

Larger Server Count. Discount VPN Providers. Privacy Tools - Encryption Against Global Mass Surveillance. You are being watched.
Private and state-sponsored organizations are monitoring and recording your online activities. privacytools.io provides knowledge and tools to protect your privacy against global mass surveillance. Language: 繁體中文 Español Deutsch Darknet: Tor, I2P, ZeroNet Over the last 16 months, as I've debated this issue around the world, every single time somebody has said to me, "I don't really worry about invasions of privacy because I don't have anything to hide.
" I always say the same thing to them. I get out a pen, I write down my email address. Read also: The UKUSA Agreement is an agreement between the United Kingdom, United States, Australia, Canada, and New Zealand to cooperatively collect, analyze, and share intelligence. Five Eyes 1. Nine Eyes 6. Fourteen Eyes 10. Why is it not recommended to choose a US based service? An example of this is Lavabit – a discontinued secure email service created by Ladar Levison. Related Information Warrant Canary Examples: Tor Browser Brave Wire.
SMTP Authentication - Wikipedia. SMTP Authentication, often abbreviated SMTP AUTH, is an extension of the Simple Mail Transfer Protocol whereby an SMTP client may log in using an authentication mechanism chosen among those supported by the SMTP server.
The authentication extension is mandatory for submission servers.[1] History[edit] John Gardiner Myers published the first draft of SMTP AUTH in 1995,[3] and it has been successively developed and discussed in the IETF along with mail submission protocol, Extended SMTP (ESMTP), and Simple Authentication and Security Layer (SASL). An older SASL mechanism for ESMTP authentication (ESMTPA) is CRAM-MD5, and uses of the MD5 algorithm in HMACs (hash-based message authentication codes) are still considered sound.[4] The Internet Mail Consortium (IMC) reported 55% of mail servers were open relays in 1998,[5] but less than 1% in 2002.[6] Role in the mail transport system[edit] Using a mail submission agent (MSA), generally on port 587, implies SMTP AUTH. Details[edit] What is Port 443? Why do SSL VPNs make use of it? - IT Answers. TrafficObfuscation – OpenVPN Community. Sometimes it's useful to obfuscate the fact that your traffic is generated by OpenVPN.
For example, if your ISP is blocking OpenVPN for some reason. This article describes various ways to obfuscate OpenVPN traffic so that it's not as easily detected and blocked. Most of the content here originates from this email thread. Additionally, for some reason this mail was not included in Gmane archives. This was suggested here. "My recent suggestion to someone regarding this was to use a static-key tunnel to encapsulate a second secure channel (either openvpn with TLS or ssh(1) as needed.) Obfsproxy is a Tor subproject. "However, the obfsproxy project sounds very interesting. This setup will start obfsproxy on your openvpn server, listening to the port 21194. Client side ¶ Add the following lines to your existing openvpn config file: Blowfish (cipher) - Wikipedia. Blowfish is a symmetric-key block cipher, designed in 1993 by Bruce Schneier and included in a large number of cipher suites and encryption products.
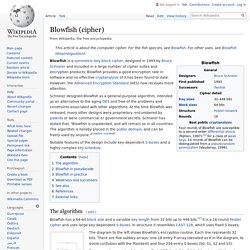
Blowfish provides a good encryption rate in software and no effective cryptanalysis of it has been found to date. However, the Advanced Encryption Standard (AES) now receives more attention. Schneier designed Blowfish as a general-purpose algorithm, intended as an alternative to the aging DES and free of the problems and constraints associated with other algorithms. At the time Blowfish was released, many other designs were proprietary, encumbered by patents or were commercial or government secrets. Schneier has stated that, "Blowfish is unpatented, and will remain so in all countries. Notable features of the design include key-dependent S-boxes and a highly complex key schedule. The Feistel structure of Blowfish The diagram to the left shows Blowfish's encryption routine. Blowfish has a memory footprint of just over 4 kilobytes of RAM. Best VPN Services in 2017 (Speed, Cost & Usability Reviews)
Proxy Tools. VPN Sort. VPN services. VPN (Virtual Private Network) VPN VLAN Tunnels etc. Networking (Engineering - Communication) Protocals, Communications & Signals.