter here. What are some tech hacks that can be learned in 10 minutes? - Quora. Jeffrey Friedl's Image Metadata Viewer. If you have questions about this tool, please see the FAQ.
WeTransfer. Ninite - Install or Update Multiple Apps at Once. Automatic Face Detection in Photos with PHP – Corpocrat Magazine. I have always wondered how to detect faces automatically with php script.
I have seen in many photo sharing and social network sites automatically detect a face and tag a name after being uploaded. In this article, i will explain how possible this task can be achieved with simplicity with OpenCV and PHP Facedetect extension. Top 10 Password Cracking Tools for all Platforms. A simple details about password cracking tools from wiki.
In cryptanalysis and computer security, password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system. A common approach (brute-force attack) is to try guesses repeatedly for the password and check them against an available cryptographic hash of the password. Learn How to Pop Your First Lock. Old versions of Windows, Mac and Linux Software, Apps & Abandonware Games - Download at OldVersion.com. How to Bypass and Reset the Password on Every Operating System.
Passwords can be reset or bypassed on every operating system.
On Windows, Linux, and Mac OS X, you can gain access to a computer’s unencrypted files after resetting the password — the password doesn’t actually prevent access to your files. On other devices where you can’t gain access to the files, you can still reset the device and gain access to it without knowing a password. These tricks all require physical access to the device. Windows. Turn an Old Computer Into a Do-Anything Home Server with FreeNAS 8.
6 links that will show you what Google knows about you. Windows 10 defaults to keylogging, harvesting browser history, purchases, and covert listening. By default, Microsoft gets to see your location, keystrokes and browser history -- and listen to your microphone, and some of that stuff is shared with "trusted [by Microsoft, not by you] partners.

" You can turn this all off, of course, by digging through screen after screen of "privacy" dashboards, navigating the welter of tickboxes that serve the same purposes as all those clean, ration-seeming lines on the craps table: to complexify the proposition so you can't figure out if the odds are in your favor. Six Great DIY Projects for Hacking Computers and Networks. Roll Your Own Anonymizing Tor Proxy with a Raspberry Pi. Visual Cryptography. The technique I’m going to describe is attributed to two great mathematicians: Moni Naor and Adi Shamir, in 1994.
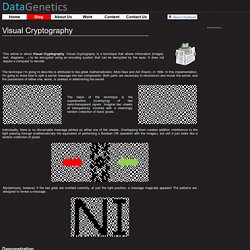
In this implementation, I'm going to show how to split a secret message into two components. Both parts are necessary to reconstruct and reveal the secret, and the possession of either one, alone, is useless in determining the secret. Individually, there is no discernable message printed on either one of the sheets. Overlapping them creates addition interference to the light passing through (mathematically the equivalent of performing a Boolean OR operation with the images), but still it just looks like a random collection of pixels. Demonstration Let’s look at couple of examples of this in action, then we’ll describe how the technique works. Below you will see two random looking rectangles of dots. To give you feedback, once the images are perfectly aligned, the advance button will go blank with a red border (don’t worry, your computer will not self-destruct in five seconds)
PhotoRec. Latest stable version 7.0 April 18, 2015 PhotoRec, Digital Picture and File Recovery PhotoRec is file data recovery software designed to recover lost files including video, documents and archives from hard disks, CD-ROMs, and lost pictures (thus the Photo Recovery name) from digital camera memory.
PhotoRec ignores the file system and goes after the underlying data, so it will still work even if your media's file system has been severely damaged or reformatted. Hola - Free VPN, Secure Browsing, Unrestricted Access. Www.unix-ninja. In this article I am going to share some bash scripting commands and regular expressions which I find useful in password cracking.
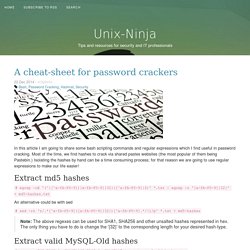
Most of the time, we find hashes to crack via shared pastes websites (the most popular of them being Pastebin.) Develop-photographic-memory. Here is an interesting technique that one can work with to develop a more photographic memory. Tools such as this can offer pathways to better understanding your own consciousness of for developing deeper levels of awareness and mindfulness. Everyone wants to remember everything all the time, reach into the sciences behind it all. Things You’ll Need A dark room.A bright lamp.A sheet of paper with a rectangular hole cut the size of a paragraph for the text you want to “photograph”. Instructions. Carlcheo. Johnnylists. Login2. It's simple! This service is made for you to save your time on registration for many sites. You can not register at all sites, so just type the name of site for which you need to enter login and password and click «Get».
Tips: Our project is constantly developing and we try to keep our database in actual state, use more of our services. 6-links-that-will-show-you-what-google. Want to find out all the things Google knows about you? Here are 6 links that will show you some of the data Google has about you. 1. Find out how Google sees you Google attempts to create a basic profile of you, your age, gender, interests. Dpl. Merabheja. Below is a list of one of the best hidden 101 Computer tips and tricks to impress your friends which you have been unaware of so far in life. 4 Ways to Crack a Facebook Password and How to Protect Yourself from Them. Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.
We share our lives on Facebook. We share our birthdays and our anniversaries. We share our vacation plans and locations. We share the births of our sons and the deaths of our fathers. But we sometimes forget who's watching. We use Facebook as a tool to connect, but there are those people who use that connectivity for malicious purposes. Null-byte.wonderhowto. Hack Like a Pro: How to Spy on Anyone, Part 1 (Hacking Computers) Welcome back, my rookie hackers!
Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too. In this brand new series, we will explore how we can use the ubiquity of the computer to peek in on just about anyone and anyplace. Unlike the spy movies of yesteryear where the spy had to place a listening device in the lamp or in a houseplant, as long as there is a computer in the room, it can be used as a "bug. " We will examine how to turn that commonplace computer into our own bug to listen in on conversations, use as a spy camera, track Internet searches, and more. Www.howtogeek. Just about any self respecting geek always has a flash drive handy. Password_sniffer. Related Links. Lifehacker. Infographicjournal. Wpengine. Who is the first superhero that comes to mind?
Www.cometdocs. Lifehacker. Geekyprojects. Www.howtogeek. Smallpdf. Fakena. Www.howtogeek. Photo by Benjamin Gustafsson Anytime you’re making connections to anything outside of your network, security should be a concern, and this is doubly true for users of BitTorrent, who are getting data from all sorts of unknown sources. Www.howtogeek. Crack a Combination Bike Lock in Under 30 Seconds. How to Hide Files in JPEG Pictures. 64 Things Every Geek Should Know. If you consider yourself a geek, or aspire to the honor of geekhood, here’s an essential checklist of must-have geek skills.
The term ‘geek’, once used to label a circus freak, has morphed in meaning over the years. USB password stealer. Hack Any Password Protected Wi-Fi Network Unlimited Free Internet Free Download. Password Secrets of Popular Windows Applications. Top 10 Ways to Break Into and Out of Almost Anything.
Ninite - Install or Update Multiple Apps at Once. How To Crack A Wi-Fi Network's WPA Password With Reaver. How to Crack the Account Password on Any Operating System. How Secure Is My Password? Encryption. Web-site hacks.