

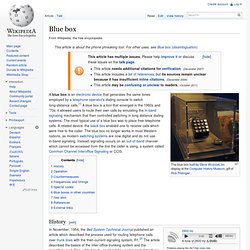
Mobile Phone Surveillance. Blue box. History[edit] In November, 1954, the Bell System Technical Journal published an article which described the process used for routing telephone calls over trunk lines with the then-current signaling system, R1.[2] The article described the basics of the inter-office trunking system and the signalling used.
Phreaking. The term phreak is a portmanteau of the words phone and freak, and may also refer to the use of various audio frequencies to manipulate a phone system.
Phreak, phreaker, or phone phreak are names used for and by individuals who participate in phreaking. Because identities were usually masked, an exact percentage of prevalence cannot be calculated. History[edit] Phone phreaking got its start in the late 1950s. Its golden age was the late 1960s and early 1970s. Switch hook and tone dialer[edit] Android NFC 'hacking' is ingenious, but not yet dangerous. The Black Hat conference takes place in Las Vegas this week, where hackers, security experts and representatives from major companies meet to discuss all things relating to information security.

If you're following the news out of the conference today, you may have come across reports of a new security vulnerability in Android (and NFC-enabled Meego phones) that could allow a malicious NFC (near-field communication) tag to beam malware directly onto your phone. Sounds terrifying, right? Now hackers can take over your smartphone without you even doing anything. But as is always the case with these kinds of security issues, it's not as simple as it seems. And this NFC 'hack,' sexy and technically impressive as it is, isn't really anything particularly scary to regular smartphone users. Read on to find out why. First off, we should quickly explain what NFC actually is. Bottom line -- if you enjoy using NFC on your Android phone from time to time, you're safe to continue doing just that. Asterisk. Phone hacking. Phone hacking is the practice of intercepting telephone calls or voicemail messages, often by accessing the voicemail messages of a mobile phone without the consent of the phone's owner.
The term came to prominence during the News International phone hacking scandal, in which it was alleged (and in some cases proved in court) that the British tabloid newspaper the News of the World had been involved in the interception of voicemail messages of the British Royal Family, other public figures, and the murdered schoolgirl Milly Dowler.[1] Risks[edit] Although any mobile phone user may be targeted, "for those who are famous, rich or powerful or whose prize is important enough (for whatever reason) to devote time and resources to make a concerted attack, there are real risks to face. Locking Memory on EPC Gen 2 RFID Tags - RFID insider. Locking the memory on EPC GEN 2 compliant RFID Tags is an often misunderstood process.

Many think that it is simply a matter of changing the access password to a non-zero value (the default for Gen 2 tags) and then the tag is ‘locked’ but this is not the case. This posting will review how tag locking works for EPC RFID tags and show you how to lock the Impinj Monza tags using .NET version 1.0.0.6 of the Octane Software Development Kit (SDK). An EPC GEN 2 tag has two separate passwords — an access password and a kill password; each are 32 bits, and are stored in the reserved bank (bank 00) of the tag memory. When a tag is singulated, it enters one of two states: 1. A tag in the open state can be moved to secured by providing non-zero access password. The key thing to remember is that assigning a non-zero access password does not, in itself, prevent anyone with a GEN 2 RFID reader from reading or changing data on the tag.
Hack. LISTS. Hackery. Hacking. Hack Tools. Phrack Magazine. PhreakVids.com - Videos Related To Phreaking. Phreaking boxes. Phreaking boxes are devices used by phone phreaks to perform various functions normally reserved for operators and other telephone company employees.
Most phreaking boxes are named after colors, due to folklore surrounding the earliest boxes which suggested that the first ones of each kind were housed in a box or casing of that color. However, very few physical specimens of phreaking boxes are actually the color for which they are named. Today, most phreaking boxes are obsolete due to changes in telephone technology. List of phreaking boxes[edit] This is not a comprehensive list. This list of boxes does not include wiretapping "bugs", pirate broadcasting apparatus or exploits involving computer security.
See also[edit] External links[edit] 5 Android Apps to Earn Real Money for Completing Little Tasks. With the increasing usage in smartphones, the amount we spend on different apps and micro-transactions are also increasing.
But have you ever thought of earning a few bucks or other rewards with your smartphone? For Android users, there are quite a few apps that help you earn a few quick bucks by completing simple tasks like taking photos, watching trailers, completing surveys, etc. Granted, you won’t be able to make a living out of these apps, but they can surely get you a coffee or two, or even pay for the next app that you are buying.
If you are wondering about them, here are some of the best Android apps that can earn you real money or other rewards for completing little tasks. MintCoins is one of the famous apps that pays you for completing little and simple tasks such as watching video advertisements, downloading free apps, completing surveys, playing free games, subscribing to websites, etc. Rewardable is a relatively new app which pays you for completing the listed tasks.