

Danger Room - What's Next in National Security. National Defense Magazine. Welcome to the National Security Agency - NSA/CSS. Cyber Warfare. US Iran Relations - History of US Iranian Relationship. Dawn of US-Iran Relations: Iran was once a powerful ally of the United States.
During the Cold War, the United States supported, in some cases "propped up," friendly governments as bulwarks against the Soviet Union. And in some of those cases the United States found itself supporting very unpopular, repressive regimes. The Shah of Iran falls into this category. His government was toppled in 1979 and was eventually replaced by another repressive regime... but this time the leadership was deeply anti-American.
Hostage Crisis: When Iranian revolutionaries took over the American Embassy in the Iran, many observers thought it would just be a a short protest... a symbolic act lasting for a few hours or a few days at most. USS Vincennes: Iran's Nuclear Dreams: Today, Iran is openly developing nuclear power capability. In a fall 2005 speech to students, Iran's president called for Israel to be wiped off the map. A 2007 U.S. government report said Iran halted its nuclear weapons program in 2003. The Fog of War – Eleven Lessons from the Life of Robert S. McNamara. The Fog of War is a film about the life and times of Robert S.
McNamara, the former Secretary of Defense under the Kennedy and Johnson administrations. The piece is a mix between historical footage and an interview with Robert McNamara by the director, Errol Morris. While allowing McNamara to tell the story from his perspective, Morris also divides the film into eleven lessons that can be taken away from McNamara’s life. What results is an inside look at one of the most important and controversial figures of 20th century American government. The film is also a candid look at the human side of the decision makers that run the United States and how their personalities can affect policy. Our Notes McNamara opens with the statement that while all military commanders make mistakes and try to learn from them, there will be no learning period with nuclear weapons.
Lesson #1: Empathize with your enemy. Lesson #2: Rationality alone will not save us. Lesson #3: There’s something beyond one’s self. OODA loop. Diagram of a decision cycle known as the Boyd cycle, or the OODA loop Overview[edit] The OODA loop has become an important concept in litigation,[1] business[2] and military strategy.
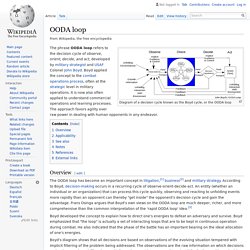
According to Boyd, decision-making occurs in a recurring cycle of observe-orient-decide-act. An entity (whether an individual or an organization) that can process this cycle quickly, observing and reacting to unfolding events more rapidly than an opponent can thereby "get inside" the opponent's decision cycle and gain the advantage. Frans Osinga argues that Boyd's own views on the OODA loop are much deeper, richer, and more comprehensive than the common interpretation of the 'rapid OODA loop' idea.[3] Boyd developed the concept to explain how to direct one's energies to defeat an adversary and survive. Boyd’s diagram shows that all decisions are based on observations of the evolving situation tempered with implicit filtering of the problem being addressed. Applicability[edit] See also[edit] Notes[edit] Identifying “Insider” Threats in Information Security. Introduction The threat of “insiders” in positions of trust with access to critical aspects of an organization’s Information Technology (IT) infrastructure, whether government, military, or private sector, to intentionally compromise and sabotage their secrets or proprietary information has become one of the paramount threats facing national security and critical infrastructure since the rise of the internet in the mid-1980s.
One reason for the increase in this threat is the massive and exponential explosion of availability of proprietary or classified information within organizations. A second key risk factor is the relative ease of access by “trusted” IT professionals who operate in these “secure” environments, ranging from data entry clerks to IT network administrators. To further exacerbate these risk factors, there is an emerging extremist ideology that all information, including an organization’s most secret and proprietary information, should be free and accessible to everyone.