

Blog. The past few days has seen an extensive discussion within the IT security industry about a cyberespionage campaign called Turla, aka Snake and Uroburos, which, according to G-DATA experts, may have been created by Russian special services.
One of the main conclusions also pointed out by research from BAE SYSTEMS, is a connection between the authors of Turla and those of another malicious program, known as Agent.BTZ, which infected the local networks of US military operations in the Middle East in 2008. We first became aware of this targeted campaign in March 2013. Hacker's Demo Shows How Easily Credit Cards Can Be Read Through Clothes And Wallets.
Scams - report the scam here. SpywareGuide.com - Spyware, Greynets, Privacy, Botnets, Rootkits, Security Resource. Java web applications security. XSS. Web-based applications have become more complex in the recent years as a result of this fact the variety and level of vulnerabilities have also increased significantly.
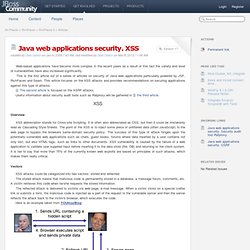
This is the first article out of a series of articles on security of Java web applications particularly powered by JSF, RichFaces and Seam. This article focuses on the XSS attacks and provides recommendations on securing applications against this type of attacks.