

Rumy Hack Tips: Configuring AnyConnect WebVPN on Cisco Router. Configuring Cisco SSL VPN AnyConnect (WebVPN) on Cisco IOS Routers. Our Web SSL VPN article written back in 2011 introduced this new wave of VPN services.
This article extends the topic by covering the installation and configuration of Cisco’s SSL AnyConnect VPN for Cisco IOS Routers. Web SSL VPN delivers the following three modes of SSL VPN access: • Clientless - Clientless mode provides secure access to private web resources and will provide access to web content. This mode is useful for accessing most content that you would expect to access in a web browser such as Internet access, web-based intranet, webmail etc. • Thin Client (port-forwarding Java applet) - Thin client mode extends the capability of the cryptographic functions of the web browser to enable remote access to TCP-based applications such as Post Office Protocol version 3 (POP3), Simple Mail Transfer Protocol (SMTP), Internet Message Access protocol (IMAP), Telnet and Secure Shell (SSH).
Configure AnyConnect with CLI. April 5, 2013By Sean Wilkins One main capability of the AnyConnect client is that it provides a virtual private network (VPN) connection from a remote location to a second secured location.
This capability of AnyConnect can be deployed from both Adaptive Security Appliances (ASA) and from a device running a supporting version of IOS (assuming the license has been purchased). Take a look at the configuration that is required to get this up and running on a Cisco IOS device. To start off, the licensing of the Security and SSL VPN licenses have already been installed on the device. Security Appliance Command Line Configuration Guide, Version 8.0 - Configuring AnyConnect VPN Client Connections [Cisco ASA 5500 Series Next Generation Firewalls.
AnyConnect VPN (SSL) Client on IOS Router with CCP Configuration Example. Introduction This document describes how to set up a Cisco IOS® router to perform Secure Sockets Layer (SSL) VPN on a stick with Cisco AnyConnect VPN client using Cisco Configuration Professional (CCP).

This setup applies to a specific case where AnyConnect on the Router is configured with split tunneling, and it allows the client secure access to corporate resources and also provides unsecured access to the Internet. SSL VPN or WebVPN technology is supported on most router platforms such as the Integrated Services Router (ISR) Generation 1, Generation 2 (Refer ISR Products for the list of ISR products). Customers are advised to refer the feature navigator guide in order to obtain a complete list of Cisco IOS platforms that support the AnyConnect VPN (SSL) client (or any other feature/ technology for that matter). This information is available in the Feature Navigator.
Configuring Cisco Site to Site IPSec VPN with Dynamic IP Endpoint Cisco Routers. This article serves as an extension to our popular Cisco VPN topics covered here on Firewall.cx.
While we’ve covered Site to Site IPSec VPN Tunnel Between Cisco Routers (using static public IP addresses), we will now take a look on how to configure our headquarter Cisco router to support remote Cisco routers with dynamic IP addresses. One important note to keep in mind when it comes to this implementation, is that Site-to-Site VPN networks with Dynamic remote Public IP addresses can only be brought up by the remote site routers as only they are aware of the headquarter's router Public IP address. IPSec VPN tunnels can also be configured using GRE (Generic Routing Encapsulation) Tunnels with IPsec encryption. GRE tunnels greatly simply the configuration and administration of VPN tunnels and are covered in our Configuring Point-to-Point GRE VPN Tunnels article. ISAKMP associations using RSA keys. Most of the IPsec tunnels I see configured, both in labs and in the real world, rely on relatively weak preshared keys to establish the initial secure ISAKMP channel for key exchange between the IPsec peers (see my IPsec quick and dirty article for an example configuration).

A much stronger solution is to use public/private key pairs distributed by a secure Public Key Infrastructure (PKI) Certificate Authority (CA). Unfortunately, deploying an enterprise PKI is no small undertaking, and many engineers are understandably hesitant about tying any aspect of network connectivity to the functionality of unrelated servers or services. Fortunately, IOS allows for a comfortable middle ground, using manually distributed RSA encryption keys on routers.
Router-to-Router IPSec (RSA Keys) on GRE Tunnel with RIP Configuration Example [IPSec Negotiation/IKE Protocols. Introduction This document provides a sample configuration for routers with RSA keys.

Both routers are configured for RSA keys and IPSec/Generic Routing Encapsulation (GRE) tunnel with Routing Information Protocol (RIP). Prerequisites Requirements There are no specific requirements for this document. Components Used. Troubleshooting IPSec VPNs. When troubleshooting IPSec VPNs, it is important to adopt a step-by-step approach.
The first step in troubleshooting IPSec VPNs is to verify IKE phase 1 negotiation between the peer routers. Once this has been verified, the next step is to verify IKE phase 2. In the final step, you should verify that user traffic is being transported successfully over the IPSec tunnel. The flowchart in Figure 8-13 describes the troubleshooting process used with IPSec VPNs. You can use this flowchart to quickly access the section of the chapter relevant to problems you are experiencing on your network. Refer to the sample topology in Figure 8-14 for the various concepts discussed in the troubleshooting sections that follow. In this example, the initiator of IKE negotiation is called Tokyo, and the responder is called Osaka. Dynamic point to point IPSEC VPN tunnels using DTVIs (GNS3 Lab) Manually configuring point to point IPSEC tunnels can become a big administrative burden as the number of endpoints grows.
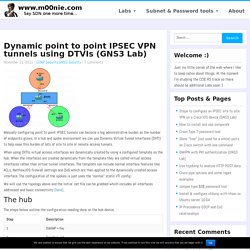
In a hub and spoke environment we can use Dynamic Virtual Tunnel Interfaces (DVTI) to help ease this burden of lots of site to site or remote access tunnels. When using DVTIs virtual access interfaces are dynamically created by using a configured template on the hub. When the interfaces are created dynamically from the template they are called virtual access interfaces rather than virtual tunnel interfaces. Security for VPNs with IPsec Configuration Guide, Cisco IOS Release 12.4T - IPsec Virtual Tunnel Interface [Support. DVTI supports multiple IPsec SAs.
The DVTI can accept multiple IPsec selectors that are proposed by the initiator. The DVTIs allow per peer features to be applied on a dedicated interface. You can order features in such way that all features that are applied on the virtual access interfaces are applied before applying crypto. Additionally, all the features that are applied on the physical interfaces are applied after applying crypto. Clean routing is available across all VRFs so that there are no traffic leaks from one VRF to another before encrypting. VTI vs. crypto map implementation. IOS Router to Pass a LAN-to-LAN IPSec Tunnel via PAT Configuration Example.
Configuring a Router IPsec Tunnel Private-to-Private Network with NAT and a Static. An Illustrated Guide to IPsec. IPsec is a suite of protocols for securing network connections, but the details and many variations quickly become overwhelming.

This is particularly the case when trying to interoperate between disparate systems, causing more than one engineer to just mindlessly turn the knobs when attempting to bring up a new connection. This Tech Tip means to give bottom-up coverage of the low-level protocols used in an IPv4 context (we provide no coverage of IPv6). This is not a deployment guide or best-practices document — we're looking at it strictly at the protocol level on up, rather than from the big picture on down. NOTE: originally this was to be a pair of papers, with the second covering Key Exchange and the like, but it appears that this was not meant to be. Sorry. In this section, we'll touch on some of the items in the form of a glossary, with a compare-and-contrast to show which terms relate to which other terms.
AH versus ESP Tunnel mode versus Transport mode IKE versus manual keys ver hlen. Cisco - Configuring an IOS Router Doing PAT to Pass a Standard IPSec Tunnel (in Tunnel Mode) Through It - 099_Cisco IOS PAT IPSEC Tunnel Guide.pdf. Advanced Cisco IPSec VPN Features. Advanced Cisco IPSec VPN Features Cisco ASA provides many advanced features to suit your remote-access VPN implementations. Some of these features are listed here: The sections that follow cover these features in more detail. How Does NAT-T work with IPSec? Introduction: This document describes details on how NAT-T works. Background: ESP encrypts all critical information, encapsulating the entire inner TCP/UDP datagram within an ESP header. ESP is an IP protocol in the same sense that TCP and UDP are IP protocols (OSI Network Layer 3), but it does not have any port information like TCP/UDP (OSI Transport Layer 4).
This is a difference from ISAKMP which uses UDP port 500 as its transport layer. PAT (Port Address Translation) is used to provide many hosts access to the internet through the same publically routable ip address. Q1: Why can't an ESP packet pass through a PAT device? It is precisely because ESP is a protocol without ports that prevents it from passing through PAT devices. Configuring Cisco Easy VPN with IPSec Dynamic Virtual Tunnel Interface (DVTI) This document provides a sample configuration for enhanced Cisco® Easy VPN Server and Easy VPN Remote configuration using the IPSec Dynamic Virtual Tunnel Interface (DVTI). Cisco Easy VPN Remote is configured with User Extension Mode and is assigned a dynamic IP address from the Easy VPN Server. Cisco Easy VPN with DVTI configuration provides a routable interface for forwarding traffic based on IP routing tables.
Cisco Easy VPN uses a virtual access interface, which is created during the initial configuration. The VPN traffic is forwarded to the virtual access interface for encryption and then sent out of the physical interface. This sample configuration also demonstrates the use of quality of service (QoS) with virtual tunnel interfaces. Figure 1 shows the sample configuration. Figure 1. Diffie-Hellman Example Calculator. Private VLANs Revisited. Due to the non-decreasing interest to the post about Private VLANs, I decided to make another one, more detailed – including a diagram and verification techniques. Introduction To begin with, recall that VLAN is essentially a broadcast domain. Private VLANs (PVANs) allow splitting the domain into multiple isolated broadcast “subdomains”, introducing sub-VLANs inside a VLAN.
IPSec Network Security Commands [Support. 1800 Series Integrated Services Routers (Fixed) Software Configuration Guide - Configuring VPNs Using an IPSec Tunnel and Generic Routing Encapsulation [Cisco 1800 Series Integrated Services Routers. Point-to-Point GRE over IPsec Design Guide - Point-to-Point GRE over IPSec Design and Implementation [Design Zone for IPv6. Using GRE tunnels in conjunction with IPsec provides the ability to run a routing protocol, IP multicast (IPmc), or multiprotocol traffic across the network between the headend(s) and branch offices. GRE also enables private addressing. Without a tunnel protocol running, all end stations are required to be addressed with registered IP addresses. By encapsulating the IP packet in a tunneling protocol, private address space can be used. With the p2p GRE over IPsec solution, all traffic between sites is encapsulated in a p2p GRE packet before the encryption process, simplifying the access control list used in the crypto map statements.