

Www.k-state.edu/its/security/training/mstraining/advanced.security.pdf. Class Work. Print server. Print servers may support a variety of industry-standard or proprietary printing protocols including Internet Printing Protocol, Line Printer Daemon protocol, NetWare, NetBIOS/NetBEUI, or JetDirect.
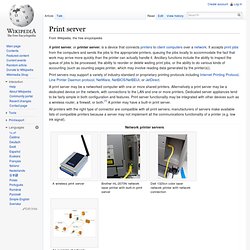
A print server may be a networked computer with one or more shared printers. Alternatively a print server may be a dedicated device on the network, with connections to the LAN and one or more printers. Dedicated server appliances tend to be fairly simple in both configuration and features. Print server functionality may be integrated with other devices such as a wireless router, a firewall, or both.[1] A printer may have a built-in print server. All printers with the right type of connector are compatible with all print servers; manufacturers of servers make available lists of compatible printers because a server may not implement all the communications functionality of a printer (e.g. low ink signal). Active Directory Server. Enabling IT to remain in control of corporate information IT must still remain in control of corporate information.

To manage a single identity for each user, across both on-premises and cloud-based (SaaS) applications, you can leverage Windows Server Active Directory, Microsoft Azure Active Directory (including Password Sync), and Active Directory Federation Services (AD FS). Enforce conditional access policies by defining the resources and level of access each user has to information and applications based on who they are, what they are accessing, and from which device, using the Web Application Proxy and AD FS. Active Directory. Directory service created by Microsoft for Windows domain networks A server running the Active Directory Domain Service (AD DS) role is called a domain controller.
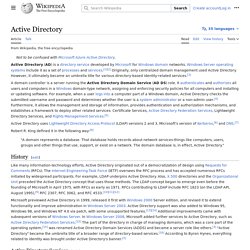
It authenticates and authorizes all users and computers in a Windows domain type network, assigning and enforcing security policies for all computers, and installing or updating software. For example, when a user logs into a computer that is part of a Windows domain, Active Directory checks the submitted password and determines whether the user is a system administrator or normal user.[4] Also, it allows management and storage of information, provides authentication and authorization mechanisms, and establishes a framework to deploy other related services: Certificate Services, Active Directory Federation Services, Lightweight Directory Services, and Rights Management Services.[5] History[edit] Like many information-technology efforts, originated out of a democratization of design using Request for Comments (RFCs).
Shortcut. The Basics of Windows Server 2008 FSRM (File Server Resource Manager) - Jose Barreto's Blog. Overview.

Assigning Delegated Print Administrator and Printer Permission Settings in Windows Server 2008 R2. Updated: September 24, 2009.
Controlling Service Security Using Windows Server 2008. If you would like to read the next part in this article series please go to Controlling Service Security Using Windows Server 2008 (Part 2).

Introduction Nearly every server that you have in your environment is running some sort of service. These services provide access to data, resources, applications, and other important areas of the server and network functionality. If these services are not protected, they become ideal candidates for an attacker. When a service is attacked, access to the server and potentially the network is at stake. Service Security Areas Services are inherently dangerous to your servers and network due to the fact that they provide holes in the server for users, applications, and other servers to access resources. When evaluating what needs to be protected, you need to look beyond the basic holes that are created and think about the potential attacks that can be performed against services and their related settings.
Security Enhancements Abound in Windows Server 2008. Six years ago, Microsoft chairman Bill Gates put security at the top of the agenda with the announcement of the company's Trustworthy Computing initiative. The fruits of this initiative are evident in Microsoft's Windows Server 2008, which is packed with new security features and enhancements straight out of the box. It's rarely wise to state that a new operating system is more secure than its predecessor because security flaws can take months to come to light after the software is released, but in the case of Windows Server 2008, we can say it with some confidence. That's because it shares the same code base as Windows Vista, which was released more than 18 months ago—so in effect the code is already tried and tested, and security patches to Vista have been incorporated into the Windows Server 2008 code. What is proxy server.
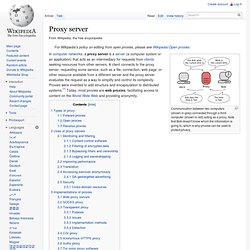
Proxy server. Communication between two computers (shown in grey) connected through a third computer (shown in red) acting as a proxy.
Note that Bob doesn't know whom the information is going to, which is why proxies can be used to protect privacy. Types of proxy[edit] A proxy server may reside on the user's local computer, or at various points between the user's computer and destination servers on the Internet. Forward proxies[edit] A forward proxy taking requests from an internal network and forwarding them to the Internet. Forward proxies are proxies in which the client server names the target server to connect to.[2] Forward proxies are able to retrieve from a wide range of sources (in most cases anywhere on the Internet). The terms "forward proxy" and "forwarding proxy" are a general description of behavior (forwarding traffic) and thus ambiguous.
Open proxies[edit]