

Advanced authentication in WebSphere Application Server. Managing user authenticity and privileges in a distributed application server environment Keys Botzum, Bill Hines, Paul Ilechko, Messaoud Benantar, and Peter BirkPublished on August 17, 2005 From the IBM WebSphere Developer Technical Journal.
In the past, IBM WebSphere Application Server had a rigid authentication model that made it challenging to support complex or unusual requirements. This situation was recently addressed with a new, highly customizable authentication framework based upon Java Authentication and Authorization Service (JAAS), extended with features that specifically address the requirements of managing user authenticity and privileges in a distributed application server environment. This new framework defined for JAAS support in WebSphere Application Server includes: plus a number of beneficial extensions to the security programming model.
This article will describe these new features in detail. Authentication overview What version should you use? ADFS 2.0 Step-by-Step Guide: Federation with IBM Tivoli Federated Identity Manager. Published: March 24, 2011 Updated: March 24, 2011 Applies To: Active Directory Federation Services (AD FS) 2.0 This guide provides step-by-step instructions for configuring a basic identity federation deployment between Microsoft® Active Directory® Federation Services 2.0 (AD FS 2.0) and IBM Tivoli Federated Identity Manager (TFIM) by using the Security Assertion Markup Language (SAML) 2.0 ( protocol, specifically its Web Browser SSO Profile and HTTP POST binding.
Throughout this document, there are numerous references to federation concepts that are called by different names in AD FS 2.0 and SAML documentation. The following table assists in drawing parallels between the two concepts. In this deployment, you have the option of configuring either (or both) of two scenarios: Configure AD FS 2.0 as the Claims Provider and TFIM as the Relying Party TFIM as claims/identity provider and AD FS 2.0 as relying party/service provider.
Tivoli Federated Identity Manager Business Gateway and ASP.NET authentication. Introduction This article requires that you are familiar with FIM Enterprise or FIM-BG and the SAML 1.0/1.1/2.0 federated single sign-on technologies.
You should be comfortable with configuring a federation using the FIM management console, and have a basic understanding of the role of the FIM plug-in for IIS V6 that ships with FIM-BG. For background material on FIM-BG and the FIM plug-in for IIS, please see the FIM-BG product documentation, which is also linked from the Resources section.
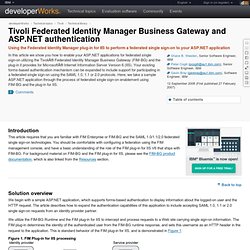
Back to top Solution overview We begin with a simple ASP.NET application, which supports forms-based authentication to display information about the logged-on user and the HTTP request. We utilize the FIM-BG Runtime and the FIM plug-in for IIS to intercept and process requests to a Web site carrying single sign-on information. Figure 1. The user authenticates to the identity provider environment.The identity provider's federated SSO system returns a security token to the user. The sample application <? Shane Weeden. This article describes an advanced Tivoli Federated Identity Mananager configuration model concerning mapping modules for single sign-on federations.
The article is applicable to readers who are already familiar with Tivoli Federated Identity Manager and it's federated SSO support. In particular I will present a technique to perform identity and attribute mapping via a second WS-Trust callout to another STS chain. It is important to understand circumstances when this might be useful to see if such a method might be applicable to your TFIM installation. Consider a use case where you have a single sign-on federation (SAML 1.1 Service Provider in this example, but that's not important) with multiple partners.
One option that I know some folks have explored is to make use of the Runtime Custom Property STS.showSSOChains = true, then use the console to modify the structure of the underlying built-in trust chains. My advice: PLEASE AVOID MODIFYING THE BUILT-IN SSO CHAINS!! Securing a composite business service delivered as a software-as-a-service: Part II, Supporting identity propagation (enterprise and federated SSO) and authorization.
Introduction A composite business service (CBS) integrates a set of fine-grained services with a business process using a Service Oriented Architecture (SOA).
A CBS is often delivered as a software-as-a-service (SaaS). A CBS delivered as a SaaS introduces many new challenges for security, for example identity propagation across services spanning multiple tiers, security domains, and legacy applications. Part 1 presented example non-functional security requirements for the Jivaro CBS SaaS application. And it demonstrated how multi-tenancy security requirements in Jivaro can be met using Tivoli Directory Server and Directory Integrator. In Part 2, Tivoli Access Manager, Tivoli Federated Identity Manager (TFIM) (including the Security Token Service), and Tivoli Federated Identity Manager Business Gateway are being used to implement additional security (identity propagation and authorization) scenarios in the Jivaro proof of concept (PoC) SaaS application. Securing a composite business service delivered as a software-as-a-service: Part I, secure multi-tenancy with WebSphere Portal Server.
Introduction.
User provisioning with Tivoli Identity Manager. Example implementation overview Example customer scenario.
Using Tivoli Access Manager for eBusiness WebSEAL without a user registry. Prequisite Knowledge This article assumes a basic familiarity with: Tivoli Access Manager for eBusiness WebSEALThe WebSEAL external authentication interface (EAI)The Tivoli Federated Identity Manager runtime, including the Security Token ServiceJ2EE and Java™ programming of servlets To implement and deploy the scenario described in this article, you need a configured TAMeB WebSEAL server, and a configured Tivoli Federated Identity Manager runtime.
Overview of the solution The solution architecture for using WebSEAL without a dedicated TAMeB user registry leverages a particular feature of the TAMeB external authentication interface (EAI). Simple, separate text headers conveying the short TAMeB username for the user and other extended attributes. The next question is then - how does one build an EPAC? Fortunately there is another method available to build a TAMeB EPAC that does not require consultation of the TAMeB user registry. The overall architecture of the solution is shown in Figure 1:
Auth10/auth10-java. Fediz. Overview Apache CXF Fediz is a subproject of CXF.

Fediz helps you to secure your web applications and delegates security enforcement to the underlying application server. With Fediz, authentication is externalized from your web application to an identity provider installed as a dedicated server component. The supported standard is WS-Federation Passive Requestor Profile. Fediz supports Claims Based Access Control beyond Role Based Access Control (RBAC). News. WIF : Is there a Java Equivalent? Been asked this question a million times and now I have an answer of sorts.
If by WIF, you mean WS-Federation, then mosey on over to: Apache CXF Fediz: An Open-Source Web Security Framework This supports: WS-Federation 1.0/1.1/1.2 SAML 1.1/2.0 Tokens Custom token support Publish WS-Federation Metadata document Role information encoded as AttributeStatement in SAML 1.1/2.0 tokens Claims information provided by FederationPrincipal interface However, if by WIF by mean the FAM / SAM / CAM functionality then the jury is still out. There is no direct Java replacement library for WIF.