

Kako otkriti FB profil iz URL adrese slike? Sigurno ste videli one “posebne” linkove slika sa fejsbuka koji se koriste da pokažete neku sliku vašeg prijatelja nekom drugom. Takvi linkovi vode samo do slike, ne i do profila vlasnika iste. Ali, postoji način da iz tog linka saznate čija je slika. Primer: Imamo ovakav link Mi ne znamo čija je to slika jer kad odemo na link vidimo samo sliku, ne i profil. Dakle, šta uraditi? Ako obratimo pažnju, link se sastoji od više grupa brojeva koji su razdvojeni donjom crticom ( _ ). Sad, brojimo sa leve strane treću grupu po redu. Dalje. U našem slučaju ceo link bi izgledao ovako: I to je link profila vlasnika slike. Isti princip je sa profilima. Uživajte. Stefan Marjanov Zaljubljenik u WordPress i Android. Aktiviraj HTML5 za sve klipove na Youtube-u. Surfujte internetom anonimno! U ovom postu ću vam pokazati kako da surfujete internetom potpuno anonimno! Kada je reč o skidanju muzike, filmova, programa za kompjuter itd.
Kada god bi nešto preuzeli s interneta „besplatno“ Vi ostavljate vaš trag, a to je IP adresa preko koje vas se može lako locirati i dovesti u neugodnu situaciju pred „državnom službom“. Svaki računar koje se spaja na internet poseduje određenu IP adresu. Šta je to Deep Web ? Naišao sam na jedan tekst o Deep Web-u za koji sam siguran da retko ko zna šta je to, pa sam odlučio da ga podelim sa vama. Ukratko: Deep Web je internet ispod “površine”. Ako bi se društvene mreže, razni sajtovi, video klipovi, itd. nalazili na površini, onda se ispod površine nalaze hakeri, naučnici, dileri droge..itd. Pošto prosečan korisnik ne može da vidi šta je ispod površine interneta, može da pročita ovaj tekst koji sledi i sazna šta se sve to krije u dubinama interneta. Napomena: Tekst sam kopirao sa benchmark foruma. Ukoliko pokušate da pristupite Deep Web-u, ja, niti bilo ko drugi nije odgovoran za eventualne posledice.
Za one koji ne znaju, Deep Web predstavlja ogroman deo interneta koji nije dostupan putem redovitih pretrazivanja preko Google ili drugih pretrazivaca. Šta je to BotNet? - Botnet je mreža računara koji su zaraženi virusom i koje hakeri mogu kontrolisati sa udaljene lokacije u svrhu napada i sličnih aktivnosti. Dakle, ukoliko u vaš računar bude “ubačen” jedan ovakav virus, vi to nećete znati ali vaš računar od tog trenutka postaje deo hakerskih napada. - Najnoviji takav botnet, nazvan TDL-4, najopasniji je od svih i gotovo neuništiv! TDL-4 vrsta je trojanca koja može zaraziti računar na nivou MBR-a (Master Boot Record), što ga čini otpornijim od većine zloćudnih programa. U prevodu, ukoliko ovaj Trojanac dospe u vaš računar, nećete to ni primetiti jer ga AntiVirus neće detektovati. HTC Desire HD Ice Cream Sandwich update: How to get it now! Back in March, we reported that HTC was planning to port Ice Cream Sandwich to a whole laundry list of its previous devices, including the Desire S, Incredible S and the Desire HD.
While no date’s been pencilled next to those names, the community of Android hackers are trying to beat HTC to it: a port of Android 4.0.3 has just landed for the Desire HD, and we’re gonna tell you how (and why) to get it. Right, so, you want to whip up an HTC Desire HD Ice Cream Sandwich? You need the right ingredients. Downloading. Downloading BackTrack With the release of Backtrack 5 we now support 32 bit, 64 bit and ARM architectures.
Backtrack 5 comes with two main Window Managers - Gnome and KDE. You can choose to download page either a VMWare image or a bootable ISO image (recommended if you run Backtrack from a LiveCD or a HDD/USB installation). Windows Firewall - Add or Remove an Exception. Unable to delete a folder in Windows 7, getting error Folder Access. I had this problem for quite some time.
[SOLVED]Keygen for TuneUp Utilities 2012 provided seems to be not working anymore - Site / Forum Feedback - nsane.forums - Aurora. Startup Programs - Change. How to Change, Add, or Remove Startup Programs in Windows 7 Information.
Server. You'll see a password prompt.
This allows you to set a password so that only you can connect to the server from your phone. You'll be asked to enter this password once on the phone as well. You can change your password later by right clicking on the Gmote server icon and selecting 'Change password'. The last step (Windows only) is to tell Gmote where your media files are, so that you can easily access them from your phone. Gmote automatically finds your C:\ drive and any cd/dvd drives it detects. If you encounter any problems, please visit the gmote faq page. How To Install Nessus In Backtrack 5 R1 Tutorial. StumbleUpon Diigo Delicious Nessus is one of the best vulnerability scanner that is available in two mode for both home and commercial user's, nessus plug in for home user is free of cost.
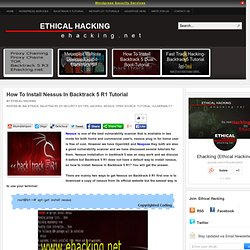
However we have OpenVAS and Nexpose they both are also a good vulnerability scanner and we have discussed several tutorials for them. Ethical Hacking-Your Way To The World Of IT Security: Backtrack 5 Tutorial. Hack facebook account and Gmail account using Backtrack 5 ~ Hack For Security. Advertisements In my previous tutorial I have explained “ How to hack facebook account using phishing ” , Now in this tutorial I am going to show you how to hack facebook account using backtrack 5.
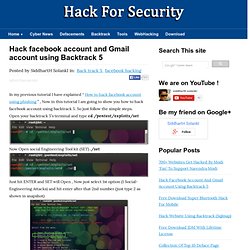
So just follow the simple steps. Open your backtrack 5’s terminal and type cd /pentest/exploits/set Now Open social Engineering Tool kit (SET) . /set Just hit ENTER and SET will Open , Now just select 1st option (1 Social-Engineering Attacks) and hit enter after that 2nd number (just type 2 as shown in snapshot) Now Just select 4th Option “Tabnabbing Attack Method” and Hit ENTER Then select 2nd option “Site Cloner” and Hit ENTER. VMware - How To Information. Virtualbox 3.1.2 Vs.
Vmware 3.0 Virtualization can save time by allowing you to run multiple operating systems on the same computer without installing them on your hard drive. The leading, free virtualizers include VirtualBox and VMware Player -- a pared-down version of VMware's commercial offering, VMware Workstation. Though both VirtualBox 3.1.2 and VMware 3.0 offer nearly identical features to users in need of a virtualizer that can run on an older system, each has its quirks. Pick the tool that best supports your preferred host and guest operating systems. How to Drag-and-Drop in VMware. Backtrack 5 – Bootable USB Thumb Drive with “Full” Disk Encryption. UPDATE (8/14/2012): I have reports that the howto works fine with Backtrack 5 R3. Please let me know if this turns out to not be the case. UPDATE (3/3/2012): The how-to has been updated to reflect changes for Backtrack R2.
They were very minor and using the previous method still works. Wireless Hacking tutorial using Backtrack ~ Hack It Easy. Wireless Hacking with backtrack 3 is easy to do , in this article I’d like to guide you in Wireless hacking with backtrack 3.
This tutorial is made based on some requests by my subscribers , they’ve been familiar enough with Backtrack 3 , that’s why I made this Wireless Hacking with backtrack 3 tutorial. Hacking away with Android pt 1 – using the file system, WiFi and FTP « Beyond the keyboard. This is one in a series of more posts to come.
Brief In the past days I have been testing several options with my Android Devices to see if I can move them beyond their general purpose. It is a preparation towards three types of use: Using Android Tablets as an alternative for a Netbook – including the use of an external keyboard, external storage, and an external mouseUsing Android devices (like tablets, hand helds and phones) as distributed computers – each fulfilling a specific task and each capable of communicating to the others and sharing and transferring filesUsing a chain of Android Devices as the “Smart Part” of Roomware installations – allowing Arduino devices and XBee-based devices to become connected to an Application Pool that can extend the local setup to a global installation. Related posts Android – more than phones: moving into alternative uses of the Android phone Recommended basic downloads.
How to crack a wireless WEP key using AIR Crack. This article shortly describes simple steps on how to crack a wireless WEP key using AIR Crack software. This can be done by sniffing a wireless network, capturing encrypted packets and running appropriate encryption cracking program in attempt to decrypt captured data. WEP ( Wired Equivalent Privacy ) is quite easy to crack as it uses only one key to encrypt all traffic. Basic principle is that communication between two nodes on the network is based on the MAC address. Each host receives packets only intended for MAC address of its own interface. The same principle also applies for a wireless networks. Install_aircrack.
Requirements Linux Kernel headers and gcc as well as make have to be installed on your system. On Debian-based distros (Debian, Ubuntu, Xubuntu, …), issue the following command in a console to install them: sudo apt-get install build-essential OpenSSL (development). Huawei 520s - zakljucavanje wirelessa. Hack Wifi using Backtrack. Do you like this story? Wifi or Wireless Fidelity is the name of a popular wireless networking technology that uses radio waves to provide wireless high-speed Internet and network connections (as if you didnt know..) ,Wifi has become an integral part of our lives today.
Wifi is secured using a WPA protocol which intends to secure Wireless LANs like Wired LAN’s by encrypting data over radio waves,however, it has been found that WEP is not as secure as once believed.Now almost anyone can hack into a Wifi network by generating the valid WEP key using Bactrack. Delphi Basics : TOpenDialog command.