

How To Become A Hacker. Copyright © 2001 Eric S.

Raymond As editor of the Jargon File and author of a few other well-known documents of similar nature, I often get email requests from enthusiastic network newbies asking (in effect) "how can I learn to be a wizardly hacker? ". Back in 1996 I noticed that there didn't seem to be any other FAQs or web documents that addressed this vital question, so I started this one. A lot of hackers now consider it definitive, and I suppose that means it is. Still, I don't claim to be the exclusive authority on this topic; if you don't like what you read here, write your own. If you are reading a snapshot of this document offline, the current version lives at Note: there is a list of Frequently Asked Questions at the end of this document. Numerous translations of this document are available: ArabicBelorussianChinese, Danish, Dutch, Estonian, FrenchGerman, GreekItalianHebrew, Japanese, Lithuanian, Norwegian, PersianPortuguese (Brazilian), RomanianSpanish, Turkish, and Swedish. 1.
Hack This Site! HashCat GUI Tutorial. “thereisnofatebutwhatwemake”—Turbo-charged cracking comes to long passwords. For the first time, the freely available password cracker ocl-Hashcat-plus is able to tackle passcodes with as many as 55 characters.
It's an improvement that comes as more and more people are relying on long passcodes and phrases to protect their website accounts and other online assets. Until now, ocl-Hashcat-plus, the Hashcat version that can use dozens of graphics cards to simultaneously crack huge numbers of cryptographic hashes, has limited guesses to 15 or fewer characters. (oclHashcat-lite and Hashcat have supported longer passwords, but these programs frequently take much longer to work.) Released over the weekend, ocl-Hashcat-plus version 0.15 can generally accommodate passwords with lengths of 55 characters. Depending on the hash that's being targeted and the types of cracking techniques being used, the maximum can grow as high as 64 characters or as low as 24. OclHashcat-plus - advanced password recovery. How I became a password cracker. At the beginning of a sunny Monday morning earlier this month, I had never cracked a password.
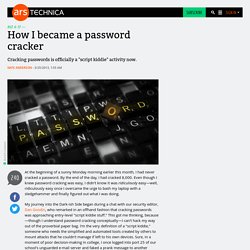
By the end of the day, I had cracked 8,000. Even though I knew password cracking was easy, I didn't know it was ridiculously easy—well, ridiculously easy once I overcame the urge to bash my laptop with a sledgehammer and finally figured out what I was doing. My journey into the Dark-ish Side began during a chat with our security editor, Dan Goodin, who remarked in an offhand fashion that cracking passwords was approaching entry-level "script kiddie stuff. " This got me thinking, because—though I understand password cracking conceptually—I can't hack my way out of the proverbial paper bag.
I'm the very definition of a "script kiddie," someone who needs the simplified and automated tools created by others to mount attacks that he couldn't manage if left to his own devices. It sounded like an interesting challenge. I could. “Password recovery” Trick question. . The first hit. GUI interface using visual basic to track the killers IP address CSI. I am a professional hacker (pentester). Companies pay me to hack their computers and tell them how I did it. AMA! : IAmA. Learn Hacking in 5 easy steps. First of all I wanna tell you that hacking is a art.

I am teaching you this art so that you can make yourself more secure. I don't want you to use my techniques to harm others because hackers never harm others, crackers do. And we are Hackers not cracker. There are 5 easy steps to learn Hacking :- 1. There are lots of techniques to hide yourself from target computer. I am mentioning few important tricks below :- Use Hide Ip Software :- This software will help you to hide your IP address.Use Firewall :- Firewall secure your computer as well as restrict any personal information from going outside.Use Proxy servers :- Whenever you want to surf the computer of your target use proxy servers.Use others username and password :- Try to avoid using your own user name and password for internet connection. 2. What is Ip address :- It's full form is Internet Protocol Address. 3.Gather information about target computer such as its operating system ,time,date etc etc .
What 's the need ? CryptoHeaven: Zero-knowledge Secure Email, Encrypted Email and Cloud Storage.