

Top 75 Network Security Tools. IP Calculator / IP Subnetting. Ipcalc takes an IP address and netmask and calculates the resulting broadcast, network, Cisco wildcard mask, and host range.

By giving a second netmask, you can design subnets and supernets. It is also intended to be a teaching tool and presents the subnetting results as easy-to-understand binary values. Enter your netmask(s) in CIDR notation (/25) or dotted decimals (255.255.255.0). Inverse netmasks are recognized. If you omit the netmask ipcalc uses the default netmask for the class of your network. Look at the space between the bits of the addresses: The bits before it are the network part of the address, the bits after it are the host part. Designing Subnets. How the extended network prefixes work Well, the subnet mask is in charge of this.

The subnet mask looks for the network prefix to ensure that a synchronized job is being processed. For example, if you need to specify a subnet mask in a class network, any subnet that you will specify will define your network Fig 8.7 Even though the subnet mask is in charge of the lookup, the router protocol refers to the extended network prefix length rather than the actual subnet mask. Network Engineering, Designing Subnets Example of Sub-netting: If a company has been assigned a network number 192.168.1.0/24 and it needs to define six subnets; it is required to support at least 28 hosts for one of their departments. First we need to determine the number of bits required for the six subnets. Observe the power notation above, it is impossible to define six, therefore 23= 8 (3-bits are required). Networktools. Network-security. Bandwidth Meter.
List of TCP and UDP port numbers. Wikipedia list article This is a list of TCP and UDP port numbers used by protocols for operation of network applications.
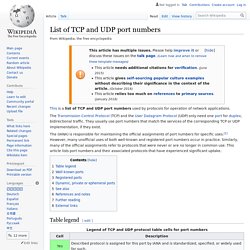
The (IANA) is responsible for maintaining the official assignments of port numbers for specific uses.[1] However, many unofficial uses of both well-known and registered port numbers occur in practice. Similarly, many of the official assignments refer to protocols that were never or are no longer in common use. This article lists port numbers and their associated protocols that have experienced significant uptake. Table legend[edit] Well-known ports[edit] The port numbers in the range from 0 to 1023 (0 to 210 − 1) are the well-known ports or system ports.[3] They are used by system processes that provide widely used types of network services.
Registered ports[edit] The range of port numbers from 1024 to 49151 (210 to 214 + 215 − 1) are the registered ports. Dynamic, private or ephemeral ports[edit] See also[edit] References and notes[edit] Stretch, Jeremy. Open Ports Tool. Remote Address Port Number Check a port's status by entering an address and port number above.
The open port checker is a tool you can use to check your external IP address and detect open ports on your connection. This tool is useful for finding out if your port forwarding is setup correctly or if your server applications are being blocked by a firewall. This tool may also be used as a port scanner to scan your network for ports that are commonly forwarded.
For more a comprehensive list of TCP and UDP ports, check out this Wikipedia article. If you are looking for a software solution to help you configure port forwarding on your network, try using this powerful Port Forwarding Wizard. Introduction to Network Security. Browser Toolbars Online Privacy - Toolbar Removal Tool. The risk with website monitoring is that it's possible for query strings to be monitored and retransmitted.
Query strings are data strings following the '? ' delimiter in urls often used by webform submissions and search engines. Query strings may contain sensitive information such as credit card numbers, passwords, names, addresses, hotel/flight reservation details and other personally identifiable information which an unethical browser extension could monitor and retransmit to its home server or a third party. Firewalls won't block browser extensions because they're integrated into the web browser. Browser toolbars can sometimes be removed by using the Windows Add/Remove Programs utility or by running the toolbar's uninstaller which should be packaged with it. Before removing an adware toolbar you may like to take notes and screenshots of the companies being advertised in its links, search listings or pop-up ads.
DNS Stuff: DNS tools, DNS hosting tests, WHOIS, traceroute, ping, and other network and domain name tools. Block Network Attacks with SnortSAM - IT Observer. SnortSAM is an open source agent that allows Snort intrusion detection system to block attacking connections by reconfiguration of access control lists on firewalls – stopping an attack in progress.
SnortSAM can order changes on firewalls such as CheckPoint, Cisco PIX firewalls, Cisco routers, UNIX-based firewalls and more. SnortSAM consists of two components: a patch for the Snort IDS itself and the SnortSAM application, which can be run on a dedicated SnortSAM server or on the Snort sensor. SnortSAM uses Snort´s output plug-in that notifies SnortSAM agent of blocking requests on a rule basis. When an alert is detected, the firewall(s) access control lists are modified to block traffic from the offending network.