

Happy 10th Birthday, Ubuntu. 20th October 2004, ten years ago today, Ubuntu 4.10 (Warty Warthog) was released.
While the user community celebrates the decade anniversary today, for me and those of us who worked on it, it was the result of almost eight months of work. My story, in common with the majority of the original group, really begins with the Debian Project. I had taken a year off full-time work and had been concentrating on involving myself more with the Linux community in general, and Debian in particular. By early 2004, the then Debian Project Leader, Martin Michlmayr had asked me to step in and take over the maintenance of Dpkg, the central package management software of the operating system. I was invited to attend the Open Source World Conference in Málaga, Spain and meet with other developers there, in particular Colin Watson and Tollef Fog Heen, to figure out the details of how we’d go about that. Mark Shuttleworth infamously vacationed to Antartica in early 2004. “MRs VD’s Warty Ubuntu? Kudos. Shellshock: The 'Bash Bug' That Could Be Worse Than Heartbleed.
Security researchers have discovered a vulnerability in the system software used in millions of computers, opening the possibility that attackers could execute arbitrary commands on web servers, other Linux-based machines and even Mac computers.
Some researchers say Shellshock, which affects an application called Bash (which is why it's often simply called the "Bash Bug"), is potentially more serious and widespread than the Heartbleed bug discovered in April, though the two vulnerabilities are quite different in nature. Unlike Heartbleed, which forced users to change their passwords for various Internet services, Shellshock doesn't appear to have any easy solutions for average users right now.
In most cases, it will be up to system administrators and software companies to issue patches. Devices use Bash, which is Unix software, to execute "shell" commands; a shell is a program that translates your commands into something the device's OS can understand. Why Do Hacker Prefer LINUX? Linux use is growing at an amazing rate.
This operating system, which has no public relations department, advertising, or government lobby, is being used widely in homes and server rooms alike. It’s also free, and 100% open source, meaning anyone can look at each and every line of code in the Linux kernel. Linux is a true multiuser operating system, and has been since the very first version. It is powerful in it’s simplicity. Though there are robust graphical environments and tools, you can still do everything you could possibly need with just a keyboard and a shell prompt. That’s one of the things that draws both the gurus and the attackers alike. The power and flexibility of Linux makes it the hacker’s playground.
Benefits of Linux: ———————— 1 : Low cost: You don’t need to spend time and money to obtain licenses since Linux and much of its software come with the GNU General Public License. 2 : Stability : Linux doesn’t need to be rebooted periodically to maintain performance levels. Storage area network. A SAN does not provide file abstraction, only block-level operations.
However, file systems built on top of SANs do provide file-level access, and are known as SAN filesystems or shared disk file systems. Storage[edit] Historically, data centers first created "islands" of SCSI disk arrays as direct-attached storage (DAS), each dedicated to an application, and visible as a number of "virtual hard drives" (i.e. LUNs).[1] Essentially, a SAN consolidates such storage islands together using a high-speed network. Operating systems maintain their own file systems on their own dedicated, non-shared LUNs, as though they were local to themselves.
Despite such issues, SANs help to increase storage capacity utilization, since multiple servers consolidate their private storage space onto the disk arrays. Common uses of a SAN include provision of transactionally accessed data that require high-speed block-level access to the hard drives such as email servers, databases, and high usage file servers. 5. R (programming language) R is a programming language and software environment for statistical computing and graphics.
The R language is widely used among statisticians and data miners for developing statistical software[2][3] and data analysis.[3] Polls, surveys of data miners, and studies of scholarly literature databases show that R's popularity has increased substantially in recent years.[4][5][6][7] R is highly extensible through the use of user-submitted packages for specific functions or specific areas of study. Due to its S heritage, R has stronger object-oriented programming facilities than most statistical computing languages. Extending R is also eased by its lexical scoping rules.[19]
MapReduce Patterns, Algorithms, and Use Cases. In this article I digested a number of MapReduce patterns and algorithms to give a systematic view of the different techniques that can be found on the web or scientific articles.
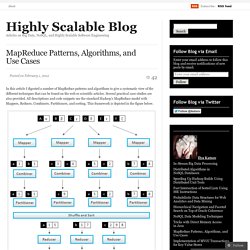
Several practical case studies are also provided. All descriptions and code snippets use the standard Hadoop’s MapReduce model with Mappers, Reduces, Combiners, Partitioners, and sorting. This framework is depicted in the figure below. MapReduce Framework Counting and Summing Problem Statement: There is a number of documents where each document is a set of terms.
Solution: Let start with something really simple. The obvious disadvantage of this approach is a high amount of dummy counters emitted by the Mapper.