

The 101 Most Useful Websites on the Internet - Digital Inspiration. Here are the most useful websites on the Internet that will make you smarter, increase productivity and help you learn new skills. These incredibly useful websites solve at least one problem really well. And they all have cool URLs that are easy to memorize thus saving you a trip to Google. Also see: The Best Android Apps. Hack N Mod - Amazingly Cool Hacks, Mods, and DIY Projects. Warez-BB.org. Browse like Bond: Use any computer without leaving a trace with Tails. If James Bond logs on to a computer, he doesn't want to leave a bunch of files, cookies, or his IP address out there for someone to find.
It might seem extreme, but sometimes it's a good idea to take the same precautions yourself. In this post, we'll walk through how to use a USB stick or DVD to anonymize, encrypt and hide everything you do on a computer no matter where you are. When we say "browse without leaving a trace", we truly mean it. Using the Linux-based, live-boot operating system Tails (The Amnesiac Incognito Live System), you can use any computer anywhere without anyone knowing you were ever on it.
Tails is a portable operating system with all the security bells and whistles you'll ever need already installed on it. The Software Packed Directly into TailsOnce you create your Tails boot disc, you'll be ready to reboot your computer into an encrypted and private operating system preloaded with all the software you'll need to browse the Web, email, IM, and edit documents. Get Detailed Information About Particular IP address Connections Using netstat Command.
Netstat command and shell pipe feature can be used to dig out more information about particular IP address connection.
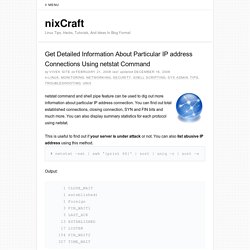
You can find out total established connections, closing connection, SYN and FIN bits and much more. You can also display summary statistics for each protocol using netstat. This is useful to find out if your server is under attack or not. You can also list abusive IP address using this method. # netstat -nat | awk '{print $6}' | sort | uniq -c | sort -n Output: 1 CLOSE_WAIT 1 established) 1 Foreign 3 FIN_WAIT1 3 LAST_ACK 13 ESTABLISHED 17 LISTEN 154 FIN_WAIT2 327 TIME_WAIT.
Cheat Sheet : All Cheat Sheets in one page. More than 10.2 million product reviews at Buzz. Screen Name Generator. Keyword suggestion tool — Google suggest scraper — Übersuggest. The Bro Code. Strikethrough T̶e̶x̶t̶ / Cross Out Text Generator : Facebook – Twitter – Mobile. Search - Find a PANTONE Color. Free Monthly Budgeting And Personal Finance Software: JXCirrusFinance.
User Ratings: [Total: 0 Average: 0/5] JXCirrusFinance is a free cross platform personal finance management software which you can use in order to keep track of your monthly budget and transactions.
Multiple accounts can be setup, bank accounts, credit cards, carry around money balances are available by default, and you can add more of them if you’re interested. That way you can for example separate between your current account and savings, and keep track of their balances separately. Sponsored Links. Discover Products that Match Your Personality. Wireshark · Go deep. Wireshark Display Filters. Hack a Day — Fresh hacks every day. [DEFCON 20] Spy vs. Spy: Spying on Mobile Device Spyware. The Evolution of Phishing. If you’ve got an email account or social media profile, it’s likely you’ve come across phishing of some kind before.

In a sentence, phishing is the fraudulent attempt to steal personal information by social engineering: the act of criminal deception. Verizon’s latest Data Breach Investigations Report notes that “social engineering remains worryingly effective” in targeting users, with over 30 percent of phishing messages sent during 2016 opened — up from 23 percent in 2014. Considering the takeaways from Verizon’s report, Tripwire editor David Bisson saliently remarks that “no locale, industry, or organisation is safe” from phishing; further analysis found that credential exfiltration and theft of trade secrets remain threat actors’ primary motives.
Phishing has clearly gained traction as an opportunistic vector; the frequency of this threat can be mapped to a concerning upward pattern. AOL, warez and the origins of phishing Criminal campaigns Spear phishing Whaling and CEO fraud. BlaBlaMeter - Bullshit detection tool. KnowEm Username Search. Web Hosting Search Tool, Reviews & More at WhoIsHostingThis.com. Online Penetration Testing Tools. About this tool Every penetration test should start with a passive reconnaissance phase.
Since public search engines have gathered huge amounts of information about almost every website from the Internet, it is a good idea to make some queries and get this information from them. 7 Tips for a Polished Web Page. Different web designers make use of simple techniques to allow their web page to stand out.
Here are 7 tips that I have made use of for one of the mock ups I’m working on. It’s the little, subtle things that really make the biggest difference. Just a note, this article is not for advanced users, but it is good to have a re-read about it. 1. Use Anti-Alias for fonts Anti-aliasing improves reading speed and accuracy. 2.