

Cryptographic Module Validation Program. Logo of the Cryptographic Module Validation Program.
The Cryptographic Module Validation Program (CMVP) is a joint American and Canadian security accreditation program for cryptographic modules. The program is available to any vendors who seek to have their products certified for use by the U.S. Government and regulated industries (such as financial and health-care institutions) that collect, store, transfer, share and disseminate "sensitive, but not classified" information. All of the tests under the CMVP are handled by third-party laboratories that are accredited as Cryptographic Module Testing Laboratories by the National Voluntary Laboratory Accreditation Program (NVLAP). Product certifications under the CMVP are performed in accordance with the requirements of FIPS 140-2. The CMVP was established by the U.S. See also[edit] Comparison of cryptographic hash functions. Cryptographic hash function. A cryptographic hash function (specifically, SHA-1) at work.
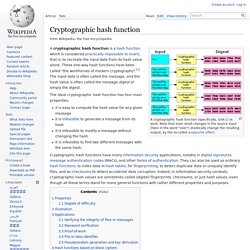
Note that even small changes in the source input (here in the word "over") drastically change the resulting output, by the so-called avalanche effect. A cryptographic hash function is a hash function which is considered practically impossible to invert, that is, to recreate the input data from its hash value alone. These one-way hash functions have been called "the workhorses of modern cryptography".[1] The input data is often called the message, and the hash value is often called the message digest or simply the digest. The ideal cryptographic hash function has four main properties: it is easy to compute the hash value for any given messageit is infeasible to generate a message from its hashit is infeasible to modify a message without changing the hashit is infeasible to find two different messages with the same hash.
§Properties[edit] A function meeting these criteria may still have undesirable properties. §Illustration[edit]
SHA-1. In cryptography, SHA-1 is a cryptographic hash function designed by the United States National Security Agency and is a U.S.
Federal Information Processing Standard published by the United States NIST.[2] SHA-1 produces a 160-bit (20-byte) hash value. A SHA-1 hash value is typically rendered as a hexadecimal number, 40 digits long. SHA stands for "secure hash algorithm". SHA-2. SHA-2 is a set of cryptographic hash functions (SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256) designed by the U.S.
National Security Agency (NSA) and published in 2001 by the NIST as a U.S. Federal Information Processing Standard (FIPS). SHA stands for Secure Hash Algorithm. National Institute of Standards and Technology. The National Institute of Standards and Technology (NIST), known between 1901 and 1988 as the National Bureau of Standards (NBS), is a measurement standards laboratory, also known as a National Metrological Institute (NMI), which is a non-regulatory agency of the United States Department of Commerce.
The institute's official mission is to:[1] Promote U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology in ways that enhance economic security and improve our quality of life. NIST had an operating budget for fiscal year 2007 (October 1, 2006-September 30, 2007) of about $843.3 million. NIST's 2009 budget was $992 million, and it also received $610 million as part of the American Recovery and Reinvestment Act.[2] NIST employs about 2,900 scientists, engineers, technicians, and support and administrative personnel. History[edit] Initial mandate[edit] History[edit] Metric system[edit] Organization[edit] Boulder Laboratories.
SHA-3. SHA-3, a subset of the cryptographic primitive family Keccak (/ˈkætʃæk/, or /kɛtʃɑːk/),[3][4] is a cryptographic hash function designed by Guido Bertoni, Joan Daemen, Michaël Peeters, and Gilles Van Assche, building upon RadioGatún.
Security Technology Related to Math. REF - Hash Algorithms. Hash Cracking. URI, Adressing, Distributed hashes, Watermarks and such.