

NIST Releases New Federal Cloud Standards - Cloud Computing. Patriot Day: 10 years later - Assurance in the Aether. Two New Publications Provide a Cloud Computing Standards Roadmap and Reference Architecture. The National Institute of Standards and Technology (NIST) has published two new documents on cloud computing: the first edition of a cloud computing standards roadmap and a cloud computing reference architecture and taxonomy.

Together, the documents provide guidance to help understand cloud computing standards and categories of cloud services that can be used government-wide. These documents, along with others from NIST and NIST working groups, will be incorporated into the NIST U.S. Government Cloud Computing Technology Roadmap, expected to be published in November, 2011. Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of computing resources, including servers, data storage and applications and services.
The working group categorized these standards for features such as security, portability and interoperability, and identified models, studies and use cases relevant to cloud computing.
Web security. Plenty to Hide. June 7, 2012 By Jay Stanley , Senior Policy Analyst, ACLU Speech, Privacy and Technology Project at 1:57pm A commentator on my recent post about the DEA installing license plate scanners on the nation’s interstate highways asks, “If you aren't doing anything illegal why would you care if someone captures your license plate number?”

Another commentator countered: “If I'm not doing anything illegal, why do the police need to record my license plate number?”
Nessus FAQ. If your whole life is in your phone, you'd better not lose it. Cryptography. Building For A Secure Future: Risk Assessment. Before a designer can recommend security measures for a facility, he or she must understand what people and property–the "assets" in security parlance–need to be protected.
Usually this assessment is quite straightforward, but the task gets complicated when trying to predict where threats may come. This knowledge has a direct bearing on what kinds of damage the designer must attempt to mitigate. "You can't even do the simplest facility assessment until you know what the threats are. What's the point? " says Bill McCarthy, an associate architect with RTKL in Baltimore. The assortment of potential security problems facing any organization has always been limited only by the collective imaginations of its members. PREDICTING THREATS The range of difficulty involved in predicting threats against persons and property runs the gamut from the obvious to the impossible. What law enforcement can determine using crime figures alone is somewhat limited because they omit many factors. What is the best starting point to embrace risk management? « InfoSecAlways.com. This is a topic that has generated a great deal of traffic on the Linkedin “Governance, Risk and Compliance Management (GRC) site.
If you are a member I recommend you read through the comments, if not you should consider joining. This is a cross post, slightly modified, of my answer to this question, so forgive the double traffic if you are a member. I was shocked that no one had mentioned the size and financial ability of the company. So this addresses both small and large corporations with and without financial money allocated to security.
If the company is 300 people and has very little money then usually the starting point is convincing management why money needs to be directed towards an assessment versus actually doing something tangible. Now if the company is more mature and financially stable, I agree with several of the current comments, which stated some type of RA framework or COSO control framework. Sarbanes–Oxley Act of 2002. The bill was enacted as a reaction to a number of major corporate and accounting scandals including those affecting Enron, Tyco International, Adelphia, Peregrine Systems and WorldCom.
These scandals cost investors billions of dollars when the share prices of affected companies collapsed, and shook public confidence in the US securities markets. The act was approved by the House by a vote of 423 in favor, 3 opposed, and 8 abstaining and by the Senate with a vote of 99 in favor, 1 abstaining. President George W. Bush signed it into law, stating it included "the most far-reaching reforms of American business practices since the time of Franklin D. Roosevelt. In response to the perception that stricter financial governance laws are needed, SOX-type regulations were subsequently enacted in Canada (2002), Germany (2002), South Africa (2002), France (2003), Australia (2004), India (2005), Japan (2006), Italy (2006)[citation needed], Israel[citation needed] and Turkey[citation needed].
Risk Assessment: A Starting Point. Recently I was asked if I could provide a few pointers to help in developing a risk assessment process for an organization.
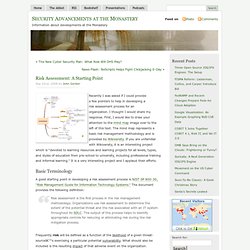
I thought I would share my response. First, I would like to draw your attention to the mind map image over to the left of this text. The mind map represents a basic risk management methodology and is provided by Wikiversity. If you are unfamiliar with Wikiversity, it is an interesting project which is “devoted to learning resources and learning projects for all levels, types, and styles of education from pre-school to university, including professional training and informal learning.”