

Dsniff-n-mirror.pdf (application/pdf Object) Dsniff.pdf (application/pdf Object) A Hacker's Story: Let me tell you just how easily I can steal your personal data. A little bird told me people are pissed at Google.
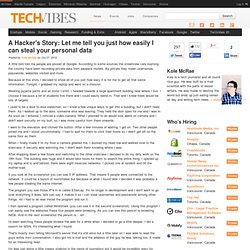
According to some sources the streetview cars roaming the country have been recording private data from people's routers. By private they mean usernames, passwords, websites visited and more. Because of this story I decided to show all of you just how easy it is for me to get all that same information. Tonight, I grabbed my laptop and went on a mission. Wearing pyjama pants and an ironic t-shirt, I headed towards a large apartment building near where I live. I used to be a door to door salesman, so I know a few unique ways to get into a building, but I didn't need them. I went to the elevators and clicked the button. When I finally made it to my floor a camera greeted me. After dropping down a few floors and switching to the other staircase I decided to do my dirty work on the 18th floor. If you look at the screenshot you can see 5 IP address.
The program you see those IP's in is called Ettercap. ECCE101.pdf (application/pdf Object) Seven_Deadliest_UC_Attacks_Ch3.pdf (application/pdf Object) Cracking-air.pdf (application/pdf Object) Bh-europe-03-valleri.pdf (application/pdf Object) 17-sam_bowne-hijacking_web_2.0.pdf (application/pdf Object) 2010JohnStrandKeynote.pdf (application/pdf Object) 18.Ettercap_Spoof.pdf (application/pdf Object) The_Magic_of_Ettercap.pdf (application/pdf Object) Arp_spoofing.pdf (application/pdf Object) Ettercap(ManInTheMiddleAttack-tool).pdf (application/pdf Object) ICTSecurity-2004-26.pdf (application/pdf Object) Ettercap_Nov_6_2005-1.pdf (application/pdf Object) Mallory is More than a Proxy.
25 August 2011 Raj Umadas and Mike Zusman of Intrepidus Group gave an amazing talk on Mallory last night at the Philadelphia OWASP chapter meeting.
At first glance Mallory seems like a simple tool, just a proxy application that sits on the wire. Closer inspection, however, reveals that Mallory offers functionality above and beyond traditional tools for packet inspection. Mallory looks like an exceptional tool that could be a valuable part of any software security assessor's toolkit. The ability of Mallory to pause, tamper, and play data makes it especially effective for monkeying with black box applications, but it also makes for a really fun tool! Raj Umadas and Mike Zusman of Intrepidus Group gave an amazing talk on Mallory last night at the Philadelphia OWASP chapter meeting.
Mallory solves a problem faced by many application security folks. Raj and Mike demonstrated several clever ways that you can use iptables to set up a transparent NAT proxy with a linux device. Thicknet: It does more than Oracle, Steve Ocepek securityjustice on USTREAM. Computers.