

OWASP Top 10 for .NET developers part 2: Cross-Site Scripting (XSS) In the first post of this series I talked about injection and of most relevance for .NET developers, SQL injection.

This exploit has some pretty severe consequences but fortunately many of the common practices employed when building .NET apps today – namely accessing data via stored procedures and ORMs – mean most apps have a head start on fending off attackers. Cross-site scripting is where things begin to get really interesting, starting with the fact that it’s by far and away the most commonly exploited vulnerability out there today. Last year, WhiteHat Security delivered their Website Security Statistics Report and found a staggering 65% of websites with XSS vulnerabilities, that’s four times as many as the SQL injection vulnerability we just looked at. But is XSS really that threatening? Isn’t it just a tricky way to put alert boxes into random websites by sending someone a carefully crafted link?
Preventing XSS in ASP.NET Made Easy - Lock Me Down. ASafaWeb - Automated Security Analyser for ASP.NET Websites. OWASP. SQL Injection Cheat Sheets. Troy Hunt. Hack Yourself First - Troy Hunt. Ethical Hacking Tutorials, Tips and Tricks. Free Tutorials, How to's. Hack This Site! Hacking Techniques in Wireless Networks. Prabhaker Mateti Department of Computer Science and EngineeringWright State UniversityDayton, Ohio 45435-0001 This article is scheduled to appear in “The Handbook of Information Security”, Hossein Bidgoli (Editor-in-Chief), John Wiley & Sons, Inc., 2005. 1.
Introduction. 2 2. 2.1 Stations and Access Points. 3 2.2 Channels. 4 2.4 Infrastructure and Ad Hoc Modes. 4. Computer Security. I Love Free Software5 Best Free Network Packet Sniffer. Here are 5 Best free network packet sniffers that does a fantastic job of packet sniffing.
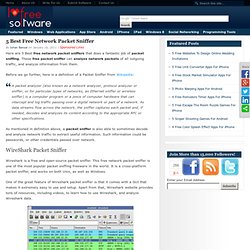
These free packet sniffer can analyze network packets of all outgoing traffic, and analyze information from them. Before we go further, here is a definition of a Packet Sniffer from Wikipedia: A packet analyzer (also known as a network analyzer, protocol analyzer or sniffer, or for particular types of networks, an Ethernet sniffer or wireless sniffer) is a computer program or a piece of computer hardware that can intercept and log traffic passing over a digital network or part of a network.
As data streams flow across the network, the sniffer captures each packet and, if needed, decodes and analyzes its content according to the appropriate RFC or other specifications. The Original Magazine of the Linux Community. Network Defense and Countermeasures: Assessing System Security. Perhaps the most critical step in assessing any network is to probe the network for vulnerabilities.

This means using various utilities to scan your network for vulnerabilities. Some network administrators skip this step. They audit policies, check the firewall logs, check patches, and so on. However, the probing tools discussed in this section are the same ones that most hackers use. If you want to know how vulnerable your network is, it is prudent to try the same tools that an intruder would use. Port scanning: This is a process of scanning the well-known ports (there are 1024) or even all the ports (there are 65,535) and seeing which ports are open. Change NTFS file and folder permissions. Hi Fellows!
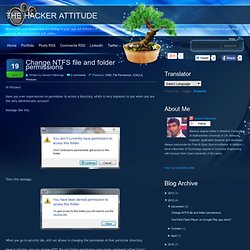
Have you ever experienced no permission to access a directory, which is very impotent to you when you are the only administrator account? Message like this, Then this message, When you go to security tab, still not allows to changing the permission of that particular directory. Here is solution, you can change NTFS file and folder permissions using magic command called "icacls".Step1:Open command prompt and type following command to see the permissions list (discretionary access control lists - DACLs)icacls [folder or filepath]oricacls [folderpath] *
How to Stop Hackers from Invading Your Network: 13 Steps. Edit Article Unethical hackers (in bad sense of this word) are always looking for weaker points in a network system to hack the security system of your company and get a hold of confidential and new information.
Some "black-hat hackers" derive a vicarious pleasure from wreaking havoc on security systems and some hackers do it for money. Whatever may be the reason, malicious hackers are giving nightmares to companies and organizations of almost all sizes. Especially, large corporate houses, banks, financial institutions, security establishments are favorite targets for hackers. However, this menace can be prevented to a great extent if proper security measures are taken at the right time. Ad Steps. I hacked my secure wireless network: here’s how it’s done.
Wireless networks are everywhere; they are widely available, cheap, and easy to setup.
To avoid the hassle of setting up a wired network in my own home, I chose to go wireless. After a day of enjoying this wireless freedom, I began thinking about security. How secure is my wireless network? I searched the Internet for many days, reading articles, gathering information, and participating on message boards and forums. I soon came to the realization that the best way for me to understand the security of my wireless network would be to test it myself. Trend Micro Site Safety Center. Networking.