

Linux AuFS Examples: Another Union File System Tutorial (UnionFS Implementation) AuFS stands for Another Union File System.
AuFS started as an implementation of UnionFS Union File System. An union filesystem takes an existing filesystem and transparently overlays it on a newer filesystem. It allows files and directories of separate filesystem to co-exist under a single roof. LXC. Translation(s): none Linux Containers (LXC) provide a Free Software virtualization system for computers running GNU/Linux.
This is accomplished through kernel level isolation. It allows one to run multiple virtual units simultaneously. Those units, similar to chroots, are sufficiently isolated to guarantee the required security, but utilize available resources efficiently, as they run on the same kernel. For all related information visit : Debian Virtualization: Back to the Basics, part 3. The traditional Linux security model starts with file permissions.

The model lets the kernel decide whether or not a process may access a resource based on permissions set as part of the filesystem. The coarse-grained granularity of this model often causes Linux processes to have too many rights. If more granularity is needed, one has to resort to adding security related code into the program source. This series of articles is about Linux namespaces, a lightweight virtualization technology implemented in Linux kernel. In part 1 I’ve talked about building chroot jails using mount namespace, and in part 2 I’ve looked into isolating processes using PID namespace. Security at this level is always reactive. The same effect can be achieved on the cheap using Linux namespaces.
Network setup Configuring the host On the host, I run the following script: The script creates br0 bridge interface, enables routing, and configures the firewall. Configuring the container. Install LXC + Web Panel on Ubuntu 13.04 w/NAT - Tutorials and Guides - vpsBoard. Kicking off my new blog, blog.jarland.me, with a guide for something that I have enjoyed recently.
I know some other hobbyists here might enjoy the experiment in something they may not have done before. Overlayfs. Docker has been a great advancement for mass consumption of linux based containers.

The maturation of the virtual machine boom that has been happening since the early 2000’s led to mass acceptance and deployment in public and private clouds. To be sure, asking for bare metal today can be seen as a faux pas without some well-defined use case (like super high IO). So, now that folks have accepted that slices of CPU, memory, and disk are good enough through well-known hypervisors (kvm, esxi, xen) for most workloads, taking the next step to containers will not be that big of a leap.
Except that now it is more common to run containers on VMs than bare metal. So now we get a slice of a slice of a slice of resources! Virtual machines are just what their name implies: full machines that are virtualized. Boot or Start? Lightweight Virtualization: LXC containers & AUFS. Conteneur LXC + NAT [Bearstech Blog] LXC/SimpleBridge. Translation(s): none This page includes examples of a bridged or routed network provided by the host.
Alternatives to this network setup for containers can be found on the LXC main page. Host device as bridge Features: persisted in host's /etc/network/interfaces the container's veth virtual ethernet interface can share the network link on the physical interface of the host (eth0). Setting up LXC containers in 30 minutes (Debian Wheezy)
UpdateVagrant has an LXC plugin that allows you to run containers instead of VMs in an almost transparent manner.

Most of this guide still applies if you need to setup the networking for your containers or enable cgroups. Why LXC? So I'm doing web development, and I'm using Debian Wheezy as my development environment, which doesn't have the same version of software than stable, which is what we usually use as target servers. I used to use chroots for this, but I found them painful to manage, especially when running daemons on the same ports than on the host machine.
People like to use virtualization for this, such as VirtualBox (esp. with Vagrant) but I didn't want that since it forces you to start a whole virtual machine every time you want to develop. Advanced networking - Docker Documentation. Estimated reading time: 15 minutes This section provides an overview of Docker’s default networking behavior, including the type of networks created by default and how to create your own user-defined networks.
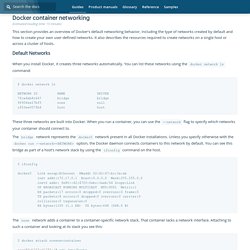
It also describes the resources required to create networks on a single host or across a cluster of hosts. Default Networks When you install Docker, it creates three networks automatically. LXC, la solution de virtualisation légère - Choix-Libres : Web log d'un utilisateur/administrateur GNU/Linux. HA Cluster with Linux Containers based on Heartbeat, Pacemaker, DRBD and LXC - Thomas-Krenn-Wiki. The following article describes how to setup a two node HA (high availability) cluster with lightweight virtualization (Linux containers, LXC), data replication (DRBD), cluster management (Pacemaker, Heartbeat), logical volume management (LVM), and a graphical user interface (LCMC).
As a result you will get a very resource- and cost-efficient shared-nothing cluster solution based completely on Open Source. Ubuntu 12.04 LTS is used as operating system. Créer des serveurs virtuels Debian 7 Wheezy avec LXC sur un dédié OVH Kimsufi. (Dernière mise à jour : 19 février 2015) Présentation de LXC Tout comme Linux-VServer et OpenVZ, LXC est une solution de virtualisation de type isolateur.

Cette solution permet la virtualisation par container au niveau du noyau. LXC est très récent et remplace Linux-VServer et OpenVZ. Aussi, LXC est dès à présent intégré au noyau, ce qui n’a jamais été le cas des deux solutions citées précédemment. L’isolateur tire avantage de la possibilité, unique sous UNIX et Linux, de partager le noyau avec d’autres processus du système. Un programme, ensemble de programmes ou système dans le cas de virtualisation à noyau partagé fonctionnant dans un environnement chroot est protégé en faisant croire au système emprisonné qu’il fonctionne sur une machine réelle avec son propre système de fichiers. Cette solution est très performante du fait du peu d’overhead puisque les environnements virtualisés se partagent le code du noyau.
Notes Compilation du nouveau noyau Linux Si screen n’est pas déjà installé : Sans titre. Running LXC containers with Debian - Tutorials and Guides - vpsBoard. My love to LXC started again after this great post from jarland about LXC and Ubuntu. Ubuntu (latest stuff) and LXC are nice partners and play well. The web-based GUI is done in the right way. But basically you do not need the GUI and you do not need Ubuntu to use LXC. My tutorial today will show the basic low-end consolish Debian way to work with LXC. So what is LXC? 12.2. Virtualization. There are multiple virtualization solutions, each with its own pros and cons.
This book will focus on Xen, LXC, and KVM, but other noteworthy implementations include the following: Xen is a “paravirtualization” solution. 12.2. Virtualization.