

The Assistance and Access Bill 2018. Encryption and other forms of electronic protection are vital security measures that protect private, commercial and Government data and make the communications and devices of all people more secure.
However, these security measures are also being employed by terrorists, child sex offenders and criminal organisations to mask illegal conduct. The exploitation of modern communications technology for illicit ends is a significant obstacle to the lawful access of communications by Australia’s law enforcement and national security agencies. To address these threats, the Government has developed the Assistance and Access Bill to secure critical assistance from the communications industry and enable law enforcement to effectively investigate serious crimes in the digital era.
Public submissions on the exposure draft Assistance and Access Bill have now closed. An amended Bill is now before the Parliament. The challenges posed by encryption Key elements. New York City's WiFi Hotspots Confirmed As Surveillance and Tracking Devices. By Kevin Samson Back in early 2016 I wrote about a plan for New York City to turn 7,500 payphones into WiFi hotspots.
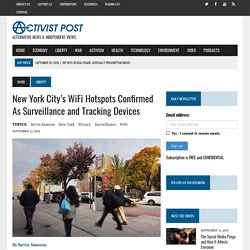
The program was called LinkNYC and indeed has begun its rollout with more than 1,500 now online. At the time, I raised some of the health concerns surrounding the implementation of a grid that would enhance the public’s exposure to electromagnetic radiation (without their consent of course). However, I also cautioned about issues of privacy and the potential for pervasive surveillance through these structures. Google tracks users who turn off location history. Image copyright Getty Images Google records users' locations even when they have asked it not to, a report from the Associated Press has suggested.
The issue could affect up to two billion Android and Apple devices which use Google for maps or search. The study, verified by researchers at Princeton University, has angered US law-makers. Australian Gov't Scooped Up Tons Of Cell Site Location Data To Track Citizens' Movements. Forensic Extraction. Secret messages hidden in TV adverts can order smartphones to spy on people, researchers warn. The Secret Surveillance Catalogue. Government Cellphone Surveillance Catalogue. Privacy: Google's Android HTC mobile phone 'transmits user locations back to company'
By Daily Mail Reporter Updated: 20:01 GMT, 22 April 2011 Google's Android HTC phone transmitted data back to Google several times an hourApple slammed for user locations being stored in iPhone and iPadGoogle and Apple are using location data to build databases of Wi-Fi hotspotsData from Apple devices syncs with computer, meaning anyone with access can see Representative Edward Markey questions whether the practice may be illegal Tests: An Android HTC phone was found to track its location every few seconds and transmitted the data back to Google several times an hour The row over the privacy of mobile phone users escalated today as it was revealed that Google devices regularly transmit user locations back to the company.
The new revelations come after Apple was this week slammed by several Congress members for the way user locations are being stored in unencrypted databases on the iPhone and iPad, sometimes stretching back several months. You've Been Warned: Spotify Wants To Spy On You In Every Way Imaginable. Bugged, Tracked, Hacked. It’s impossible to imagine life without smartphones.
Everything about our lives can now be contained in the palm of our hand. Personal details, professional contacts, banking details, photos, medical data, it’s all there, so you’d expect your smartphone to be secure. But in this special investigation Ross Coulthart discovers, we are facing the biggest threat to our privacy that the world has ever seen. Apple Has Quietly Started Tracking iPhone Users Again, And It's Tricky To Opt Out. Photo: Flickr/pasukaru76 Apple’s launch of the iPhone 5 in September came with a bunch of new commercials to promote the device.But Apple didn’t shout quite so loud about an enhancement to its new mobile operating system, iOS 6, which also occurred in September: The company has started tracking users so that advertisers can target them again, through a new tracking technology called IFA or IDFA.
Previously, Apple had all but disabled tracking of iPhone users by advertisers when it stopped app developers from utilising Apple mobile device data via UDID, the unique, permanent, non-deletable serial number that previously identified every Apple device. NSA Tests Out Smartphones that Recognize Handwriting Motion. The NSA Has Inserted Its Code Into Android OS, Or Three Quarters Of All Smartphones. Over a decade ago, it was discovered that the NSA embedded backdoor access into Windows 95, and likely into virtually all other subsequent internet connected, desktop-based operating systems.

However, with the passage of time, more and more people went "mobile", and as a result the NSA had to adapt. Snowden says Australia watching its citizens ‘all the time,’ slams new metadata laws — RT News. EFF Files FOIA Suit Over U.S. Marshals’ Spy Planes. San Francisco - The Electronic Frontier Foundation (EFF) today filed a Freedom of Information Act (FOIA) lawsuit to shine light on the U.S.

Marshals Service's (USMS) use of small aircraft mounted with controversial cell-phone tracking systems. The Wall Street Journal revealed last year that the Marshals have been flying small, fixed-wing Cessna planes mounted with IMSI catchers—devices that emulate cell phone towers and are able to capture the locational data of tens of thousands of cell phones during a single flight. The planes—in the air since 2007—reportedly were based out of five metropolitan airports and shared by multiple agencies within the U.S.
Smartphone Users Tracked by Apps an Average of every Three Minutes. Using a smartphone can mean revealing your whereabouts nearly all the time, according to new research performed by computer scientists at Carnegie Mellon University.
Working with nearly two dozen smartphone owners using the Android operating system over a two-week period, researchers found some apps collected GPS data from those phones an average of every three minutes. The average was calculated after the computer scientists found that about a dozen or so Android apps gathered GPS data 6,200 times per study participant during the two weeks. Some of the apps mentioned in the study include The Weather Channel, which collected GPS data every 10 minutes. Another app, Groupon, requested a smartphone owner’s coordinates 1,062 times in two weeks. Telcos face mass SIM card recall after spy agencies' encryption hack revealed.
The SIM cards of Telstra, Vodafone and Optus may be compromised.
FBI taps cell phone mic as eavesdropping tool. The FBI appears to have begun using a novel form of electronic surveillance in criminal investigations: remotely activating a mobile phone's microphone and using it to eavesdrop on nearby conversations. The technique is called a "roving bug," and was approved by top U.S. Department of Justice officials for use against members of a New York organized crime family who were wary of conventional surveillance techniques such as tailing a suspect or wiretapping him. Nextel cell phones owned by two alleged mobsters, John Ardito and his attorney Peter Peluso, were used by the FBI to listen in on nearby conversations. Vodafone made millions helping GCHQ spy on the world. Facebook can gain direct access to your mobile and take pictures or make videos at any time, MPs warn.
Verizon Injecting Perma-Cookies to Track Mobile Customers, Bypassing Privacy Controls. Verizon users might want to start looking for another provider. In an effort to better serve advertisers, Verizon Wireless has been silently modifying its users' web traffic on its network to inject a cookie-like tracker. This tracker, included in an HTTP header called X-UIDH, is sent to every unencrypted website a Verizon customer visits from a mobile device.
It allows third-party advertisers and websites to assemble a deep, permanent profile of visitors' web browsing habits without their consent. Verizon apparently created this mechanism to expand their advertising programs, but it has privacy implications far beyond those programs. Vodafone reveals existence of secret wires that allow state surveillance. Vodafone, one of the world's largest mobile phone groups, has revealed the existence of secret wires that allow government agencies to listen to all conversations on its networks, saying they are widely used in some of the 29 countries in which it operates in Europe and beyond. The company has broken its silence on government surveillance in order to push back against the increasingly widespread use of phone and broadband networks to spy on citizens, and will publish its first Law Enforcement Disclosure Report on Friday.
At 40,000 words, it is the most comprehensive survey yet of how governments monitor the conversations and whereabouts of their people.
Mesh networks. Revealed: How governments can take control of smartphones. ‘Legal malware’ produced by the Italian firm Hacking Team can take total control of your mobile phone. Dozens of countries use Israeli spy technology to tap into global cell phone location databases. New app reveals how your smartphone can spy on you without permission (VIDEO) Google Maps Has Been Tracking Your Every Move, And There’s A Website To Prove It. Police scoop up data on thousands in mobile phone 'tower dumps' to track down criminals. Landmark Supreme Court Ruling: Police Need Warrant to Search Your Cellphone.
Researchers Find and Decode the Spy Tools Governments Use to Hijack Phones. Les and Dave Jacobs/Getty Newly uncovered components of a digital surveillance tool used by more than 60 governments worldwide provide a rare glimpse at the extensive ways law enforcement and intelligence agencies use the tool to surreptitiously record and steal data from mobile phones.