

Bluetooth 5 Coming With Massively Enhanced Range And Speed - Technical Questions & Answers. The next huge upgrade to Bluetooth is set.
The executive director of Bluetooth Special Interest Group (SIG) Mark Powell wrote an email message to the UK health and monitoring company Blue Maestro, regarding that Bluetooth version 5 will be launched on June 16 in London. Powell assertions that Bluetooth 5 offers double the range and four times faster speed as compared to the present offering. Furthermore, he says that it will also provide support to a broader range of devices important in today's times. To recall, the latest version was detailed slightly in November last year, with the spotlight on IoT devices. Moreover, Powell wrote in his email message, "Bluetooth 5 will also provide significant new functionality for connectionless services like location-relevant information and navigation. The amount point jump with Bluetooth v5 translates to a huge upgrade in itself.
The roadmap for the latest version was outlined last year, but a real release with extra details is set for June 16. Defencebyte Blog: The Perfect Security for Your Computer. Backdoor.Teamviewer is a Trojan infection which feign to be an Adobe Flash Player installer, but actually, it’s a malicious computer programs that hacks into your PC and bring destructive alteration on your computer.
This Trojan deceives the computer user to get in to user’s computer. First it installs a copy of the TeamViewer remote access application on to the target computer and when the TeamViewer is installed, it reconnects to the hackers Command & Control server and adduce the IP address of the infected PC. Once the hackers get the IP address of the victim’s computer, they can access the victim’s computer remotely and take remote control of it. Once they are connected, they can use the user’s computer as if they are in front of the computer. Navigation.iwatchavi.com Browser Hijacker Removal Tool. The Iiwatchavi.com Browser Hijacker is an unwanted computer program that replaces the home page of your installed browsers to navigation.iwatchavi.com.
This browser hijacker is the tool from the Adware/Shortcut Hijacker that replaces you home page by modifying the shortcuts for your entire installed browser. It doesn’t install a program that infects your shortcuts. Rather, it installs a special VBScript into the Windows Management Instrumentations (WMI) to modify the shortcuts of all the browsers installed on your computer. As there is no program installed on the targeted computer, so the security software are able to detect the infected shortcuts, but not able to remove WMI script completely. That’s why user will find the infection again even after removing it. How to fix Kaspersky Error Code 0X800723 Error - TechNetOnlines. How to Update Avast Program Versions and Virus definitions - PCTECH24. The performance of any antivirus program is dependent on the efficiency of the virus detection and deletion.
A good antivirus is known how effective its database because on the basis of the virus definitions an antivirus program has. On the basis of this database, a program identifies threats, so it’s important that the virus definitions are regularly updated. To detect and remove various types of bugs and viruses, users need to update the program to its latest version and other general program improvements. So if a new version is available, update the Engine and Virus Definitions (VPS) instantly.
Chrome Cleanup Tool to Simplify Your Browsing Experience - TechNetOnlines. Defencebyte Blog: The Perfect Security for Your Computer. Hao123Tab is an agent from the browser plug-in category.
This browser extension is specifically made for Google Chrome browser and this extension promotes itself as a very useful tool. Defencebyte Blog: The Perfect Security for Your Computer. EasyHotSpot is an unwanted adware computer program and it advertise itself as a useful tool that helps you to configure Windows for sharing the Internet connection with other users.
Although this function is useful, but this program isn’t trustworthy and may expose your system to multiple threats. This program display irrelevant and unwanted ads while a computer user browses the Internet. As soon as you put your cursor on these advertisements mistakenly or click on them, the attached link will open in the new tab showing the advertisement. Often EasyHotSpot and such adware hide themselves behind the free applications and install on the user’s computer without their consent. How to Get the Setup Log File if Avast Installation Fails. There may be several reasons if you’re trying to install and download Avast on your computer and could not be successful or it quits unexpectedly.
If you connect to any tech support service providing company to help you in Avast installation, you will be asked to provide a setup log file for further analysis. You can access and copy a setup log file to a text file from the screen where Avast Setup wizard notifies you about an error that occurs while completing the setup. Methods to Fix Errors Caused by Avast Antivirus. Defencebyte Blog: The Perfect Security for Your Computer. Search.fc-cmf.com is a browser hijacker and it’s caused cause by adware infection.
It redirects you to another unknown search engine as soon as you access your browser. It changes your home page and redirects you on the unknown and risky sites. This unwanted software program may alter or take over start-up page and as well as new tab configuration. If you open your home page and find Search.fc-cmf.com has opened, it means adware has change the settings of your browser. Adware authors replace the default search engine and set their own as your home page. Thus, if Search.fc-cmf.com is showing up as your home page, it signifies that adware already made changes to browser settings.
Adware authors pack their adware programs with the freeware and these programs gets installed when you install any freeware. Defencebyte Blog: The Perfect Security for Your Computer. Petya is a horrible ransom agent which encrypt your data and dpesn’t let you to access them until you decrypt them using a decryption key.
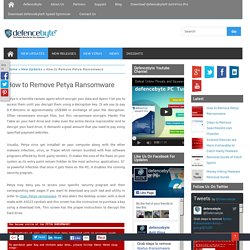
It ask you to pay 0.9 Bitcoins or approximately US$380 in exchange of your file decryption. Often ransomware encrypt files, but this ransomware encrypts Master File Table on your hard drive and make even the entire device inaccessible And to decrypt your hard drive, it demands a good amount that you need to pay using specified payment websites. Usually, Petya virus get installed on your computer along with the other malware infection, virus, or Trojan which remain bundled with free software programs offered by third-party vendors.
It makes the uses of the flaws on your system as its entry point remain hidden to the most antivirus applications. It’ so powerful infection that once it gets there on the PC, it disables the running security program. Important Note: Steps to Create and Use Avast Rescue Disk. There are multiples types of malwares and infections which may prevent the Avast installation on your computer.
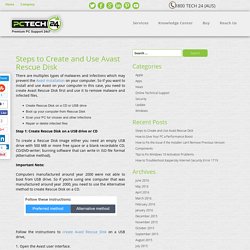
So if you want to install and use Avast on your computer in this case, you need to create Avast Rescue Disk first and use it to remove malware and infected files. Create Rescue Disk on a CD or USB driveBoot up your computer from Rescue DiskScan your PC for viruses and other infectionsRepair or delete infected files Step 1: Create Rescue Disk on a USB drive or CD To create a Rescue Disk image either you need an empty USB drive with 500 MB or more free space or a blank recordable CD; CD/DVD-writer; burning software that can write in ISO file format (Alternative method). Important Note: Computers manufactured around year 2000 were not able to boot from USB drive. Searchlock3.com Hijacker Removal Tool. Computer users may experience that their default search engine set on the existing browser has been replaced by Searchlock3.com or other such browser hijacking search engine sites. Often these random browser programs get installed decisively. It get installed without asking for the approval from the computer owner or user.
Once it get installed, it comes up as a default start-up page even if you haven’t set it as default page. It pretends to be a normal search engine page, but actually it’s a very risky program. How to Fix “Incompatible Software Found” Error Displays While Installing Trend Micro Security software. How to Fix “Installation Incomplete… Error code: #0, 1003, 0x000” How to Use the Trend Micro Vulnerability Scanner (TMVS) for Installing Worry-Free Business Security Agent. How to Fix the Issue if the Installer can’t Remove Previous Version Components. The Installer can’t Remove Previous Version Components “displays while installing or upgrading TrendMicro Worry-Free Business Security (WFBS) Agent 7.0 You receive the following error message if the WFBS 7.0 Security Agent (SA) failed to install or upgrade: Installation Unsuccessful.
How to Troubleshoot Avast! Antivirus RPC Error. Avast! Antivirus Error RPC encounters because of corrupt download or incomplete installation of its anti-virus software. How to Fix Error “Setup cannot continue… Error code 215″ While Upgrading Worry-Free Business Security (WFBS) Agent. How to Troubleshoot Kaspersky Internet-Security Error 1719. Kaspersky 1719 error encounters because of corrupt download or incomplete installation of its anti-virus software. How to Troubleshoot Kaspersky Anti-Virus Error Code 502. Kaspersky 502 error encounters because of corrupt download or incomplete installation of its anti-virus software. There is any issue with the Windows registry or your system is already under the influence of severe malware and infections, or there is already an anti-virus program running onyour computer, or some other application has meticulously removed Kaspersky anti-virus related files.
Your system shows following symptoms if error 502 encounters: It appears and crashes all the running applicationsWhile installing Kaspersky program, it crashes the PCComputer freezes periodicallyIt executes the inputs with a delay and responds significantly slow This error may appear while installing a any software program while a Kaspersky Lab-related program is running, or during installation of the Windows operating system, or while Windows startup and shutdown. Please note that these instructions are applicable for Windows 10/8/7/Vista/XP/ME/2000 Step 2: Perform a Full Malware Scan of Your PC.