

Callback (computer science) Two's complement. Two's complement is a mathematical operation on binary numbers, as well as a binary signed number representation based on this operation.
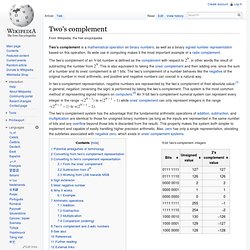
Its wide use in computing makes it the most important example of a radix complement. The two's complement of an N-bit number is defined as the complement with respect to 2N, in other words the result of subtracting the number from 2N. This is also equivalent to taking the ones' complement and then adding one, since the sum of a number and its ones' complement is all 1 bits.
The two's complement of a number behaves like the negative of the original number in most arithmetic, and positive and negative numbers can coexist in a natural way. OpenMP.org. Non-Uniform Memory Access. Non-uniform memory access (NUMA) is a computer memory design used in multiprocessing, where the memory access time depends on the memory location relative to the processor.
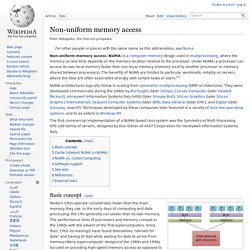
Under NUMA, a processor can access its own local memory faster than non-local memory (memory local to another processor or memory shared between processors). The benefits of NUMA are limited to particular workloads, notably on servers where the data are often associated strongly with certain tasks or users.[1] Symmetric multiprocessing. Diagram of a symmetric multiprocessing system Symmetric multiprocessing (SMP) involves a multiprocessor computer hardware and software architecture where two or more identical processors connect to a single, shared main memory, have full access to all I/O devices, and are controlled by a single OS instance that treats all processors equally, reserving none for special purposes.
Most multiprocessor systems today use an SMP architecture. In the case of multi-core processors, the SMP architecture applies to the cores, treating them as separate processors. Upper Memory Area. The upper memory area is located between 640 KB and 1024 KB.
In DOS memory management, the upper memory area (UMA) refers to memory between the addresses of 640 KB and 1024 KB (0xA0000–0xFFFFF) in an IBM PC or compatible. IBM reserved the uppermost 384 KB of the 8088 CPU's 1024 KB address space for ROM, RAM on peripherals, and memory-mapped input/output. For example, the monochrome video memory area runs from 704 to 736 KB (0xB0000–B7FFF). However, even with video RAM, the ROM BIOS and I/O ports for expansion cards, much of this 384 KB of address space was unused.
As the 640 KB memory restriction became ever more of an obstacle, techniques were found to fill the empty areas with RAM. Amdahl's law. The speedup of a program using multiple processors in parallel computing is limited by the sequential fraction of the program.
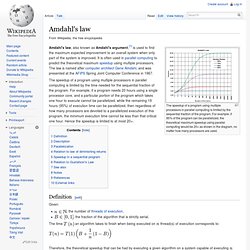
For example, if 95% of the program can be parallelized, the theoretical maximum speedup using parallel computing would be 20× as shown in the diagram, no matter how many processors are used. Amdahl's law, also known as Amdahl's argument,[1] is used to find the maximum expected improvement to an overall system when only part of the system is improved. It is often used in parallel computing to predict the theoretical maximum speedup using multiple processors. The law is named after computer architect Gene Amdahl, and was presented at the AFIPS Spring Joint Computer Conference in 1967.
Thread (computer science) A process with two threads of execution on a single processor On a single processor, multithreading is generally implemented by time-division multiplexing (as in multitasking): the processor switches between different threads.
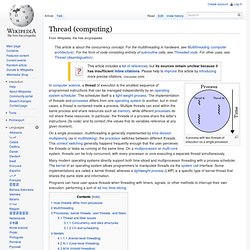
This context switching generally happens frequently enough that the user perceives the threads or tasks as running at the same time. On a multiprocessor or multi-core system, threads can be truly concurrent, with every processor or core executing a separate thread simultaneously. Flynn's taxonomy. Flynn's taxonomy is a classification of computer architectures, proposed by Michael J.
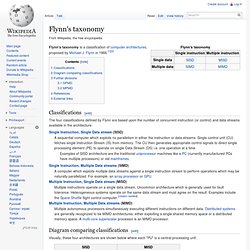
Flynn in 1966.[1][2] Classifications[edit] The four classifications defined by Flynn are based upon the number of concurrent instruction (or control) and data streams available in the architecture: Single Instruction, Single Data stream (SISD) MIMD. In computing, MIMD (multiple instruction, multiple data) is a technique employed to achieve parallelism.
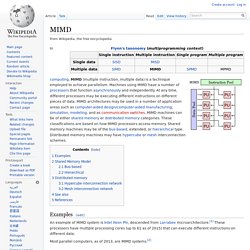
Machines using MIMD have a number of processors that function asynchronously and independently. At any time, different processors may be executing different instructions on different pieces of data. Message Passing Interface. Request for Comments. A Request for Comments (RFC) is a publication of the Internet Engineering Task Force (IETF) and the Internet Society, the principal technical development and standards-setting bodies for the Internet.
An RFC is authored by engineers and computer scientists in the form of a memorandum describing methods, behaviours, research, or innovations applicable to the working of the Internet and Internet-connected systems. It is submitted either for peer review or simply to convey new concepts, information, or (occasionally) engineering humour. The IETF adopts some of the proposals published as RFCs as Internet standards. History[edit] Transport Layer Security. Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are cryptographic protocols designed to provide communications security over a computer network.[1] They use X.509 certificates and hence asymmetric cryptography to authenticate the counterparty with whom they are communicating,[2] and to exchange a symmetric key.
This session key is then used to encrypt data flowing between the parties. This allows for data/message confidentiality, and message authentication codes for message integrity and as a by-product, message authentication. [clarification needed] Several versions of the protocols are in widespread use in applications such as web browsing, electronic mail, Internet faxing, instant messaging, and voice-over-IP (VoIP). An important property in this context is forward secrecy, so the short-term session key cannot be derived from the long-term asymmetric secret key.[3] Description[edit] History and development[edit] Secure Network Programming[edit] Dr. Notes. SQL. SQL (/ˈɛs kjuː ˈɛl/,[4] or /ˈsiːkwəl/; Structured Query Language[5][6][7][8]) is a special-purpose programming language designed for managing data held in a relational database management system (RDBMS).
Originally based upon relational algebra and tuple relational calculus, SQL consists of a data definition language and a data manipulation language. The scope of SQL includes data insert, query, update and delete, schema creation and modification, and data access control. Although SQL is often described as, and to a great extent is, a declarative language (4GL), it also includes procedural elements. Cognitive network. In communication networks, cognitive network (CN) is a new type of data network that makes use of cutting edge technology from several research areas (i.e. machine learning, knowledge representation, computer network, network management) to solve some problems current networks are faced with.
OSI model. Model with 7 layers to describe communications systems The Open Systems Interconnection model (OSI model) is a conceptual model that characterizes and standardizes the communication functions of a telecommunication or computing system without regard to its underlying internal structure and technology. Its goal is the interoperability of diverse communication systems with standard protocols. The model partitions a communication system into abstraction layers. The original version of the model defined seven layers. Message Passing Interface. History[edit] Category:Computer science stubs. From Wikipedia, the free encyclopedia Subcategories This category has the following 12 subcategories, out of 12 total. Notes on C. C (programming language) C is one of the most widely used programming languages of all time,[8][9] and C compilers are available for the majority of available computer architectures and operating systems.
C is an imperative (procedural) language. It was designed to be compiled using a relatively straightforward compiler, to provide low-level access to memory, to provide language constructs that map efficiently to machine instructions, and to require minimal run-time support. C was therefore useful for many applications that had formerly been coded in assembly language, such as in system programming. Despite its low-level capabilities, the language was designed to encourage cross-platform programming.
A standards-compliant and portably written C program can be compiled for a very wide variety of computer platforms and operating systems with few changes to its source code. Preprocessor. Lexical preprocessors[edit]