

HowTo/EximAndDovecotSASL - Dovecot Wiki. AuthenticatedSmtpUsingPam · Exim/exim Wiki. Authenticated SMTP using PAM Introduction.
Ch14 : Linux Firewalls Using iptables. Network security is a primary consideration in any decision to host a website as the threats are becoming more widespread and persistent every day.

One means of providing additional protection is to invest in a firewall. Though prices are always falling, in some cases you may be able to create a comparable unit using the Linux iptables package on an existing server for little or no additional expenditure. How do I use Iptables connection tracking feature? By Vivek Gite on October 27, 2005 Connection tracking is an essential security feature of Iptables.
But, what is connection tracking? It is the ability to maintain connection information in memory. How do I use Iptables connection tracking feature? Iptables Open FTP Port 21 and 20. By Vivek Gite on April 13, 2006 How do I open port 21 using Linux iptables firewall?
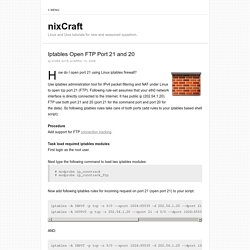
Use iptables administration tool for IPv4 packet filtering and NAT under Linux to open tcp port 21 (FTP). Following rule-set assumes that your eth0 network interface is directly connected to the Internet. It has public ip (202.54.1.20). FTP use both port 21 and 20 (port 21 for the command port and port 20 for the data). Procedure Add support for FTP connection tracking. Task load required iptables modules First login as the root user. Iptables rules for NAT with FTP active / passive connections. If you have an FTP server running behind a server that acts as the gateway or firewall, here are the rules to enable full NAT for active and passive connections. # general rules for forwarding traffic between external interface tap0 and internal interface eth0 iptables -t nat -A POSTROUTING -o tap0 -j MASQUERADE iptables -A FORWARD -i tap0 -o eth0 -m state --state RELATED,ESTABLISHED -j ACCEPT iptables -A FORWARD -i eth0 -o tap0 -j ACCEPT.
Iptables debugging « \1. Has it ever happened to you that iptables was apparently not working as expected, and, in an effort to find out what's going on, you littered your ruleset with logging rules all over the place, or some other awkward kludge?
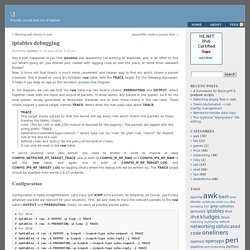
Now, it turns out that there's a much more convenient and cleaner way to find out which chains a packet traverses. This is based on using ip{,6}tables' raw table, with the TRACE target. For the following discussion, it helps if you keep an eye on this excellent iptables flow diagram. In the diagram, we can see that the raw table has two built-in chains: PREROUTING and OUTPUT, which together cover both the input and output of packets. In other words, any packet in the system, be it for the local system, locally generated, or forwarded, traverses one or both these chains in the raw table. TRACE This target marks packes so that the kernel will log every rule which match the packets as those traverse the tables, chains, rules.
View topic - Шифрованные пароли. AuthenticatedSmtpUsingPam · Exim/exim Wiki. AuthenticatedSmtpUsingPam · Exim/exim Wiki. [Exim] AUTH with PAM using pam_radius_auth. Lähettäjä: Jonker, NielsPäiväys: 2001-12-08 16:58 Vastaanottaja: 'exim-users@exim.org'Aihe: [Exim] AUTH with PAM using pam_radius_auth.
![[Exim] AUTH with PAM using pam_radius_auth.](http://cdn.pearltrees.com/s/pic/th/exim-auth-with-using-radius-110925402)
In order to make Exim use PAM to Radius under Linux (Redhat 7.1) I used the pam_radius_auth.so available from freeradius.org (About the only one I could find that actually worked for Auth). Note that the module does NOT support all the PAM functions exim wants. Here's what I did to make it work: PAM Tutorial. © 2005–2012 by Wayne Pollock, Tampa Florida USA.

All Rights Reserved. Many interactive commands are security sensitive. An obvious example is passwd used to change a user's password. Such commands require users to authenticate themselves even though they have successfully logged in to the system. Also many server daemons carry out tasks on behalf of remote users, and most of these require the daemon to authenticate the remote user. Early versions of Unix had all such programs (applications and daemons) directly read and parse the /etc/passwd file, so they could authenticate users.
Showterm. Using RADIUS to authenticate users with RSA SecurID. Recently I was tasked with authenticating users who carry RSA SecurID tokens.
I was highly inspired by Jeff Wirth and his success using RADIUS to authenticate with SecurID Tokens on FreeBSD. While I'm not a fan of non-free software, it's possible to make each server authenticate against the non-free RSA Ace server using only free software. This isn't a perfect solution but it's useful when such a requirement is thrust upon you. The requirements are simple. How To Set Up WebDAV With Apache2 On Debian Etch. Version 1.0 Author: Falko Timme This guide explains how to set up WebDAV with Apache2 on a Debian Etch server.
WebDAV stands for Web-based Distributed Authoring and Versioning and is a set of extensions to the HTTP protocol that allow users to directly edit files on the Apache server so that they do not need to be downloaded/uploaded via FTP. Of course, WebDAV can also be used to upload and download files. How to jail / chroot users in FTP / SFTP - Ochounos.com - Web development. How to install Pam-radius on Ubuntu server. Force PAM to create user home folder if it already not exists. Lorens November 18th, 2011, 10:08 AM I'm posting the configuration files: Ch09. The rest of this section is about using the PAM module provided in the Samba distribution to enable Windows domain users to authenticate on the Linux system hosting Samba. Depending on which services you choose to configure, this allows Windows domain users to log in on a local console (or through telnet), log in to a GUI desktop on the Linux system, authenticate with an FTP server running on the Linux system, or use other services normally limited to users who have an account on the Linux system.
The PAM module authenticates Windows domain users by querying winbind, which passes the authentication off to a Windows NT domain controller. As an example, we will show how to allow Windows domain users to log in to a text console on the Linux system and get a command shell and home directory. The method used in our example can be applied (with variations) to other services. All users who can log in to the Linux system need a shell and a home directory. How to create a software RAID-1 array with mdadm on Linux. Redundant Array of Independent Disks (RAID) is a storage technology that combines multiple hard disks into a single logical unit to provide fault-tolerance and/or improve disk I/O performance.
Depending on how data is stored in an array of disks (e.g., with striping, mirroring, parity, or any combination thereof), different RAID levels are defined (e.g., RAID-0, RAID-1, RAID-5, etc). RAID can be implemented either in software or with a hardware RAID card. On modern Linux, basic software RAID functionality is available by default. In this post, we'll discuss the software setup of a RAID-1 array (also known as a "mirroring" array), where identical data is written to the two devices that form the array. How to create a software RAID-1 array with mdadm on Linux. Core. AcceptFilter Directive This directive enables operating system specific optimizations for a listening socket by the Protocol type. The basic premise is for the kernel to not send a socket to the server process until either data is received or an entire HTTP Request is buffered.
Only FreeBSD's Accept Filters and Linux's more primitive TCP_DEFER_ACCEPT are currently supported. The default values on FreeBSD are: AcceptFilter http httpready AcceptFilter https dataready The httpready accept filter buffers entire HTTP requests at the kernel level. The default values on Linux are: AcceptFilter http data AcceptFilter https data Linux's TCP_DEFER_ACCEPT does not support buffering http requests. How to get mod_auth_pam running on Apache 2.2.x. Mod_auth_pam is not supported and/or developed any longer and the latest available version works only with apache 2.0.x. The new apache 2.2 uses a new authentication mechanism and the old mod_auth_pam does not work, if you only install it to your local apache and use it with the follow configuration: AuthPAM_Enabled On AuthPAM_FallThrough Off AuthType Basic AuthName "Testingarea" You have to turn off the new apache 2.2 basic authentication to get the module up and running.
You can do this in two different ways. The first one is to disable the whole module, the second and better one is to disable it through a directive. For the first solution, you can use the tool a2dismod to disable the module mod_auth_basic. PAM with Radius Authentication. PAM Radius Module allows any PAM-capable machine to become a RADIUS client for authentication and accounting requests. The actual authentication will be performed by a RADIUS server. The freeradius can be used for radius server. How to authenticate Apache 2 with Radius on Debian « Admins eHow.
FreeRADIUS: Working with Authentication Methods. (For more resources on this subject, see here.) This section will give you background on three common authentication protocols. These protocols involve the supply of a username and password. The radtest program uses the Password Authentication Protocol (PAP) by default when testing authentication.
PAP is not the only authentication protocol but probably the most generic and widely used. Authentication protocols you should know about are PAP, CHAP, and MS-CHAP. An authentication protocol is typically used on the data link layer that connects the client with the NAS. The data link layer and network layer are layers inside the Open Systems Interconnect model (OSI model). PAP was one of the first protocols used to facilitate the supply of a username and password when making point-to-point connections. Although PAP transmits passwords in clear text, using it should not always be frowned upon. If PAP is used inside a secure tunnel it is as secure as the tunnel. How Squid ACLs work. For less experienced Squid administrators the concept of ACLs can be confusing at first.
Access_controls.