

Hurry UP!! Get These Top 15 Udemy Courses For Free With These Coupon Code»(Verified) - VINSTECHS. Hello Guys, It’s ViNs, Today i got a Big deal for all of my Readers.
Yes, really it’s a Big deal, why because in the next 5 minutes you are going to get Top 15 Udemy Courses For free which costs 200$ and more. Crazy Right!!! Yo guys we are serious, we are giving you a Coupon Codes which are working crazily for Top 15 Udemy Courses related to Ethical HACKING, Android app development, Web Development, Animation, etc..
Kali LinuxTR l Türkçe Destek Platformu. A Google Credit Card Hack How-To Guide (White Hat) Preface If you know me, or have read my previous post, you know that I worked for a very interesting company before joining Toptal.
At this company, our payment provider processed transactions in the neighborhood of $500k per day. Part of my job was to make our provider PCI-DSS compliant—that is, compliant with the Payment Card Industry – Data Security Standard. It’s safe to say that this wasn’t a job for the faint of heart. At this point, I’m pretty intimate with Credit Cards (CCs), Credit Card fraud and web security in general. 1000 Popular Hacking tricks tutorials. How to Find the Wi-Fi Password of your Current Network [Windows, Android & Mac] WiFi is the most common way to connect to your network or you can say most feasible way to connect anywhere without any problem.
![How to Find the Wi-Fi Password of your Current Network [Windows, Android & Mac]](http://cdn.pearltrees.com/s/pic/th/password-current-network-135261567)
Most of the common problem of WIFI network is you easily forgot the WiFi password due to changing it more often. How to Stop Apps You're Not Using Anymore from Accessing Your Google Account. How to Stop Apps You're Not Using Anymore from Accessing Your Google Account Many apps and services that are available for Android can only work if they have access to your Google account.
Lab of a Penetration Tester: Practical use of JavaScript and COM Scriptlets for Penetration Testing. I have been following Casey Smith's brilliant work on JavaScript and COM Scriptlets.
After looking at his work, I started playing with the code. I was interested in developing easy and customizable ways to use JavaScript, SCT files, rundll32 and regvr32 for...well...interesting things. Hacking Tutorials. Hacker. Hacking. Attacks (Hacking) General Hacking. Brandieself added: Best Data Recovery Software for PC - The Vuze BlogThe Vuze Blog. People are addicted to photos and images.
So much in fact that Facebook reported more than 250 billion photos have been uploaded to its social platform with 350 million photos uploaded every day on average. With all of those photos of family, friends, vacations and memories that you’ve taken what would you do if you lost all of them? What if you forgot to create a backup of your digital photo albums?
What if your photo database became corrupted? Having a backup and recovery plan for your electronic media and personal files is important because, well, you just never know when or if something could go wrong. Wondershare can help you quickly recover more than 550 file formats from computer. The name says it all with this product. A great data recovery tool with a free version that allows you to recover up to 2GB at no cost. Have you ever had to use data recovery software? Photo credit: P1520761 via (license) The following two tabs change content below. HACKING AND CRACKING TOOLS. Hash Database. Hack/Search. Stades and acadimic. Brandieself added: The Vuze Blog - The Vuze Blog. This Gang of Flat Robots Can Autonomously Steal (Or Park) Your Car. The Inside Story of How British Spies Hacked Belgium's Largest Telco.
When the incoming emails stopped arriving, it seemed innocuous at first.
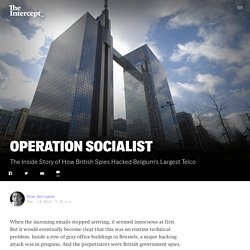
But it would eventually become clear that this was no routine technical problem. Inside a row of gray office buildings in Brussels, a major hacking attack was in progress. And the perpetrators were British government spies. It was in the summer of 2012 that the anomalies were initially detected by employees at Belgium’s largest telecommunications provider, Belgacom. But it wasn’t until a year later, in June 2013, that the company’s security experts were able to figure out what was going on. Last year, documents from National Security Agency whistleblower Edward Snowden confirmed that British surveillance agency Government Communications Headquarters was behind the attack, codenamed Operation Socialist. The full story about GCHQ’s infiltration of Belgacom, however, has never been told.
Gang of Romanian and Moldovan crooks stole £1.6m from ATMsSecurity Affairs. According to the police, a group of Romanian criminals has stolen nearly £1.6 million in series of jackpotting attacks.
The technique of the jack spotting was presented for the first time by the popular hacker Barnaby Jack in 2010 and it consists in a method to force ATMs to spit out cash. The_Pirates_Code.pdf. Dancho Danchev's Blog - Mind Streams of Information Security Knowledge: Historical OSINT - Profiling an OPSEC-Unaware Vendor of GSM/USB ATM Skimmers and Pinpads. On daily basis, I profile over a dozen of newly advertised (verified) vendors of ATM skimmers, indicating that this market segment is still quite successful, thanks to the overall demand for these 'tools-of-the-trade', allowing potential cybercriminals to enter the world of ATM skimming.
In this post part of the "Historical OSINT" series, I'll profile the underground market proposition of a vendor of GSM/USB ATM Skimmers and Pinpads, that appeared on my radar back in 2008, with an emphasis on the lack of OPSEC (Operational Security) applied by them, and the IP hosting changes of their main domain that took place throughout 2008, in particular, offer evidence of active multi-tasking on behalf of the same gang of cybercriminals. On 2006-04-06, darkforum.net (ICQ 16-09-61/160961) was registered using the alsaleh@gawab.com email. On 2009-01-07, the registration email changed to blanerds@hushmail.com. The Hacker's Toolkit. Computer Security. Pillage and Plunder.
Phreaking. Pentest distros. OFFENSIVE SECURITY. Hack tools. Atiucosem42012.