

Terms of Service; Didn't Read. How to easily delete your online accounts. Spring Financial is a finance company based in Canada.
The company was founded in 2014. Spring Financial is a subsidiary of Canada Drives, which is a leading auto financing company in Canada. The Chief Executive Officer is Michael Galpin. The Director is Cody Green. The Customer Relations Manager is Laura Marchand. Upon loan approval, the funds will go into a secure trust account. Canceling your loan is simple. Opt Out From Online Behavioral Advertising By Participating Companies (BETA) OFF Pocket™ - Privacy Case for Mobile Phones by Adam Harvey. A Girl Who Codes. Nikita Rau is a high school senior and, at this moment, drinking applekiwi-strawberry juice out of a plastic cup.
We're in the cafeteria of Bronx High School of Science, in New York. The noise level is high--too high for older ears--but the kids seem excited. Or maybe frenzied would be a better word. It's around 3:30 p.m. on the second Monday of the new school year, otherwise known as club-fair day. Sipping her juice, Rau moves to straighten a pile of brochures for XX Hackers, the computer-coding club she started last year. Girls (Who Code) Rule The World. In a conference room on the ninth floor of the futuristic-looking IAC building on Manhattan's far West Side, a hive of teenage girls were buzzing in conversation recently.
But they weren't talking about fashion or Justin Bieber. Instead, if you listen in, you'd overhear snippets like this: "My interest is robotics--I'm curious how a stoplight or an ATM works," said Martha Ghose, a Bangladeshi girl from Manhattan, or, "I want to create new medical devices," said Sondos Alnajjar from Jordan. These are Girls Who Code and their newest friends, the TechGirls. Girls Who Code is an eight-week summer enrichment and mentoring program for teenage girls interested in web design, robotics, and mobile development. The program was started in New York City and is happening in six cities this summer.
Some of the TechGirls are wearing hijabs, while others are dressed more secularly. Minimize request overhead - Make the Web Faster. Every time a client sends an HTTP request, it has to send all associated cookies that have been set for that domain and path along with it.
ULPS Configuration Utility. [C] // This is a quick analysis of Linux's use of RDRAND. All double-slash (//) // Introducing Blue Pill. All the current rootkits and backdoors, which I am aware of, are based on a concept.
For example: FU was based on an idea of unlinking EPROCESS blocks from the kernel list of active processes, Shadow Walker was based on a concept of hooking the page fault handler and marking some pages as invalid, deepdoor on changing some fields in NDIS data structure, etc... Once you know the concept you can (at least theoretically) detect the given rootkit. Now, imagine a malware (e.g. a network backdoor, keylogger, etc...) whose capabilities to remain undetectable do not rely on obscurity of the concept. Does Pixel Size Matter. By Roger N.
Clark All images, text and data on this site are copyrighted. Simple Urban Internet. NitruxSA/flattr-icons. DisplayFusion: Multiple Monitors Made Easy! A Beginner’s Guide to Big O Notation « Rob Bell. Big O notation is used in Computer Science to describe the performance or complexity of an algorithm.

Big O specifically describes the worst-case scenario, and can be used to describe the execution time required or the space used (e.g. in memory or on disk) by an algorithm. Anyone who’s read Programming Pearls or any other Computer Science books and doesn’t have a grounding in Mathematics will have hit a wall when they reached chapters that mention O(N log N) or other seemingly crazy syntax. Hopefully this article will help you gain an understanding of the basics of Big O and Logarithms. As a programmer first and a mathematician second (or maybe third or fourth) I found the best way to understand Big O thoroughly was to produce some examples in code. So, below are some common orders of growth along with descriptions and examples where possible. O(1) describes an algorithm that will always execute in the same time (or space) regardless of the size of the input data set. AntLion Audio — All Products. Security Group Claims to Have Subverted Google Chrome’s Sandbox. A French security research firm boasted today that it has discovered a two-step process for defeating Google Chrome‘s sandbox, the security technology designed to protect the browser from being compromised by previously unknown security flaws.

Experts say the discovery, if true, marks the first time hackers have figured out a way around the vaunted security layer, and almost certainly will encourage attackers to devise similar methods of subverting this technology in Chrome and other widely used software. In an advisory released today, VUPEN Security said: “We are (un)happy to announce that we have official Pwnd Google Chrome and its sandbox.” The post includes a video showing the exploitation of what VUPEN claims is a previously undocumented security hole in Chrome v.11.0.696.65 on Microsoft Windows 7 SP1 (x64). Google spokesman Jay Nancarrow said the company was unable to verify VUPEN’s claims, because VUPEN hadn’t shared any information about their findings. Dvorak keyboard training. List of Printers Which Do or Do Not Display Tracking Dots. Introduction This is a list in progress of color laser printer models that do or do not print yellow tracking dots on their output.
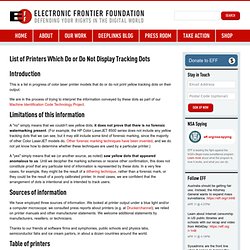
We are in the process of trying to interpret the information conveyed by these dots as part of our Machine Identification Code Technology Project. Downloads / SATA & SAS / WD RE2-GP. Downloads Support by Country RE2GP Idle Mode Update Utility Description This firmware modifies the behavior of the drive to wait longer before positioning the heads in their park position and turning off unnecessary electronics.
Android Rice /g/uide. So, if Android is so modular, why do we need to run a special version of it? The answer lies in just how open Android really is. Android allows OEMs (Phone manufacturers like HTC and Samsung) to personalize it to their own taste, and in most situations, these OEMs lock down the experience to what they want it to be like. Because of this, many community developers band together and create special ROMs (usually referring to an entire picture of an operating system that gets saved to a special area called Read-Only Memory, where they get their name from), which are basically custom versions of Google's AOSP code.
They create drivers for phones so that these ROMs can run on these phones, and teach users how to install them. Logitech HQ: François Morier, Senior Engineer Explains Mouse Sensor Design. Computer Stupidities. Worthless information about your worthless mouse. Your mouse's polling rate determines how often it sends data to your operating system. All mouse movements (counts) and button presses must wait in the mouse until windows polls for them. By default, windows will poll a usb mouse every 8 milliseconds (125hz). You can increase the frequency of polling with a number of programs/drivers/registry fixes. All this does is reduce the delay of sending the mouse data to the operating system. This has no effect on your sensitivity, but it will increase cpu usage. Bugmenot.com - login with these free web passwords to bypass compulsory registration. SHODAN - Computer Search Engine.
ShieldsUP! — Internet Vulnerability Profiling. Your Internet connection's IP address is uniquely associated with the following "machine name": The string of text above is known as your Internet connection's "reverse DNS. " The end of the string is probably a domain name related to your ISP. This will be common to all customers of this ISP. But the beginning of the string uniquely identifies your Internet connection. The question is: Is the beginning of the string an "account ID" that is uniquely and permanently tied to you, or is it merely related to your current public IP address and thus subject to change?
The Sith Lords Restored Content Mod (TSLRCM) for Star Wars: Knights of the Old Republic II. NewDark - Thief 2 V1.19 & System Shock 2 V2.4. Chromium Notes: The story of Iron. Update from 2013: this post was written in 2009. While the statements it made about Chrome were true then, Chrome today is a much different project. Iron claims to be a "privacy-oriented" fork of Chrome, which removes a bunch of pieces that the Iron author claims are privacy invasive. In the abstract this is a thing I'd support -- nothing like some publicity to put pressure on the project to be more careful about user privacy -- but when you look at the details it kinda falls down.
JDS Labs - O2+ODAC Combo. JDS Labs - Objective2 Headphone Amplifier. VPNs: Is it OK to Monitor ‘Bad’ Users on Ethical Grounds? When signing up to a VPN provider many users hope that they can use those services in complete privacy, free from the prying eyes of their ISP, aggressive governments and commercially motivated corporations. There are many different VPN providers to choose from and endless configuration, pricing and location issues to consider. Those aside, current attitudes suggest that going with one that claims a zero logging policy, where it’s impossible to link any activity with a particular user, is a good starting point for a selection.
Proxy.sh is one such provider, but last weekend the company openly announced that it would install the Wireshark network monitoring tool on one of its servers in order to identify an individual who had been accused of harassing someone’s daughter. Surprised that the company would do so without a court order, on Monday TorrentFreak published an article on the topic. Can You Trust Your VPN Provider…? The privacy of Internet users has become an extremely hot topic this year, largely thanks to the revelations of whistleblower Edward Snowden. As a result many people have turned to VPNs in the hope of making their online browsing habits harder to track. VPN Services That Take Your Anonymity Seriously, 2013 Edition. AMD Bulldozer and Piledriver Overclocking Guide - Asus Motherboard. FSB & MISC Overclocking Section. Bulldozer Overclocking Guide (Performance Scaling Charts, max OCs)LN2 Results coming! Bulldozer OC Guide! Everything you need to overclock bulldozer properly. Logical Increments - Peripherals Buying Guide.
Mindplar. Eyefinity Setup Guide - Radeon - Graphics & Displays. WASD Keyboards: Custom Mechanical Keyboards. Android Asset Studio - Device Frame Generator. Linux - Why do game developers prefer Windows. How a RAM disk saved my life. How To Turn Your Nintendo DS Into a Retro Game Machine. Have Your Accounts Been Compromised? KittyKatt/screenFetch. CMDFetch~ Guides. Bitfenix Alchemy Multisleeve 24-Pin ATX Extension Cable - 30cm - White (BFA-MSC-24ATX45WK-RP) Part of the Bitfenix Alchemy Premium Modding Series, this series of multisleeved cables brings together the highest quality materials and craftsmanship for the discerning modding enthusiasts.
With input from some of the world's most prolific case modders, BitFenix Alchemy Multisleeved Cables offer a premium ultra-dense weave and a unique multisleeved construction for an unparalleled look. These premium cables feature precision molded connectors, and come in a variety of colors and cable types, enabling modders to transform normal PCs into objects of wonderment.
How To Ask Questions The Smart Way. In the world of hackers, the kind of answers you get to your technical questions depends as much on the way you ask the questions as on the difficulty of developing the answer. This guide will teach you how to ask questions in a way more likely to get you a satisfactory answer. GNU/Linux Ricing - /g/ Technology Wiki. GNU/Linux distributions are well known for their ability to customize the way they work to a large degree. The purpose of this page is to give the reader some ideas on what can be customized and how. Mice - /g/ Technology Wiki. Anonymising Yourself - /g/ Technology Wiki. XTY Operator Style Earbud Microphone Set. CODE Mechanical Keyboard. DNS Nameserver Spoofability Test. Ninite - Install or Update Multiple Apps at Once. HTTP vs HTTPS performance. Php - What does it mean to escape a string. PHP Security - Sanitize & Clean.
Operators - Reference - What does this symbol mean in PHP. In The Shadows mod for Quake. Mplayer2. GNU/Linux Ricing - /g/ Technology. KCP - Kawaii Codec Pack. Logical Increments - PC Buying Guide. Still trust DuckDuckGo? [root] Triangle Away. Aporia ALPHA v1.0 download - Aporia: Uncover the Mystery Game. Intel Core i7-3770K, Gigabyte GeForce GTX 680, Cooler Master HAF 922 - System Build. Mac to School - Education Mac Purchasing, Refurbishment & Sales. How to - USBTUX - Waterfox. Madness and Obsession on the Electronic Frontier. Deus Ex: Human Revolution.
Deus Ex – Human Revolution: Computer Usernames and Passwords. 4walled. Pwnie Express. G35 Surround Sound Headset. Meshmoon. Vuze: The most powerful bittorrent app on earth. Deluge BitTorrent Client. The libTorrent and rTorrent Project. Whatbox. Ipredator - Surf anonymously with VPN and proxy. AMD VISION Premium Quad Core Barebone PC - MSI 760GM-P33 Motherboard, AMD Phenom II X4 840 Quad Core CPU, ATI Radeon HD 5450 1GB, Cooler Master Elite 310 Mid-Tower Case, 350 Watt Power Supply at TigerDirect. Netgear Rangemax WNDR3700. The Ultimate Router Battle. Computer Parts, PC Components, Laptop Computers, LED LCD TV, Digital Cameras and more!
LG M2280D-PU 21.5" 1920 x 1080p 5ms Full HD LED Backlight TV Monitor w/DTV Tuner 250cd/m2 DC 5,000,000:1. ASUS VW246H Glossy Black 24" 2ms(GTG) HDMI Widescreen LCD Monitor 300 cd/m2 ASCR 20000:1 (1000:1) Built-in Speakers. ASUS VH236H Black 23" 2ms Full HD Widescreen LCD Monitor w/ Speakers 300 cd/m2 20000 :1 (ASCR) Acer G235HAbd 23'' 5ms 1920x1080 WideScreen LCD monitor 300 cd/m2 1000:1. Acer P215HBbd Black 21.5" 5ms Full HD WideScreen LCD Monitor 300 cd/m2 ACM 50,000:1 (1,000:1) Thermaltake Element G VL10001W2Z Black ATX Mid Tower Computer Case. Thermaltake Element G Mid Tower Case at CircuitCity.com. G.SKILL Ripjaws Series 4GB (2 x 2GB) 240-Pin DDR3 SDRAM DDR3 1600 (PC3 12800) Desktop Memory Model F3-12800CL9D-4GBRL. AMD Phenom II X6 1075T Thuban 3.0GHz 6 x 512KB L2 Cache 6MB L3 Cache Socket AM3 125W Six-Core Desktop Processor HDT75TFBGRBOX.
OCZ ModXStream Pro 700W Modular High Performance Power Supply compatible with Intel Sandybridge Core i3 i5 i7 and AMD Phenom. ASUS M4A88T-V EVO/USB3 AM3 AMD 880G HDMI USB 3.0 ATX AMD Motherboard.