

Malware Analysis Tutorials: a Reverse Engineering Approach - Cодержание (Перевод Prosper-H, coldfire, ximera) Corkami - reverse engineering experiments and documentations. About Corkami - sources & PoCs - posters - order prints 2015/01/21 PNG Merge, a script to store several images in the same PNG 2014/01/28 Preserving arcade games 2014/01/29 Funky file formats I covered enough formats to get a complete calendar !
Mini. Unwind/unwind at master · evanw/unwind. SWF Investigator / Code / [r11] SWF Investigator. Recent Updates May 22, 2013 — Preview 5 of the SWF Investigator is now available.
This adds support for new SWF tags and contains bug fixes. Download SWF Investigator Preview 5 Perform quick, comprehensive, analysis of SWF applications Adobe® SWF Investigator is the only comprehensive, cross-platform, GUI-based set of tools, which enables quality engineers, developers and security researchers to quickly analyze SWF files to improve the quality and security of their applications. VERA - Cyber Security Research. Java_opcodes.pdf - corkami - JVM opcodes - reverse engineering experiments and documentations. Jsunpack-n - A generic JavaScript unpacker. Py2exe-extract - Extract python code_objects from executable file. Peepdf - PDF Analysis Tool. Whats is this?
UsageHow does it work? More info Google code project Download it! Follow peepdf on Twitter! What is this? Peepdf is a Python tool to explore PDF files in order to find out if the file can be harmful or not. [Python] ttfFromDocx. PDF Tools. I produced screencasts for my pdfid and pdf-parser tools, you can find them on Didier Stevens Labs products page. There are translations of this page, see bottom. pdf-parser.py This tool will parse a PDF document to identify the fundamental elements used in the analyzed file. Static analysis of a CVE-2011-2462 PDF exploit. CVE-2011-2462 was published more than one month ago.
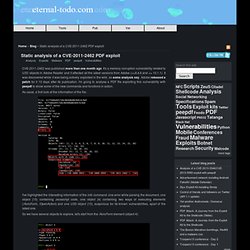
It's a memory corruption vulnerability related to U3D objects in Adobe Reader and it affected all the latest versions from Adobe (<=9.4.6 and <= 10.1.1). It was discovered while it was being actively exploited in the wild, as some analysis say. Adobe released a patch for it 10 days after its publication. I'm going to analyse a PDF file exploiting this vulnerability with peepdf to show some of the new commands and functions in action. As usual, a first look at the information of the file: I've highlighted the interesting information of the info command: one error while parsing the document, one object (15) containing Javascript code, one object (4) containing two ways of executing elements (/AcroForm, /OpenAction) and one U3D object (10), suspicious for its known vulnerabilities, apart of the latest one.
So we have several objects to explore, let's start from the /AcroForm element (object 4): So we take a look at page 3 of the document: Radare. And finally... Bokken 1.5. Once the development has finished, radare2 0.9 has been released and the project site has been updated, the moment has arrived: Bokken 1.5 is here!
Take a look at the previous post to read some of the new features of this release and keep reading to see most of them in detail; for the rest... install Bokken and enjoy them! As mentioned before, one of the most important features added is the support of radare2 as backend. So now Bokken can work with either Pyew or Radare, each one having its own advantages and drawbacks. Most of the development efforts for this release have gone to improve the GUI in order to make it cleaner and easier to use.
The disassembly view has gained in interactivity, and now it features, among others: Code navigation by clicking over: functions, basic blocks, address, section names, etc...Add comments, view and follow xrefs or view opcode information by right-clicking on a code line. Windows Disassembler. Download PEBrowse64 Professional. for Vista64, Windows 7 (64-bit) and Windows 8 (64-bit)MSI file, 1,193 KBSHA256: 65ebc51dcf3ed5d184dfce2d8d2777c3a861206c6cc940ab5625b06bd43e9195PEBrowse Professional. for all versions of WindowsZIP file, 1,665 KBSHA256: 6465a1585938327cc03569785aca0b6a74ef7599425dbb006bc81eec4c3d4fc6 PEBrowse64 Professional (v5.2) is a 64-bit executable and requires the .NET framework.

It will display both Win32 and Win64 executables, native, managed and mixed. IDA: About. What is IDA all about?

IDA is a Windows, Linux or Mac OS X hosted multi-processor disassembler and debugger that offers so many features it is hard to describe them all. Just grab an evaluation version if you want a test drive. IDA + gdb remote debugging. In part 2 of this series we found a SQL injection vulnerability using static analysis.
However, it is often advantageous to debug a target application, a capability that we’ll need when working with more complex exploits later on. In this segment we won’t be discovering any new vulnerabilities, but instead we will focus on configuring and using our debugging environment. For this we will be using Qemu and the IDA Pro debugger. If you don’t have IDA you can use insight/ddd/gdb instead, but in my experience IDA is far superior when it comes to embedded debugging. Our target binaries from the TEW-654TR are little endian MIPS, so we need an emulator in order to run them on our host system. But before you go grab the latest version of Qemu from your distro’s repositories, keep in mind that our MIPS binaries are dynamically linked to MIPS libraries. BinDiff. Zynamics BinDiff uses a unique graph-theoretical approach to compare executables by identifying identical and similar functions Description BinDiff is a comparison tool for binary files, that assists vulnerability researchers and engineers to quickly find differences and similarities in disassembled code.

With BinDiff you can identify and isolate fixes for vulnerabilities in vendor-supplied patches. You can also port symbols and comments between disassemblies of multiple versions of the same binary or use BinDiff to gather evidence for code theft or patent infringement. Screenshots Screenshot 1: Changed functions are displayed in an easy-to-understand symmetric layout Screenshot 2: Changes in instructions are shown in yellow, new instructions are shown in red. DarunGrim: A Patch Analysis and Binary Diffing Tool. Scriptable version of DarunGrim3. Binwalk - Firmware Analysis Tool. As of 2013-11-15, binwalk is no longer maintained on GoogleCode.
The code repository has moved to and all future releases and updates will be posted at binwalk.org. The GoogleCode repository remains for historical purposes only. Binwalk is a firmware analysis tool designed to assist in the analysis, extraction, and reverse engineering of firmware images and other binary blobs. It is simple to use, fully scriptable, and can be easily extended via custom signatures, extraction rules, and plugin modules. Binwalk supports various types of analysis useful for inspecting and reverse engineering firmware, including: PEdump. NtQuery/Scylla. [android] wuntee/otertool - GitHub. Powered by Google Docs. NETZOB: A Protocol Reverse Engineering Tool. Hyperdbg - A kernel debugger that leverages hardware-assisted virtualization.
Free .NET decompiler. CODEGATE 2012 Prob #1 - /var/log/smokedchicken.log. I've lost my source code! Fortunately, I have a test program. But, Test program is not perfect. Please, I need your help. Дан архив 49F69C55C47B4AA87059F3EEF391F5A7 с запакованным ASProtect исполняемым файлом и запароленным ZIP-архивом внутри. Распакуем ASProtect. Загружаем в Olly, на точке входа видим стартовый код ASProtect: Ставим бряк на GetProcAddress и хардварный на исполнение на 00401000.