

Batch file. The filename extension .bat is used in DOS and Windows.
Windows NT and OS/2 also added .cmd. Batch files for other environments may have different extensions, e.g. .btm in 4DOS, 4OS2 and 4NT related shells. The detailed handling of batch files has changed. Some of the detail in this article applies to all batch files while other details apply only to certain versions. Window (computing) Typical elements of a window (computing).
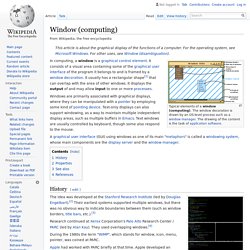
The window decoration is drawn by an OS-level process such as a window manager. The drawing of the content is the task of application software. Application Programming Interface for Windows. The Application Programming Interface for Windows (APIW) Standard is a specification of the Microsoft Windows 3.1 API drafted by Willows Software.
It is the successor to previously proposed Public Windows Interface standard. It was created in an attempt to establish a vendor-neutral, platform-independent, open standard of the 16-bit Windows API not controlled by Microsoft.[1] History[edit] Solutions for heterogeneous environments[edit] By the end of 1990, Windows 3.0 was the top-selling software. Category:Programming tools for Windows.
DLR (Dynamic Language Runtime) .Net Programming Languages (dot net) List of Microsoft Windows application programming interfaces and frameworks. From Wikipedia, the free encyclopedia The following is a list of Microsoft APIs and frameworks.
APIs[edit] Resource (Windows) The Windows API provides for easy access to all applications resources.
Each resource has a type and a name, both being either numeric identifiers or strings. Windows has a set of predefined resource types: The programmer can also define custom data types in resources. Windows API. Window (Computing Concepts) Windows Forms. Architecture[edit] A Windows Forms application is an event-driven application supported by Microsoft's .NET Framework.
Unlike a batch program, it spends most of its time simply waiting for the user to do something, such as fill in a text box or click a button. Windows Forms provides access to native Windows User Interface Common Controls by wrapping the extant Windows API in managed code.[5] With the help of Windows Forms, the .NET Framework provides a more comprehensive abstraction above the Win32 API than Visual Basic or MFC did.[6] Features[edit] All visual elements in the Windows Forms class library derive from the Control class.
Windows Presentation Foundation. Windows Presentation Foundation (or WPF) is a graphical subsystem for rendering user interfaces in Windows-based applications by Microsoft.
WPF, previously known as "Avalon", was initially released as part of .NET Framework 3.0. Rather than relying on the older GDI subsystem, WPF uses DirectX. WPF attempts to provide a consistent programming model for building applications and separates the user interface from business logic. It resembles similar XML-oriented object models, such as those implemented in XUL and SVG. WPF employs XAML, an XML-based language, to define and link various interface elements.[1] WPF applications can be deployed as standalone desktop programs or hosted as an embedded object in a website.
Windows Programming. Introduction[edit] This book aims to be a comprehensive source for any developer who is interested in programming for the Windows platform.
It starts at the lowest level, with the Win32 API (C and VB Classic) and then goes over to MFC (C++). Beyond these basic sections, it will cover COM, and the creation of ActiveX modules from a variety of languages. Next, it delves into the Windows DDK, and talk about programming device drivers for Windows platform. Finally, it moves on to the highest-level programming tasks, including shell extensions, shell scripting, and finally ASP and WSH.
Other topics that will be discussed here are: Writing screen-savers, creating HTML help modules, and compiling DLL files. This book will focus on topics that are specific to Windows, and avoids general programming topics. The reader is assumed to have a previous knowledge of the programming languages involved. Table of Contents[edit] Windows Template Library. Overview[edit] WTL provides support for implementing various user interface elements, from frame and popup windows, to MDI, standard and common controls, common dialogs, property sheets and pages, GDI objects, and other common UI elements, such as scrollable windows, splitter windows, toolbars and command bars.
WTL's main objective is to deliver small and efficient code, close in size and speed to "straight" SDK programs while providing a higher-level and more flexible object model to developers. Other classes such as a string wrapper that is syntax-compatible with MFC's CString and some templated collections are also included. Most of the WTL API is a mirror of the standard Win32 calls, so the interface tends to be familiar to most Windows programmers. Although no official documentation from Microsoft exists, the WTL Documentation Project is attempting to create a comprehensive reference for the library.[1] The WTL is not supported by Microsoft Product Support Services. Licensing[edit] Shell Tools (Windows)
Winsock. In computing, the Windows Sockets API (WSA), which was later shortened to Winsock, is a technical specification that defines how Windows network software should access network services, especially TCP/IP.
It defines a standard interface between a Windows TCP/IP client application (such as an FTP client or a web browser) and the underlying TCP/IP protocol stack. The nomenclature is based on the Berkeley sockets API model used in BSD for communications between programs. Initially, all the participating developers resisted the shortening of the name to Winsock for a long time, since there was much confusion among users between the API and the DLL library file (winsock.dll) which only exposed the common WSA interfaces to applications above it. Users would commonly believe that only making sure the DLL file was present on a system would provide full TCP/IP protocol support. Background[edit] In particular, Microsoft did not offer support for the TCP/IP protocol stack at that time. Handle (computing) For the interactive method of resizing visual elements in a user interface, see Adjustment handles. Common resource handles are file descriptors, network sockets, database connections, process identifiers (PIDs), and job IDs.
Process IDs and job IDs are explicitly visible integers, while file descriptors and sockets (which are often implemented as a form of file descriptor) are represented as integers, but are typically considered opaque. In traditional implementations, file descriptors are indices into a (per-process) file descriptor table, thence a (system-wide) file table. A handle leak is a type of software bug that occurs when a computer program asks for a handle to a resource but does not free the handle when it is no longer used; this is a form of resource leak, similar to a memory leak for a pointer to memory.
For example, if a program wishes to read the system password file (/etc/passwd) in read/write mode (O_RDWR), it could try to open the file via the following call: Hooking. Hooking is used for many purposes, including debugging and extending functionality. Examples might include intercepting keyboard or mouse event messages before they reach an application, or intercepting operating system calls in order to monitor behavior or modify the function of an application or other component. It is also widely used in benchmarking programs, for example frame rate measuring in 3D games, where the output and input is done through hooking.
Hooking can also be used by malicious code. For example, rootkits, pieces of software that try to make themselves invisible by faking the output of API calls that would otherwise reveal their existence, often use hooking techniques.