

Zendesk Security Breach Affects Twitter, Tumblr and Pinterest. Customer service software provider Zendesk announced a security breach that allowed attackers into its system, where they could access data from three customers this week.

Wired learned those three clients were Twitter, Pinterest and Tumblr. The San Francisco-based company announced the breach in a blog post published early Thursday night. Tumblr notified affected users in an email at approximately 6:35 p.m. PST; Twitter and Pinterest are expected to do so shortly. Zendesk declined to comment beyond its blog post, titled, appropriately, "We've been hacked. " We’ve become aware that a hacker accessed our system this week. Zendesk allows companies to outsource many of their customer service functions to it via software tools. Cyber Intelligence Sharing and Protection Act. The Cyber Intelligence Sharing and Protection Act (CISPA H.R. 3523 (112th Congress), H.R. 624 (113th Congress)) is a proposed law in the United States which would allow for the sharing of Internet traffic information between the U.S. government and technology and manufacturing companies. The stated aim of the bill is to help the U.S. government investigate cyber threats and ensure the security of networks against cyberattacks.[1] Some critics saw CISPA as a second attempt at strengthening digital piracy laws after the Stop Online Piracy Act and the Protect Intellectual Property Act both met huge opposition.[12] Intellectual property theft was initially listed in the bill as a possible cause for sharing Web traffic information with the government, though it was removed in subsequent drafts.[13] Content[edit] CISPA is an amendment to the National Security Act of 1947, which does not currently contain provisions pertaining to cybercrime.
Recent developments[edit] House voting counts[edit] Software that tracks people on social media created by defence firm. A multinational security firm has secretly developed software capable of tracking people's movements and predicting future behaviour by mining data from social networking websites.
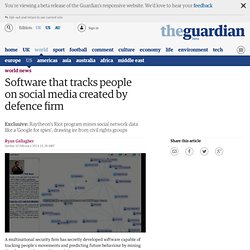
A video obtained by the Guardian reveals how an "extreme-scale analytics" system created by Raytheon, the world's fifth largest defence contractor, can gather vast amounts of information about people from websites including Facebook, Twitter and Foursquare. Raytheon says it has not sold the software – named Riot, or Rapid Information Overlay Technology – to any clients. But the Massachusetts-based company has acknowledged the technology was shared with US government and industry as part of a joint research and development effort, in 2010, to help build a national security system capable of analysing "trillions of entities" from cyberspace.
Using Riot it is possible to gain an entire snapshot of a person's life – their friends, the places they visit charted on a map – in little more than a few clicks of a button. Cryptography I. Download Pidgin for Windows. How a social engineer tricked Wal-Mart into handing over sensitive information. Wal-Mart pretty much sliced itself open and spilled its guts onto the scammer's lap.
In this year's Capture the Flag social engineering contest at Defcon, champion Shane MacDougall used good lying, a lucrative (albeit bogus) government contract, and his talent for self-effacing small talk to squeeze the following information out of Wal-Mart: The small-town Canadian Wal-Mart store's janitorial contractor,Its cafeteria food-services provider,Its employee pay cycle,Its staff shift schedules,The time managers take their breaks, Where they usually go for lunch, Type of PC used by the manager, Make and version numbers of the computer's operating system, and Its Web browser and antivirus software. Reporting from the Las Vegas show, which wrapped up a few weeks ago, Stacy Cowley at CNNMoney wrote up the details of how Wal-Mart got taken in to the extent of coughing up so much scam-worthy treasure. But first, he told the store manager, he needed a thorough picture of how the store operated. New Memory Method Lets Users Remember Long Passwords.
'Implicit learning' lets users store a 30-character password in their memories -- without remembering it Remembering passwords is the biggest bane of security for most users.

But what if you could learn a long password and remember it subconsciously, like you remember how to ride a bike? According to a report about subconscious passwords in the publication Extreme Tech, a group of neuroscientists and cryptographers have developed a password system that does just that. Scrambls - home. Magic Quadrant for Endpoint Protection Platforms. Attackers Divert Bank Phone Calls to Cover Tracks.
Poisoning The Data Well. FIDO Alliance technology will allow enterprises to replace passwords with plug-and-play multifactor authentication.
By Phil Dunkelberger President & CEO, Nok Nok Labs, 3/26/2014 1 Comment | Read | Post a Comment News Hackers interrupt and deface sites of black-market forums selling credit card data stolen from Target and other retailers.By Mathew J. Schwartz , 3/18/2014. Encrypt Stick Features & Benefits. Sucuri - Protect Your Interwebs. Protect The Business - Enable Access. Danger Room. Wardriving Evolves Into Warflying. Www.isecpartners.com/storage/docs/presentations/iSEC_BH2011_Mac_APT.pdf. News. Opinion. Advice. Research. Over a million web sites affected in mass SQL injection attack.