

Publications and Presentations. Voter Database Leak Exposes 154 Million Sensitive Records. Privacy International. A map of the interconnections between computers generated by running trace routes from a single computer.
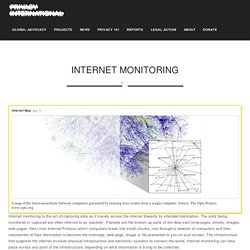
Source: The Opte Project, www.opte.org Internet monitoring is the act of capturing data as it travels across the internet towards its intended destination. The units being monitored or captured are often referred to as ‘packets’. Packets are the broken up parts of the data sent (messages, emails, images, web pages, files) over Internet Protocol which computers break into small chunks, rout through a network of computers and then reassemble at their destination to become the message, web page, image or file presented to you on your screen. The infrastructure that supports the internet involves physical infrastructure and electronic systems to connect the world. Glimmerglass has the capability to capture traffic as it comes from International Gateways and Submarine Landing Stations. HI2 refers to Intercept Related Information, or metadata as it is more commonly known.
Tools: Security - Forensics - Pentesting - Ethical Hacking. Free Tools: Online Investigation & Brand Protection – ICMS Worldwide. Recommended Brand Protection Solutions For Your Industry This list of online investigation tools has been compiled by ICMS- A global service providing anti-counterfeit, brand protection solutions for High risk world regions such as China, Southeast Asia, Latin America, Russia and East Europe.
Most of the tools below require some basic computer skills. We hope you can put them to good use! —Disclaimer: Please use these tools with caution. They are created and hosted by third parties with absolutely no affiliation with ICMS. Mapping Google Maps Engine Lite Link: Create your own detailed maps, markers and labels. BatchGeo Link: This is another good tool for making your own custom maps. Web Searching Google Advance Search Link: This is just like a regular google search but with a lot more filters to help you find what you’re looking for. Google Image Search Link: and (Advanced) Match up images or find webpages that are using your own. Deep Research and Infringement Detection Productivity. CREATE BATCH VIRUS AND SEND TO YOUR FRIENDS FOR FUN. Send Anonymous Emails: 20 Sites To Keep Your Identity Hidden.
The first question to answer here is why go for anonymous email when there are plenty of premium featured and free email services such as Gmail, Outlook and Yahoo!
Mail available? Well, privacy and anonymity is a digital right — our digital right. These email services are ‘free’ because of the advertisements. Although deemed necessary evils, ads are mostly tailored for the visitor or service user, and to do that, service providers need your data to show you advertisements targeted to you and your user group. These are ads that you are most likely to click and/or follow. Moreover, the disclosure of the motives of secret agencies and their top-secret internet-censoring programs (such as PRISM) has raised concerns among digital privacy advocates.
Recommended Reading: VPN Protocols: Preserving Your Sensitive Information Online Anonymous email forms the basic foundation of anonymity over the web.
Security. Covert Surveillance Technologies. Intelink%20Basic%20presentation.pdf. Logout page. INTELINK. Pravail® Security Analytics. Revealing attacks in real-time within your network Today’s breed of attacker uses stealthy and sophisticated methods to penetrate an organization’s perimeter.
The indicators of compromise are often impossible to identify before it’s too late. In order to really understand subtle, advanced targeted attacks, enterprises need a complete record of all network traffic. Pravail Security Analytics uses big data technologies that lower the barrier to entry for organizations looking to deploy and operate world-class security analytics. You don’t need to spend large amounts of capital, and you don’t need to spend months on complex deployments and integration. Interact with your data like never before.
At Arbor, we have a fresh approach and a single vision – to provide a richer picture into your network and more security context – so you can solve problems faster and reduce the risk to your business. Revealing attacks in real-time within your network Interact with your data like never before. Database. Cybernetics.