

Networking in the Cloud Age (LISA 2012 Tutorial) Multiple Paths to Software-Defined Networking. Software-Defined Networking or SDN is making a lot of noise in the press right now (this blog included), yet many are still confused about what SDN is and what is best way to build one.
While many enterprises are just beginning to explore this technology, large telcos and cloud service providers are much further along, testing and deploying SDN technologies in production environments. There are, however, a number of different technologies or approaches that can be used to create a Software-Defined Network.
Depending on which vendor you speak to, the answer will vary. I was reminded of this during a recent conversation wtih ConteXtream, an emerging technology vendor in the SDN space that offers a different approach to SDN as outlined below. Loosely defined, SDN is about separating the control plane from the forwarding plane. Centralized control with OpenFlow connection. Next-generation Enterprise WANs: OpenFlow, Software-Defined Networking and the Enterprise WAN. Context is everything.
In our next column, we’ll resume the discussion of the details behind the Next-generation Enterprise WAN (NEW) architecture. Here, with the recent Open Networking Summit, and the excitement around Software-Defined Networking in general, and OpenFlow in particular, let’s take a look at the adjacent topic of what’s going on in data center (LAN) networking, and whether and how it relates to the Enterprise WAN. Networking Needs a VMware (Part 1: Address Virtualization) « Network Heresy.
[This post was written with Andrew Lambeth] Our last post “Networking Doesn’t Need a VMware” made the point that drawing a simple analogy between server and network virtualization can steer the technical discourse on network virtualization in the wrong direction.

The sentiment comes from the many partner, analyst, and media meetings we’ve been involved in that persistently focus on relatively uninteresting areas of the network virtualization space, specifically, details of encapsulation formats and lookup pipelines. vShield App, vShield Edge, vShield Manager, Use Cases and Comparisons « Researcher's Blog?!?!?! I Rate This Virtualization forms the foundation for building private clouds. Virtualization is essential for transitioning legacy applications to new cloud infrastructure ; it is a key security enabler for cloud environments. Data Center Virtual Machine Fabric Extender (VM-FEX) White Papers. Www.cisco.com/en/US/solutions/collateral/ns340/ns517/ns224/ns955/ns963/solution_overview_c22-687087.pdf.
Virtual Machine Networking: Standards and Solutions [Cisco Data Center Virtual Machine Fabric Extender (VM-FEX) What You Will Learn With the advent of server virtualization, two basic assumptions of data center network design have changed: multiple OS images (or virtual machines) are now allowed to transparently share the same physical server and I/O devices, and the relationship between an OS image and the network is now dynamic.

The access layer of the network extends further to support local switching between different virtual machines within the same server, thus invalidating the traditional assumption that each network access port corresponds to a single physical server running a single image. Further complicating the picture, each virtual machine can be moved from one physical server to another within the data center or even across data centers. One option for network virtualization is to implement a software switch as part of the hypervisor. Another option is to enable the switching function to be performed by an external switch. Virtual Embedded Bridge Figure 1. External Hardware Switch. Embrane. Crossbow: Network Virtualization and Resource Control (Project crossbow.WebHome) - XWiki - (Current Session: Current)
The crossbow project is available as part of Solaris 11 . More information about the technology can be found at our Network Virtualization spotlight OTN . Some of the documents available here may be out of date. For the latest documentation see Solaris 11 Documentation . Crossbow provides the building blocks for network virtualization and resource control by virtualizing the stack and NIC around any service (HTTP, HTTPS, FTP, NFS, etc.), protocol or Virtual machine. VMware vCloud Architecture ToolKit (vCAT) 2.0 – Get Some! Home > Cloud Computing, Virtualization, VMware > VMware vCloud Architecture ToolKit (vCAT) 2.0 – Get Some!
Here’s a great resource for those of you trying to get your arms around VMware’s vCloud Architecture: VMware vCloud Architecture ToolKit (vCAT) 2.0 This is a collection of really useful materials, clearly painting a picture of cloud rosiness, but valuable to understand how to approach the various deployment models and options for VMware’s cloud stack:
NetworkingBasics. Main Page - SecurityAutomata. A simple example of Network Interface Virtualization. I’m seeing some confusion in the blogosphere about how Cisco’s implementation of Network Interface Virtualization (NIV) really works so perhaps a very simple example is needed, and that is the intent of this post.
My previous posts about NIV with Cisco’s Palo adapter were focused on the big picture and the complete solution, such as this post about NIV with the VMware vSwitch, and this post about NIV with the Nexus 1000V. Perhaps in all of the grand detail some of the fundamental concepts were glossed over so I am attempting to revisit the simple concept of how multiple virtual adapters can be treated as if they were multiple physical adapters to provide true Network Interface Virtualization (NIV), or as some others are calling it “Virtual I/O”.
The main confusion I want to address is the belief that VLAN tagging must be implemented on the virtual adapters to uniquely differentiate each virtual adapter to the upstream network switch. Before NIV After NIV Cheers, Brad. Simple use cases for Network Interface Virtualization. My most recent post Simple Example of Network Interface Virtualization generated enough interest and curosity to warrant a follow-up post showing simple uses cases for NIV.
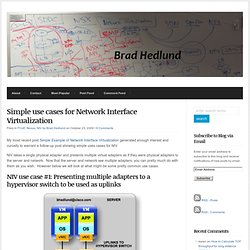
NIV takes a single physical adapter and presents multiple virtual adapters as if they were physical adapters to the server and network. Now that the server and network see multiple adapters, you can pretty much do with them as you wish. However below we will look at what might be some pretty common use cases. NIV use case #1: Presenting multiple adapters to a hypervisor switch to be used as uplinks. Security & Networking: Let's get logical - the case for network virtualization. Security & Networking Biography Allwyn is CTO/VP R&D, Networking & Security BU at VMware.
He was CTO and SVP of Product Operations at Blue Lane Technologies, which was acquired by VMware in October 2008. He was previously the SVP of Products & Operations at netVmg, an intelligent route control company acquired by InterNap in 2003. Prior to netVmg, Allwyn was founder, CTO and EVP of Products and Operations at FirstVirtual Corporation (FVC), a multi-service networking company that had a successful IPO in 1998. Allwyn started his career in 1983 as a software developer at HP in the Information Networks Division, working on the development of TCP/IP protocols. Allwyn holds a Bachelor of Technology degree in Computer Science from the Indian Institute of Technology, Bombay, and a Master of Science in ComputerScience from the University of Wisconsin, Madison.
Posts by Allwyn Sequeira.