

The Basics of C Programming". The previous discussion becomes a little clearer if you understand how memory addresses work in a computer's hardware.
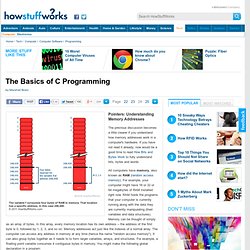
If you have not read it already, now would be a good time to read How Bits and Bytes Work to fully understand bits, bytes and words. All computers have memory, also known as RAM (random access memory). For example, your computer might have 16 or 32 or 64 megabytes of RAM installed right now. RAM holds the programs that your computer is currently running along with the data they are currently manipulating (their variables and data structures).
University lectures computer science. Whether your goal is to earn a promotion, graduate at the top of your class, or just accelerate your life, lectures can help get you there.
Our archives of lectures cover a huge range of topics and have all been handpicked and carefully designed by experienced instructors throughout the world who are dedicated to helping you take the next step toward meeting your career goals. Lifelong learns can turn their free time turn into self-improvement time. The online lectures on this list are more than lecture notes or a slideshow on a topic -- they were designed for audiences like you, with carefully sequenced themes and topics taught by veteran educators, and often with additional resources for your own independent study.
Introduction to Databases. How To Become A Hacker. Copyright © 2001 Eric S.

Raymond As editor of the Jargon File and author of a few other well-known documents of similar nature, I often get email requests from enthusiastic network newbies asking (in effect) "how can I learn to be a wizardly hacker? ". Back in 1996 I noticed that there didn't seem to be any other FAQs or web documents that addressed this vital question, so I started this one. A lot of hackers now consider it definitive, and I suppose that means it is.
Still, I don't claim to be the exclusive authority on this topic; if you don't like what you read here, write your own. If you are reading a snapshot of this document offline, the current version lives at Note: there is a list of Frequently Asked Questions at the end of this document. Numerous translations of this document are available: ArabicBelorussianChinese (Simplified), Czech, Danish, Dutch, Estonian, German, GreekItalianHebrew, Norwegian, PersianPortuguese (Brazilian), RomanianSpanish, Turkish, and Swedish. 1. 2. 3. 30 Useful (and Unknown) Web Apps You Need to Bookmark - Page 1. At Maximum PC, computer hardware is our bread and butter.
We review it, preview it, and just generally love to talk about it. Unfortunately, hardware becomes less important with each passing day, as more and more software moves onto the internet. We're not looking forward to the day that our PC's become Chrome OS-style thin client, but we have to admit, some web apps are pretty awesome. How to use Google for Hacking. Google serves almost 80 percent of all search queries on the Internet, proving itself as the most popular search engine.
However Google makes it possible to reach not only the publicly available information resources, but also gives access to some of the most confidential information that should never have been revealed. In this post I will show how to use Google for exploiting security vulnerabilities within websites. The following are some of the hacks that can be accomplished using Google. 1. Hacking Security Cameras There exists many security cameras used for monitoring places like parking lots, college campus, road traffic etc. which can be hacked using Google so that you can view the images captured by those cameras in real time.
Inurl:”viewerframe? Click on any of the search results (Top 5 recommended) and you will gain access to the live camera which has full controls. you now have access to the Live cameras which work in real-time. Intitle:”Live View / – AXIS” 2. The Best Hacking Tutorial Sites - Learn Legal Hacking. Proyecto Fedora - Descarga Fedora y pruébalo. Edición de escritorio de Fedora 20 Medio vivo de instalación Esta es la última versión de la Edición de Escritorio del sistema operativo Fedora Linux.
Es todo lo que necesita para probar Fedora — usted no deberá borrar nada en su sistema actual para probarlo y no pondrá en riesgo sus archivos. Tome Fedora para un paseo de prueba y si le gusta, puede instalarlo directamente a su disco duro desde el escritorio del Medio Vivo. Descargar ahora 1.0GB, ISO format image for Intel-compatible PCs (64-bit) Top 50 Free Open Source Classes on Computer Science : Comtechtor. Computer science is an interesting field to go into.

There are a number of opportunities in computer science that you can take advantage of. With computers increasingly becoming a regular part of life, those who can work with computers have good opportunities. You can find a good salary with a program in computer science, and as long as you are careful to keep up your skills. Here are 50 free opencourseware classes that can help you learn more about computer science: Introduction to Computer Science Learn the basics of computer science, and get a foundation in how computer science works. Introduction to Computer Science: Learn about the history of computing, as well as the development of computer languages.
Comprehensive Computer Science Collections.