

DeveloperWorks : Open source tutorials and projects. DeveloperWorks : Linux.
Keyboard (keys) reading. Allwinner a10. The Allwinner A10 CPU has been developed in, and is sold in, the People's Republic of China.

Its mass-volume price is around $7, yet it is a 400-pin highly feature-rich 1.2ghz ARM Cortex A8 with a MALI400 GPU. It has the distinction of having the highest bang-per-buck ratio of any SoC available at the time of writing, by quite a margin. Its price and features is causing massive disruption of the tablet market in China (a minor recession was caused by widespread cancellation of prior committments to other SoCs!) , as every factory in Shenzen scrambles to compete with hundreds of other factories for the same end-user market: tablets and PVRs. For comparison: TI has brought out a new $5 ARM Cortex A8, but it is limited to 500mhz and it is extra cost for the version with a PowerVR 3D GPU.
Preorders If you would like to register your interest in an EOMA-68 CPU card with an Allwinner A10 CPU, please follow the instructions at the orders page. News Updates are available at the news page. Explore Linux /proc File System (/proc directories, /proc files) Inside the /proc directory, you’ll see two types of content — numbered directories, and system information files. /proc is not a real file system, it is a virtual file system. For example, if you do ls -l /proc/stat, you’ll notice that it has a size of 0 bytes, but if you do “cat /proc/stat”, you’ll see some content inside the file. Several Linux commands access the information from /proc, and displays in a certain format. 1. /proc Directories with names as numbers Do a ls -l /proc, and you’ll see lot of directories with just numbers.
Following are the important files located under each numbered directory (for each process): cmdline – command line of the command. environ – environment variables. fd – Contains the file descriptors which is linked to the appropriate files. limits – Contains the information about the specific limits to the process. mounts – mount related information. 4.3. Setting up permissions for USB ports. As USB is designed for hotplugging of devices, the operating system also needs a mechanism that dynamically creates devices (device files) for the devices currently connected and switched on. The operating system has to determine which users may access a device dynamically. As the operating system cannot determine this by itself, there have to be some helper applications. If you are using pre-built packages for your distribution (such as SuSE or Redhat RPMs or Debian DEBs, Gentoo Ebuilds, FreeBSD pots, ...), simply installing those packages should do this configuration for you.
In reality, however, you often still have to do a varying amount of work. Read the documentation for your package (usually somewhere in /usr/share/doc/*gphoto2*/) and this guide section to find out if and what work there still is or may be to do for you. If you are installing and setting up libgphoto2 yourself, then the following sections explain the configuration of these helpers. /proc. Proc(5) - Linux manual page.
Advice for boot loader authors. Serial console support in a boot loader is very useful.

Thank you for supporting it. The boot loader should support the 8250A UART and its programming-compatible 82510, 16450, 16550 and 16750 descendants. The serial chip used in the IBM PC/XT, the 8250 (no A), and its 8250B descendant need not be supported. The 8250A data sheet is 82C50A CMOS Asynchronous Communications Element and is updated by Intel's errata 82510 PC Software Compatibility. The 16550 data sheet is PC16550D Universal Asynchronous Receiver/Transmitter with FIFOs. To set the serial port and serial parameters, most Linux boot loaders use a syntax modeled upon the kernel's console parameter. The default value should be 9600bps, 8 data bits, no parity, 1 stop bit and CTS/RTS flow control.
Please do not ignore the lower speeds, as remote serial console is at its most valuable when the computer is located three days walk up a mountain in the New Guinea highlands. Be conservative in your use of the modem status lines. Advice for BIOS authors. User space. A modern computer operating system usually segregates virtual memory into kernel space and user space.
Ring (computer security) In computer science, hierarchical protection domains,[1][2] often called protection rings, are mechanisms to protect data and functionality from faults (by improving fault tolerance) and malicious behaviour (by providing computer security).
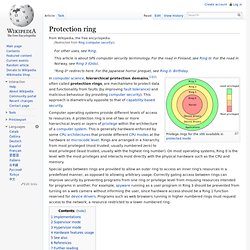
This approach is diametrically opposite to that of capability-based security. Special gates between rings are provided to allow an outer ring to access an inner ring's resources in a predefined manner, as opposed to allowing arbitrary usage. Correctly gating access between rings can improve security by preventing programs from one ring or privilege level from misusing resources intended for programs in another. For example, spyware running as a user program in Ring 3 should be prevented from turning on a web camera without informing the user, since hardware access should be a Ring 1 function reserved for device drivers.
Implementations[edit] Effective use of ring architecture requires close cooperation between hardware and the operating system.