

Week 6 Journal. Complaints. Web-Borne Malware Breaches Cost $3.2M to Remediate: Survey. A new survey from the Ponemon Institute calls web-borne malware not only a growing threat to enterprise data security, but a costly one.

According to the report, which surveyed 645 IT pros and IT security practitioners and was sponsored by security firm Spike Security, web-borne malware attacks cost the organizations in the survey an average of $3.2 million to remediate. The organizations surveyed had an average of 14,000 employees. Sixty-nine percent believe browser-borne malware is a more significant threat today than it was 12 months ago. "The findings of this research reveal that current solutions are not stopping the growth of web-borne malware," said Dr. Larry Ponemon, chairman and founder of Ponemon Institute, in a statement. " While all of the companies surveyed utilized a multilayered, defense-in-depth approach, they still dealt with an average of 51 security breaches during the past year tied to the failure of malware detection technology.
Does apple recommend running anti-virus software with snow leopard? Hygiene, Honey Pots, Espionage: 3 Approaches To Defying Hackers : All Tech Considered. Dmitri Alperovitch, co-founder of the cybersecurity startup CrowdStrike, says his company is building stockpiles of intelligence about potential hacking groups.
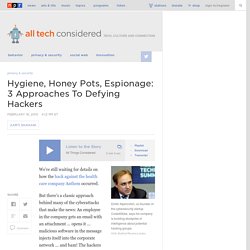
Keith Bedford/Reuters/Landov hide caption itoggle caption Keith Bedford/Reuters/Landov Dmitri Alperovitch, co-founder of the cybersecurity startup CrowdStrike, says his company is building stockpiles of intelligence about potential hacking groups. Keith Bedford/Reuters/Landov We're still waiting for details on how the hack against the health care company Anthem occurred. But there's a classic approach behind many of the cyberattacks that make the news: An employee in the company gets an email with an attachment ... opens it ... malicious software in the message injects itself into the corporate network ... and bam! How Do I Protect Myself Against Malware? The best way to deal with a malware attack is to avoid getting infected in the first place.
Identity Theft. You Might Want To Take Another Pass At Your Passwords : All Tech Considered. They might be hard to remember sometimes, but good passwords may be the best defense against hackers.
iStockphoto hide caption itoggle caption iStockphoto They might be hard to remember sometimes, but good passwords may be the best defense against hackers. iStockphoto Compromises of private corporate or consumer data are all too common. Yet even President Obama last week poked fun at our common line of defense: the lazy password. The Five Biggest Threats to Your Kids’ Privacy, and What You Can Do About Them. Remember back in school, when your teachers warned that everything you did would go on your permanent record?
It turns out your teachers have become right. That permanent record is the Internet. It’s hard to be a fully functioning adult in 2014 and not leave behind a digital trail. Now imagine how hard it is for your kids, who have never known a world where the net did not exist. From the moment they emerge from the womb, they’re generating data, which is then eagerly absorbed and stored by Internet companies, government agencies and some evil no-goodniks. Despite federal laws prohibiting the collection of data from children under the age of 13, dossiers are constantly being created about your kids, whether it’s Google capturing their search histories, advertisers creating profiles of their interests, or their grandparents tagging photos of them on Facebook. How to Tell if your Cell Phone is Being Tracked, Tapped or Monitored by Spy Software - SpyzRus.net. There are a few signs that may help you find out if your cell phone has spy software installed and that it is being tracked, tapped or monitored in some way.
Quite often these signs can be quite subtle but when you know what to look out for, you can sometimes find out if your cell phone is being spied on. This article series will deal with How to Find installed Spy Phone Software and then How to Remove Spy Software followed by How to Secure your Cell Phone. This guide should help for all types of Smartphone including Android and for the iPhone there are a few extra tips. It seems that almost everyone is obsessed with cell phones, from young kids’ right through to the elderly. Babies seem to be the only ones missing out so far! I know that it might seem strange to younger readers, but back in the day, cell phones were only used to make phone calls (often quite unreliably). Is Your Mobile Phone Being Monitored? Spy software apps. How to Protect Your Computer from Hackers, Spyware and Viruses. This article has been inspired by a situation I ran into while visiting a cousin in India.
Since I’m in the IT field, she asked me to take a look at her computer since it was acting “funny”. The “funny” part was that the computer would automatically restart whenever you tried to install ANY software onto it or download any program from the Internet. The first thing I noticed was that there was no anti-virus software installed on the computer, so my first goal was to install an anti-virus program and check for viruses. But of course, the virus that was already on the computer would not let me install or download anything! Smart virus! Most of the viruses on the computer were hidden in files that had been downloaded off the Internet: songs, videos, and movies. This is by no means a comprehensive list, so if you have any suggestions, please feel free to comment and I’ll add them on! 1.