

Operating System Reviews (History, Facts, Versions and Screenshots) Why is my Windows PC running out of memory? I have a four-year-old Windows desktop that frequently runs really slowly with Task Manager showing that 80-90% of the physical memory is being used even when I’m not running any applications.
Svchost.exe seems to be the culprit, and sometimes RapportService.exe *32. I did a software spring clean as your column suggested but it didn’t help. My PC is an HP CQ5307UK desktop, with a 2.90GHz AMD Athlon II X3 435 processor and 3GB of memory running Microsoft Windows 7 and Norton Internet Security. I use Microsoft Office Pro and Mailwasher. Judith Modern versions of Windows – the ones that followed Windows XP – are designed to use all your PC’s physical memory: that’s what it’s there for. Official Home Page. Privacy in Outlook.com.
Use Location Services More Safely Factsheet. What is a single-use code? Security Essentials. About The Spamhaus Project. The Spamhaus Project is an international nonprofit organization whose mission is to track the Internet's spam operations and sources, to provide dependable realtime anti-spam protection for Internet networks, to work with Law Enforcement Agencies to identify and pursue spam and malware gangs worldwide, and to lobby governments for effective anti-spam legislation.

Founded in 1998, Spamhaus is based in Geneva, Switzerland and London, UK and is run by a dedicated staff of 38 investigators, forensics specialists and network engineers located in 10 countries. Spamhaus maintains a number of security intelligence databases and realtime spam-blocking databases ('DNSBLs') responsible for keeping back the vast majority of spam and malware sent out on the Internet. These include the Spamhaus Block List (SBL), the Exploits Block List (XBL), the Policy Block List (PBL) and the Domain Block List (DBL). DIY Electronica. Mobility Muse. Synchronize. Mobile Ideas. Windows research. Critical Flaws in Apple, Samsung Devices. Normally, I don’t cover vulnerabilities about which the user can do little or nothing to prevent, but two newly detailed flaws affecting hundreds of millions of Android, iOS and Apple products probably deserve special exceptions.
“More specifically, we found that the inter-app interaction services, including the keychain…can be exploited…to steal such confidential information as the passwords for iCloud, email and bank, and the secret token of Evernote,” the researchers wrote. The team said they tested their findings by circumventing the restrictive security checks of the Apple Store, and that their attack apps were approved by the App Store in January 2015. According to the researchers, more than 88 percent of apps were “completely exposed” to the attack. News of the research was first reported by The Register, which said that Apple was initially notified in October 2014 and that in February 2015 the company asked researchers to hold off disclosure for six months. iOS research. 9x reviews.
The Observing Self: Mysticism and Psychotherapy - Arthur J. Deikman. Reorient. Disability.gov. Disability.gov is a United States Government inter-agency web portal that provides access to comprehensive information about disability-related programs and services.
The site contains thousands of trusted resources, updated daily, from the federal government, educational institutions, non-profit organizations and state and local governments.[1] Disability.gov offers information for the more than 50 million Americans with disabilities. It is also a reliable resource for parents of children with disabilities, employers, workforce and human resource professionals, veterans, military families, caregivers and other community members. The site offers resources on ten key subjects: benefits, civil rights, community life, education, emergency preparedness, employment, health, housing, technology and transportation.[1] History[edit] References[edit] External links[edit] Disability.gov web portal. Disability.gov - Welcome to Disability.gov, the federal government website that provides quick access to national and local resources for people with disabilities, their families, friends and organizations that serve them.
2 Do. Copying Content from your iPod to your Computer - The Definitive Guide. Probably the single most frequently-asked question of our editors here at iLounge is “How do I copy music from my iPod back to my computer?” Although Apple’s iTunes program is very good at keeping a computer-based library synchronized to an iPod automatically, or for manually transferring tracks from your computer’s iTunes library onto your iPod, it provides extremely limited functionality for transferring information in the opposite direction—from your iPod back to your computer. One of the likely reasons for Apple to have taken such a restrictive approach to this is to combat piracy and thereby maintain good relations with the music labels that are currently selling their content via Apple’s iTunes Store. Dell Recovery Partition – Guide for Windows XP, Vista, 7, 8. This is a guide for recovering Dell computers using the recovery partition for the following versions of Windows: Windows XP, Windows Vista, Windows 7 and Windows 8.
Restoring Your Computer´s Software to the Factory Settings for Windows Vista. Free antivirus software Panda tops AV-Test's security rankings. Antivirus suites are only as good as their latest tests.
And in AV-test.org’s latest roundup for July and August, the usual suspects—BitDefender, Kaspersky, McAfee, and Symantec—came out on top. The same holds true for the free options. If you’re a cheapskate, you can download Panda Security’s free cloud antivirus and have a good chance that it will catch everything that the shadowy corners of the Web can throw at it—as it did in AV-test’s own proving ground. Artemis Trojan Removal Process (remove ArtemisTrojan) - PCHubs.com. December 27, 2013 – 5:31 pm Protect Yourself from Artemis Trojan - Remove rogue anti-spyware/anti-virus programs - Prevent trojans, hijackers & other malware infections - Use spyware helpdesk to resolve pesky malware Start Your Scan Now to Detect Artemis Trojan The ‘Artemis Trojan’ is a generic detection that usually signifies the presence of other obscure threat on your computer.

The ‘Artemis Trojan’ is not a real infection per se. How Did the Artemis Trojan Get onto My System? As previously mentioned, the ‘Artemis Trojan’ is not an infection per se. Profit driven Trojans (such as Police Trojans and CryptoLocker Trojans) typically encrypt files on the infected computer or block access to programs and demand a ransom. Top 10 Registry Tweaks that Power Up Windows. 8 Sleeping Positions & Their Effects On Health. In what position do you sleep most often?
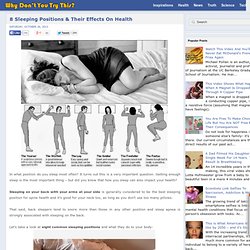
It turns out this is a very important question. Getting enough sleep is the most important thing – but did you know that how you sleep can also impact your health? Homeless man given $100 and secretly followed to see how he would spend it. Map: More than half of humanity lives within this circle. (Via Imgur) In yet another illustration of China's and India's enormous populations, Reddit recently surfaced the above population map, which claims more than half the world’s people live within a circle superimposed over a section of Asia.
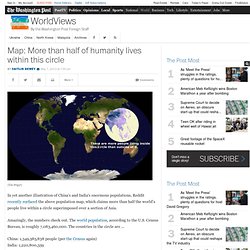
Amazingly, the numbers check out. The world population, according to the U.S. Testy.