

Official Website. Public Key for PGP Signing Starting from v3.3.4 all source tarballs and binaries are signed.

The key currently used is: 4096R/5B7CC9A2 Fingerprint: D8F3DA77AAC6741053599C136E4A2D025B7CC9A2 You can also download it from here Previously the following key was used to sign the v3.3.4 source tarballs and v3.3.4 Windows installer only: 4096R/520EC6F6 Fingerprint: F4A5FD201B117B1C2AB590E2A1ACCAE4520EC6F6 Windows 7 / 8 / 10 Current stable version: qBittorrent v4.2.5 Download link: 32-bit & 64-bit installers / PGP signature (FossHub) Mirror link: 32-bit installer / PGP signature (SourceForge) Mirror link: 64-bit installer / PGP signature (SourceForge) Hacker Noon.
TCP/IP Fingerprinting Methods Supported by Nmap. Nmap OS fingerprinting works by sending up to 16 TCP, UDP, and ICMP probes to known open and closed ports of the target machine.
These probes are specially designed to exploit various ambiguities in the standard protocol RFCs. Then Nmap listens for responses. Dozens of attributes in those responses are analyzed and combined to generate a fingerprint. Every probe packet is tracked and resent at least once if there is no response. All of the packets are IPv4 with a random IP ID value. The following sections are highly technical and reveal the hidden workings of Nmap OS detection. Even the best of us occasionally forget byte offsets for packet header fields and flags. This section describes each IP probe sent by Nmap as part of TCP/IP fingerprinting. Sequence generation (SEQ, OPS, WIN, and T1) A series of six TCP probes is sent to generate these four test response lines.
Each probe is a TCP SYN packet to a detected open port on the remote machine. TCP explicit congestion notification (ECN)
Security Relevant. Node.js and MongoDB - Getting started with MongoJS. HEADS UP!
This article was written for an older version of node. More up-to-date information may be available elsewhere. It won't be an exaggeration if one claims that in the past few months Node.js and MongoDB have literally taken the software and web industries by storm. Not just bleeding-edge startups but even medium and large enterprises are leveraging these two technologies to deliver a better experience to their users by build more capable, performant and scalable apps.
So what is Node.js? Node.js is a platform built on Chrome's JavaScript runtime for easily building fast, scalable network applications. ..and what is MongoDB? MongoDB is a scalable, high-performance, open source NoSQL database.
Response. SysSec: About. Home. PGP word list. The PGP Word List ("Pretty Good Privacy word list", also called a biometric word list for reasons explained below) is a list of words for conveying data bytes in a clear unambiguous way via a voice channel.
They are analogous in purpose to the NATO phonetic alphabet used by pilots, except a longer list of words is used, each word corresponding to one of the 256 unique numeric byte values. History and structure[edit] The PGP Word List was designed in 1995 by Patrick Juola, a computational linguist, and Philip Zimmermann, creator of PGP.[1][2] The words were carefully chosen for their phonetic distinctiveness, using genetic algorithms to select lists of words that had optimum separations in phoneme space. The candidate word lists were randomly drawn from Grady Ward's Moby Pronunciator list as raw material for the search, successively refined by the genetic algorithms.
Examples[edit] Each byte in a bytestring is encoded as a single word. Topmost Istanbul Pluto vagabond References[edit] PGP word list. Index of /archives/tgz. Index of /archives/tgz Name Last modified Size Description.
Dorkbot – Scan Google search results for vulnerability. – Security List Network™ LEGAL DISCLAMERThe author does not hold any responsibility about the bad use of this script, remember that attacking targets without prior concent its ilegal and punish by law, this script was build to show how resource files can automate tasks. dorkbot is a modular command-line tool for performing vulnerability scans against a set of webpages returned by Google search queries in a given Google Custom Search Engine.
It is broken up into two sets of modules: + Indexers – modules that issue a search query and return the results as targets + Scanners – modules that perform a vulnerability scan against each target Targets are stored in a local database upon being indexed. Once scanned, any vulnerabilities found by the chosen scanner are written to a standard JSON report file. Indexing and scanning processes can be run separately or combined in a single command. PHP security exploit - list content of remote PHP file?
[HYP3RLINX] Webmin 1.850 - Multiple Vulnerabilities. [+] Credits: John Page (aka hyp3rlinx) [+] Website: hyp3rlinx.altervista.org [+] ISR: ApparitionSec Vulnerability summary The following advisory describes three (3) vulnerabilities found in Webmin version 1.850.

Bugtraq: Multiple vulnerabilities in OpenText Documentum Content Server. Bugtraq mailing list archives Multiple vulnerabilities in OpenText Documentum Content Server.
Google Hacking Archives - Hacking Articles. First login in your Gmail account than Go to google.com and search for what you want.
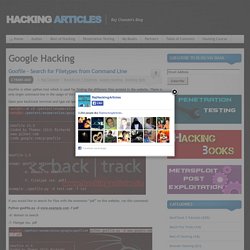
You got the search results and you saw that domain which you don’t want to see again in your search results. Click the browser’s back button from the website, which will give you the previous search results, but this time you can see a new link as shown in below image. Now you will be able to see “Block all Feature to this Website. Manage your blocked sites by clicking on the above ‘Manage blocked sites’ link or log-in to google and accessing the reviews URL. How To Search On Google Like Elite Hackers. Google is best search engine in the world.
Actually people think that Google's popularity is because of its simple and fast searching interface but friends, its more popular because it has rich operators and query support that will make your searching experience even better. Most of us doesn't know which operators are supported by Google and if they know some of them, they doesn't know how actually these operators work and enrich our searching practice. Finding Serial Key Of Any Software Using Simple Google Trick. Most of you download and use pirated software from torrents or any such other sites, but sometime it gets very difficult to find serial key of those softwares. I will make it easy for you by showing you simple yet very intersting google trick which will allow you to find serial key of any software very easily How To Find Serial Key Of Any Software ? The key 94FBR is a part of Office 2000 Pro CD activation key that is widely distributed as it bypasses the activation requirements of Office 2000 Pro.
By searching for 94fbr and the product name, you are guarantee that the pages that are returned are pages dealing specifically with the product you're wanting a serial for. Follow simple steps given below to learn this trick. Finding Serial Key Of Any Software Using Simple Google Trick.