

Obama gives himself control of all communication systems in America. Main Core. Main Core is the code name of a database maintained since the 1980s by the federal government of the United States.
Main Core contains personal and financial data of millions of U.S. citizens believed to be threats to national security.[1] The data, which comes from the NSA, FBI, CIA, and other sources,[1] is collected and stored without warrants or court orders.[1] The database's name derives from the fact that it contains "copies of the 'main core' or essence of each item of intelligence information on Americans produced by the FBI and the other agencies of the U.S. intelligence community. "[1] The Main Core database is believed to have originated with the Federal Emergency Management Agency (FEMA) in 1982, following Ronald Reagan's Continuity of Operations plan outlined in the National Security Directive (NSD) 69 / National Security Decision Directive (NSDD) 55, entitled "Enduring National Leadership," implemented on September 14, 1982.[1][2] See also[edit] References[edit] Where Did Our ‘Inalienable Rights’ Go?
Can Wi-Fi let you see people through walls? Do you really wish you had X-ray vision?
Sure, it would be fun to see what your neighbors are doing behind those walls -- until you see something you wish you hadn't. Regardless, researchers at MIT have developed a sensing technology that uses low-power Wi-Fi to detect moving people. It follows other wall-penetrating sensor tech using radar and heavy equipment. The Wi-Vi system by Dina Katabi and Fadel Adib sends out a low-power Wi-Fi signal and tracks its reflections to sense people moving around, even if they're in closed rooms or behind walls. Part of a Wi-Fi signal transmitted at a wall will penetrate it and reflect off people on the other side. See Through Walls with WiFi. Surveillance device uses Wi-Fi to see through walls. Researchers in England have created a prototype surveillance device that can be used to spy on people inside buildings and behind walls by tracking the frequency changes as Wi-Fi signals generated by wireless routers and access points bounce off people as they move around.
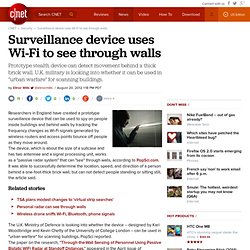
The device, which is about the size of a suitcase and has two antennae and a signal processing unit, works as a "passive radar system" that can "see" through walls, according to PopSci.com. It was able to successfully determine the location, speed, and direction of a person behind a one-foot-thick brick wall, but can not detect people standing or sitting still, the article said.
The U.K. ECHELON. ECHELON[needs IPA], originally a code-name, is now used in global media and in popular culture to describe a signals intelligence (SIGINT) collection and analysis network operated on behalf of the five signatory nations to the UKUSA Security Agreement[1] — Australia, Canada, New Zealand, the United Kingdom, and the United States.
Referred to by a number of other abbreviations, including AUSCANNZUKUS[1] and Five Eyes,[2][3][4] it has also been described as the only software system which controls the download and dissemination of the intercept of commercial satellite trunk communications.[5] It was created in the early 1960s to monitor the military and diplomatic communications of the Soviet Union and its Eastern Bloc allies during the Cold War, and was formally established in the year of 1971.[6][7] §Name[edit] Britain's The Guardian newspaper summarized the capabilities of the ECHELON system as follows: §History[edit] §Origins (1960s–1970s)[edit] §Expansion (1980s)[edit] §Organization[edit] UKUSA Agreement. The "Five Eyes", often abbreviated as "FVEY", refer to an intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States.
These countries are bound by the multilateral UKUSA Agreement, a treaty for joint cooperation in signals intelligence.[1][2][3] The origins of the FVEY can be traced back to World War II, when the Atlantic Charter was issued by the Allies to lay out their goals for a post-war world. During the course of the Cold War, the ECHELON surveillance system was initially developed by the FVEY to monitor the communications of the former Soviet Union and the Eastern Bloc, although it allegedly was later used to monitor billions of private communications worldwide.[4][5] Amid Data Controversy, NSA Builds Its Biggest Data Farm. Hide captionA National Security Agency data center is under construction in Bluffdale, Utah.
When this data center opens in the fall, it will be the largest spy data center for the NSA. George Frey/EPA/LANDOV A National Security Agency data center is under construction in Bluffdale, Utah. Biometric Database of All Adult Americans Hidden in Immigration Reform. Illustration: National Institutes of Health The immigration reform measure the Senate began debating yesterday would create a national biometric database of virtually every adult in the U.S., in what privacy groups fear could be the first step to a ubiquitous national identification system.
Buried in the more than 800 pages of the bipartisan legislation (.pdf) is language mandating the creation of the innocuously-named “photo tool,” a massive federal database administered by the Department of Homeland Security and containing names, ages, Social Security numbers and photographs of everyone in the country with a driver’s license or other state-issued photo ID. Employers would be obliged to look up every new hire in the database to verify that they match their photo. This piece of the Border Security, Economic Opportunity, and Immigration Modernization Act is aimed at curbing employment of undocumented immigrants. EAS13500toMDM13313redline.pdf. Immigration Bill Trojan Horse for Biometrics. The Immigration Bill Does NOT Create a 'Biometric Database of All Adult Americans'
The Wonderful American World of Informers and Agents Provocateurs by Tom Engelhardt. WHAT HAPPENED IN TRIPOLI FROM 20th to 22nd of AUGUST - THE TRUTH !! REAL GREEN SQUARE Vs FAKE CNN's GREEN SQUARE It’s no longer a surprise that a media war is being waged against Gaddafi and Libya.
In March, all news were breaking and highly contradictive towards each other. It arose in global media approximately on 15th of August, when a Saudi Arabia newspaper Asharq Alawsat told that Gaddafi is allegedly ill and ready to leave the country. Saudis, mortal enemies of Muammar Gaddafi, were, of course, such a reliable source, that all other papers followed. 31no.jpg (JPEG Image, 1024 × 218 pixels) s6my.jpg (JPEG Image, 1024 × 271 pixels) Sijb.jpg (JPEG Image, 1024 × 200 pixels) Black Hat vs. White Hat - Snowden, Hastings & Barret Brown.
The United States Seized Confidential Mail Records Of European Parliament. Privacy – Christian Engström I can’t say I’m surprised – but we’ve got the United States and its security bureaucrats digging through our e-mail in the European Parliament. Jakob Augstein: Data Spying Programs Threaten German Security. "Germany's security is also being defended in the Hindu Kush, too," Peter Struck, who was Germany's defense minister at the time, said in 2002.

If that's true, then the government should also be expected to defend the security of its people at their own doorstep. Because the massive sniffing out and saving of data of all kinds -- that of citizens and businesses, newspapers, political parties, government agencies -- is in the end just that: a question of security. It is about the principles of the rule of law. And it is a matter of national security. Demonizing Edward Snowden: Which Side Are You On?
As I write this, a bunch of reporters are flying from Moscow to Havana on an Aeroflot Airbus 330, but Edward Snowden isn’t sitting among them.
His whereabouts are unknown. He might still be in the V.I.P. lounge at Sheremetyevo International Airport. He could have left on another plane. There are even suggestions that he has taken shelter in the Ecuadorian Embassy in Moscow. What we do know is that, on this side of the Atlantic, efforts are being stepped up to demonize Snowden, and to delegitimize his claim to be a conscientious objector to the huge electronic-spying apparatus operated by the United States and the United Kingdom. Wyden and Udall to General Alexander: NSA Must Correct Inaccurate Statement in Fact Sheet. By Communications Office Today, Senators Wyden and Udall wrote to General Keith Alexander urging him to correct inaccurate and misleading statements in the NSA's recently released fact sheet on Section 702 of Foreign Intelligence Survelliance Act (FISA). "In our judgement this inaccuracy is significant, as it portrays protections for Americans' privacy being significantly stronger than they actually are," wrote Wyden and Udall.
Full text of the letter & fact sheet are below: Wyden and Udall Letter to General Alexander on NSA's Section 702 Fact Sheet Inaccuracy. 2 Senators Say the NSA Is Still Feeding Us False Information - Conor Friedersdorf. How can a democratic republic function when the bureaucrats are constantly misleading the people? Senator Ron Wyden departs after a full-Senate briefing by Director of the National Security Agency General Keith Alexander. (Reuters) President Obama avows that he welcomes a debate about the NSA, privacy, and national security.
Before Edward Snowden's leak, Americans lacked the information necessary for that debate; Obama would strongly prefer that we were still oblivious to his domestic surveillance activities. Maps: Senators who voted to expand NSA’s power. Senate intelligence leaders say phone surveillance is ‘lawful’ NSA PRISM program taps in to user data of Facebook, Yahoo and others. The National Security Agency has obtained direct access to the systems of Google, Facebook, Apple and other US internet giants, according to a top secret document obtained by the Guardian. The NSA access is part of a previously undisclosed program called Prism, which allows officials to collect material including search history, the content of emails, file transfers and live chats, the document says. Glenn Greenwald on the NSA and PRISM: "It's well past time that we have a debate about whether that's the kind of country and world in which we want to live.
On the heels of Thursday's news that revealed government agencies have been using a secret program to collect various types of data from some of the largest digital companies – including Google, Apple, and Facebook – so as to monitor Americans communications, "Piers Morgan Live" invited Glenn Greenwald to offer his perspective. The NSA Is Building the Country's Biggest Spy Center (Watch What You Say) Photo: Name Withheld; Digital Manipulation: Jesse Lenz. 10 Questions: Warrantless Wiretaps. US gov't defends NSA surveillance, slams 'reprehensible' journalists. After media outlets published "top secret" court orders which allow the U.S.
National Security Agency (NSA) to vacuum up millions of Verizon customer details and mine data from top technology firms, the U.S. Director of National Intelligence has hit back, claiming the reports have "numerous inaccuracies" and everything is perfectly legal. First obtained by The Guardian , the original report documented a court order which forced U.S. carrier Verizon to hand over call system data to the U.S. National Security Agency (NSA) on an "ongoing, daily basis. " PRISM Is Also Product From Palantir. U.S., British intelligence mining data from nine U.S. Internet companies in broad secret program.
What Is PRISM? What Is PRISM?