

HowTo: Map a user to a certificate via all the methods available in the altSecurityIdentities attribute - Spat's WebLog (Steve Patrick) Today I am going to talk a little bit about certificate mapping.
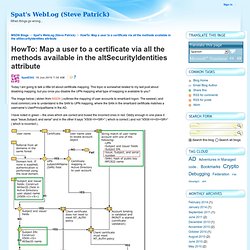
This topic is somewhat related to my last post about disabling mapping, but you once you disable the UPN mapping what type of mapping is available to you? The image below ( stolen from MSDN ) outlines the mapping of user accounts to smartcard logon. The easiest ( and most common) one to understand is the SAN to UPN mapping, where the SAN in the smartcard certificate matches a username’s UserPrincipalName in the AD. I have noted in green – the ones which are correct and boxed the incorrect ones in red. Oddly enough in one place it says “Issue,Subject, and serial” and in the other it says “X509:<I><SR>” ( which is correct ) and not “X509:<I><S><SR>” ( which is incorrect ) .
The more complex, and less documented ( or documented incorrectly ) are as follows: Kerberos Explained. By Mark Walla Article from the May 2000 issue of Windows 2000 Advantage magazine Although this article is billed as a primer to Kerberos authentication, it is a high technical review.

Kerberos is an integral part of Windows 2000 Active Directory implementations, and anyone planning to deploy and maintain a Windows 2000 enterprise must have a working knowledge of the principals and administrative issues involved in this front-line security technology. Since many other operating system vendors are also adopting this MIT-developed authentication protocol, Kerberos Version 5 will increasingly become a centerpiece of enterprise-level interoperability. Kerberos provides secure user authentication with an industry standard that permits interoperability. The process of authenticating the identity of users during log-in is the first step in gaining system access. On This Page. Configuring SharePoint 2010 with Kerberos Authentication. Determine the application pool account that will be responsible for authenticating users.
Follow the steps below to be absolutely sure of the account responsible for running the site that will support kerberos authentication. If SharePoint has already been configured verify your application pool account is, in fact, running the IIS application pool that supports the website where Kerberos is enabled Open the web application that will support Kerberos and make a note of the application pool that supports this web application (note that you may have more than one web application for the same data for such cases as http and https so take care to determine the exact web application) Make a note of the account that is the identity of this application pool, later this account must be trusted for “Delegation”. Configuring Kerberos for SharePoint 2007: Part 1 - Base Configuration for SharePoint - A Marvellous Point.
(UPDATED on 04/06/07 as per feedback from two different subscribers (thank-you).
Updates in Italic) (UPDATED on 20/08/07: My colleauge James World has just published an excellent article which is a kind of follow-up to this one. It goes a bit deeper on Kerberos basics and covers some real-world tips that relate specifically to SharePoint. Check it out here: ) At some point during a career working with SharePoint, everyone will be given the dubious task of configuring Kerberos authentication. This is the first of a several-part series that outlines what you need to do to enable Kerberos in a MOSS 2007 environment. Why Kerberos? There are many reasons why Kerberos authentication can be used rather than the default NTLM, the main reason should be because it is faster and more secure than NTLM. In SharePoint, 'double hops' are most commonly seen when webparts need to access other web services or databases. Step 1: SPNs Step 2: Trust for Delegation. Kerberos for the Busy Admin - Ask the Directory Services Team. Hi Rob here, I am a Support Escalation Engineer in Directory Services out of Charlotte, NC, USA.
We work a lot of Kerberos authentication failure issues. Since Kerberos is typically the first authentication method attempted, it ends up having authentication failures more often. One of the great things about Windows is that the product seems to just work without too much customization that is needed by the customer. However I wanted to create a blog to try and demystify how Kerberos authentication works.
I plan on writing several Kerberos blogs in the near future to include Kerberos Delegation aka Double-hop, how to troubleshoot Kerberos authentication. There are some general terms that you might not be familiar, so let's run through them quickly. Principal Names: Kerberos defines two different types of accounts (or Principals). Only user accounts have a UPN defined on their account. Service Principal Names define what services run under the accounts security context.