

Fedora software management tool. Receta para evitar el espionaje: software libre y cifrado. A no ser que acabes de salir de una cueva, tienes que saber si o si qué es PRISM, el programa de ciberespionaje masivo que estaría llevando a cabo la Agencia Nacional de Seguridad estadounidense (NSA por sus siglas en inglés) en colaboración con las principales tecnológicas patrias.

Eso es al menos a lo que apuntan todos los indicios, ya que tanto Google, Microsoft, Facebook, Apple y el resto de firmas involucradas niegan tajantemente tal participación. ISODisk, free software for mount and create ISO disk image. BitTorrent Sync 2.0, sincronización segura de archivos sin nube. Disponible LibreOffice 5, más potente que nunca. Los lenguajes de programación abiertos copan GitHub. Los responsables de la forja de software más popular del momento han publicado una gráfica que muestra las tendencias en cuanto a los lenguajes de programación utilizados.

Una gráfica que contempla desde el lanzamiento del sitio en 2008 hasta este 2015 y cuyo denominador común es el Open Source. Como se sabe, GitHub se basa en el software de control de versiones Git, creado por Linus Torvalds para gestionar mejor las actualizaciones del kernel Linux y extendido al mundo en forma de plataforma para desarrolladores que triunfa como ninguna otra: en 2010 ya albergaba mas de un millón de proyectos, en 2013 superó los diez millones y el pasado junio la compañía salía a buscar financiación con una valoración de mercado de 2.000 millones de dólares. Una buena estampa de cómo ha discurrido el mundillo de la programación en los últimos tiempos. ¿Qué tal se comporta realmente Btrfs? Released darktable 1.6.8. We are happy to announce that darktable 1.6.8 has been released.
The release notes and relevant downloads can be found attached to this git tag: Please only use our provided packages ("darktable-1.6.8. *" tar.xz and dmg) not the auto-created tarballs from github ("Source code", zip and tar.gz). The latter are just git snapshots and will not work! Docker knows how to win over developers and sysadmins. The use of Docker as an application container management system has become standard practice for developers and systems engineers in the space of just two years.

Some like to say that haven’t seen such a technological advance since OpenSSH. Docker is now a major player and is widely used in cloud systems architectures. But more than just that: Docker knows how to win developers over. Let's take a look at an overview of what we’ve done with Docker, as well as an assessment of the future and of the competition that is appearing on the horizon. 5 videos to help you learn about Docker. When you're interested in learning a new technology, sometimes the best way is to watch it in action—or at the very least, to have someone explain it one-on-one.
Success of Vagrant, Docker, and Ansible. The complexity of application stacks keeps going up.
Way, way up. Application stacks have always been complicated, but never like this. There are so many services, so many tools, so much more compute power available, so many new techniques to try, and always the desire, and the pressure, to solve problems in newer and cooler and more elegant ways. View the installed drivers list on Windows operating system. Description InstalledDriversList is a simple tool for Windows that lists all device drivers that are currently installed on your system.
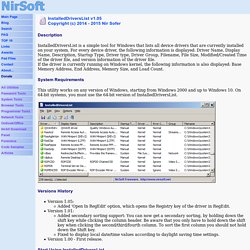
For every device driver, the following information is displayed: Driver Name, Display Name, Description, Startup Type, Driver type, Driver Group, Filename, File Size, Modified/Created Time of the driver file, and version information of the driver file. If the driver is currently running on Windows kernel, the following information is also displayed: Base Memory Address, End Address, Memory Size, and Load Count.
System Requirements This utility works on any version of Windows, starting from Windows 2000 and up to Windows 10. Versions History. Disponible darktable 1.6.8. Distros de seguridad [Aporte] : Seguridad. Virtual Appliances Quick Start Guide - Bitnami documentation. Bitnami Virtual Machine Images, also known as virtual appliances, contain a minimal Linux operating system and a fully installed and configured Bitnami application Stack.
This allows you to run the application without actually installing it on your computer’s operating system. Using a virtualization platform, you can simply start and stop the Bitnami Virtual Machine Image whenever you want to use the application. This allows you to keep it completely isolated from software installed on your machine. After you download and extract a Bitnami Virtual Machine Image (the file is compressed to reduce the download size), it will be ready to be deployed in your virtualization infrastructure. How to Find The Best Wi-Fi Channel For Your Router on Any Operating System.
Choosing the best Wi-Fi channel on your router helps to reduce interference and improve your WI-Fi signal.
These tools will help you identify the least congested Wi-Fi channel in your area. Wi-Fi channels overlap with nearby channels. Channels 1, 6, and 11 are the most frequently used for 2.4 GHz Wi-Fi. How to Access FTP and WebDAV Sites in Any Operating System’s File Manager. You don’t need third-party software to access FTP servers, WebDAV sites, and other remote files shares.
Popular desktop operating systems like Windows, Mac, and Linux can all do this out-of-the-box. You can also access files stored on servers using the NFS, Windows file sharing (SMB), and SSH protocols. Different operating systems support different protocols. Windows Windows Explorer has built-in FTP support — in fact, this was the centerpiece of our guide to downloading Firefox without ever opening Internet Explorer on a new Windows installation. To access a remote server, you can simply plug its address into the location box using the appropriate protocol. Nginx - Bitnami documentation. NGinx is a free, open-source, high-performance HTTP server and reverse proxy, as well as an IMAP/POP3 proxy server. Currently Ruby Stack includes this server already configured. Quick reference card How to start the Nginx server?
You can find the Nginx server in your installation directory. If you are using the Virtual Machine or the Cloud Image check the /opt/bitnami folder. Mapping URLs to Filesystem Locations - Apache HTTP Server Version 2.2. This document explains how Apache uses the URL of a request to determine the filesystem location from which to serve a file.
DocumentRoot In deciding what file to serve for a given request, Apache's default behavior is to take the URL-Path for the request (the part of the URL following the hostname and port) and add it to the end of the DocumentRoot specified in your configuration files. Therefore, the files and directories underneath the DocumentRoot make up the basic document tree which will be visible from the web. Abuso de permisos: Caso Tigo Shop ¿Spyware de la telefónica? Hace un buen tiempo que estaba queriendo retomar el blog con artículos referentes a seguridad de la información, sobre todo con algunos sucesos de suplantación de identidad ocurridos la semana pasada (Mal llamado "hackeos" por la prensa) pero ese tema prefiero dejarlo para otro post debido a algo que surgió el día de ayer.