

A simple interface for OpenPGP email security. Anton Chuvakin Homepage. Anton Chuvakin, Ph.D., GCIA, GCIH, GCFA Information Security Publications. 10 Cryptography Mistakes Amateurs Make - Laura Diane Hamilton. On Tuesday I attended John Downey's talk at Braintree entitled "Cryptography Pitfalls.
" I learned a ton about cryptography and common cryptography mistakes. Cryptography is very complicated, difficult to understand, and perilously easy to get wrong. The #1 rule of cryptography is "Don't invent your own. " But even if you use existing components, there are myriad ways you can introduce subtle bugs that make your application dramatically less secure. Here are some of the ways — although this is far from complete! Mistake #1 — Improper or inadequate seeding of the random number generator In 2006, a bug was introduced to Debian (and Ubuntu) that broke the seeding of the random number generator.
Mistake #2 — Using the MD5 hashing algorithm We've known MD5 to be insecure since 1996. From wikipedia: The security of the MD5 hash function is severely compromised. Mistake #3 — Storing SHA1(password) in the database For passwords, it's better to use a unique salt for each account. Mistake #5 — Using DES. Microsoft PowerPoint - AppSec_IL_0706_Comsec_ShayZ_ Crypto 1_0_2 - C.ppt - OWASP_IL_0706_Comsec_ShayZ_Crypto_1_0_2.pdf. CSE 107: Introduction to Modern Cryptography.
2007spring:notes:lec18 [CS111] By Marshall Ha, Aaron Chen, Carlos Albuja, Sayyed Alireza Binesh Computer Security: Protect a computer against adversaries.
![2007spring:notes:lec18 [CS111]](http://cdn.pearltrees.com/s/pic/th/2007spring-notes-lec18-cs111-68995559)
A computer system performs actions on behalf of principals. Principals: A model of a user with some rights and privileges. Examples: Can a principal log in? The root/administrator often has all the rights and privileges that a computer system can grant. Complete Mediation Is every action performed by a correct principal? Authentication Is the request real? Authenticity: Request is authentic if it was made by a real principal. Authorization Is the request allowed? Policy: Request satisfies the policy if the principal has the rights and privileges required for the request. Computer security goals Positive goal (+): System should perform all authentic, authorized actions. These two goals cannot both be realistically met.1) Rather, our priority is robustness within the system. For some systems, performance is robustness. ASN.1 JavaScript decoder.
Usemos Linux: Cómo proteger tu información en Linux con Truecrypt. Artículo de Usemos Linux Truecrypt funciona del siguiente modo: montás el dispositivo virtual a través de Truecrypt y luego podés acceder a él como a cualquier otra carpeta de tu sistema.
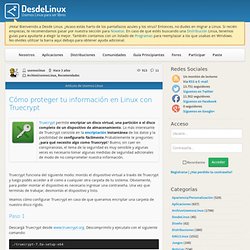
Obviamente, para poder montar el dispositivo es necesario ingresar una contraseña. Una vez que terminás de trabajar, desmontás el dispositivo y listo. Veamos cómo configurar Truecrypt en caso de que queramos encriptar una carpeta de nuestro disco rígido. Paso 1 Descargá Truecrypt desde www.truecrypt.org. . Esto es en el caso de una máquina 64bit y para la versión 7.0a. Paso 2 Al ejecutar Truecrypt, vas a ver la siguiente ventana. Hacé clic en el botón Create Volume. Paso 3 Una vez que se abre la nueva ventana, elegí la primera opción y hacé clic en Next. Paso 4 En esta ventana las opciones están bien explicadas. Paso 5 Aquí, tenés que elegir la ruta donde se guardará el archivo de Truecrypt. It Should Work... Breaking LFSR-based pseudo-random number generators January 22nd, 2011 · 14 Comments · hacking Another english post?

Yes because this is related to the first Security By Default Wargame that took place a few days ago. Congratulations to Int3pids! Cryptography. L’home dibuixat. Lifetimes of cryptographic hash functions. I've written some cautionary articles on using cryptographic hashes to create content-based addresses (compare-by-hash).
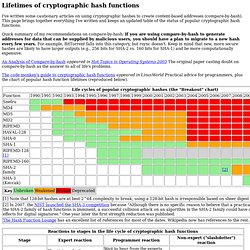
This page brings together everything I've written and keeps an updated table of the status of popular cryptographic hash functions. Quick summary of my recommendations on compare-by-hash: If you are using compare-by-hash to generate addresses for data that can be supplied by malicious users, you should have a plan to migrate to a new hash every few years. For example, BitTorrent falls into this category, but rsync doesn't. Keep in mind that new, more secure hashes are likely to have larger outputs (e.g., 256 bits for SHA-2 vs. 160 bits for SHA-1) and be more computationally expensive. An Analysis of Compare-by-hash appeared in Hot Topics in Operating Systems 2003 The original paper casting doubt on compare-by-hash as the answer to all of life's problems. Copyright 2007 - 2012 Valerie Aurora, licensed CC-BY-SA and don't forget the f'ing BY.