

Grepping ASA syslogs for AnyConnect client logon/logoff activity. Ran across a Quick Question the other day: “Hey, can you quick tell me when so-and-so has been on the vpn in the last week?”
Everybody knows a quick question is anything but. This was no exception. The quick answer is “Sure, just let me look in the syslogs. Hang on.” To my genuine surprise, the syslogs we very large. 2+ Gbs for each day – way too large just to search in Notepad++ (Notepad and Wordpad actually refused to open the file). Once I figured that out, the next trick was to figure out what to grep for. Logging class auth trap informational logging class vpdn trap informational logging class vpn trap informational logging class vpnc trap informational logging class webvpn trap informational Turns out that class vpnc (VPNCLIENT) is not what you think. We’re using ASA software version 8.2.1, and Cisco syslog message documentation explains these messages like this: In Part 2, I’ll go into detail on how to search multiple syslogs files for these events with one command.
Register a Device with a FireSIGHT Management Center. Introduction.
ASA FirePOWER Module Quick Start Guide. Table of Contents Cisco ASA FirePOWER Module Quick Start Guide 1.
CLI Book 2: Cisco ASA Series Firewall CLI Configuration Guide, 9.2 - ASA FirePOWER (SFR) Module [Cisco ASA 5500-X Series Next-Generation Firewalls] The ASA FirePOWER Module The ASA FirePOWER module supplies next-generation firewall services, including Next-Generation IPS (NGIPS), Application Visibility and Control (AVC), URL filtering, and Advanced Malware Protection (AMP).You can use the module in single or multiple context mode, and in routed or transparent mode.
![CLI Book 2: Cisco ASA Series Firewall CLI Configuration Guide, 9.2 - ASA FirePOWER (SFR) Module [Cisco ASA 5500-X Series Next-Generation Firewalls]](http://cdn.pearltrees.com/s/pic/th/configuration-generation-126047559)
The module is also known as ASA SFR. Although the module has a basic command line interface (CLI) for initial configuration and troubleshooting, you configure the security policy on the device using a separate application, FireSIGHT Management Center, which can be hosted on a separate FireSIGHT Management Center appliance or as a virtual appliance running on a VMware server. ASA/PIX/FWSM: Packet Capturing using CLI and ASDM Configuration Example.
Introduction This document describes how to configure the Cisco 5500 Series Adaptive Security Appliance (ASA) to capture the desired packets using the Adaptive Security Device Manager (ASDM) or CLI.
The ASDM delivers world-class security management and monitoring through an intuitive, easy-to-use Web-based management interface. Prerequisites Requirements This document assumes that the ASA is fully operational and configured to allow the Cisco ASDM or CLI to make configuration changes. Note: Refer to Allowing HTTPS Access for ASDM or PIX/ASA 7.x: SSH on the Inside and Outside Interface Configuration Example to allow the device to be remotely configured by the ASDM or Secure Shell (SSH). Components Used The information in this document is based on these software and hardware versions: Cisco Adaptive Security Appliance Software Version 7.x and later Adaptive Security Device Manager Version 6.x and later The information in this document was created from the devices in a specific lab environment.
ASA 5500-X Sourcefire / FirePOWER configuration. I have not found any documentation to install/configure the sourcefire/firePOWER module on the 5500-X NGFW so I have decided to create my own.
I hope you find this helpful. *I have not figured all of this out - but this is a good starting point. As I get more information i'll update this post. . * Cisco ASA NAT Hairpin - private internal IP's accessing web server using public IP address. : networking. IPSec important Debugging and logging. I thought of sharing ipsec debugging and troubleshooting steps with everyone.
Being in VPN technology we explain this to many of our customers and thought of discussing it here on our support forum as well. What is IPSEC? IPSec stands for IP Security and the standard definition of IPSEC is-- “A security protocol in the network layer will be developed to provide cryptographic security services that will flexibly support combinations of authentication, integrity, access control, and confidentiality” (IETF) It is a standard for privacy, integrity and authenticity.
IPSEC Protocol Architecture. Site-to-site IPSec VPN through NAT. This post follows on from the first in this series and looks at how to modify the config if there is NAT along the way as well as reviewing a couple of the verification commands.
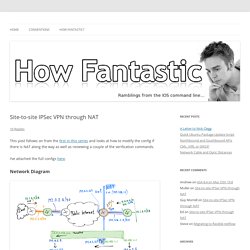
I’ve attached the full configs here. Network Diagram Premise A branch office with an ADSL connection would like to access corporate and local resources without running a local client on office machines. Split tunnelling is not required, all traffic must be routed back up to the corporate HQ. Config. KB0000216 - Troubleshooting Phase 1 Cisco Site to Site (L2L) VPN Tunnels. KB ID 0000216 Dtd 01/04/10 Problem Site to Site VPN's either work faultlessly straight away, or involve head scratching and a call to Cisco TAC, or someone like me to come and take a look.

If I'm honest, the simplest and best answer to the problem is "Remove the Tunnel from both ends and put it back again". Just about every VPN tunnel I've put in that did not work, was a result of my fat fingers putting in the wrong subnet, IP address or shared secret. However you can,t always remove the tunnel and start again, especially if you only have control of your end of the tunnel. Solution. CLI Book 3: Cisco ASA Series VPN CLI Configuration Guide, 9.1 - Configuring LAN-to-LAN VPNs [Cisco ASA 5500-X Series Next-Generation Firewalls] Install an Identity Certificate for ASDM.
Last Updated: May 8, 2015 When using some versions of Java, such as Version 7 update 51, the ASDM Launcher requires a trusted certificate.
An easy approach to fulfill the certificate requirements is to generate a self-signed identity certificate and to configure the ASA to use it when establishing an SSL connection. After you generate the identity certificate and configure the ASA, you need to register it with the Java Control Panel on your computer. Install and Configure a FirePOWER Services Module on an ASA Platform. Introduction. How to configure an ASA with built-in Sourcefire Firepower home lab. For those following Cisco security, you probably know Cisco acquired Sourcefire last year (more found HERE).
The most anticipated release has been adding Sourcefire’s flagship Firepower offering inside Cisco’s most popular firewall offering the Adaptive Security Appliance (ASA). As of September 16th, this offering is officially available. You can find data sheets, configuration guides and more on the new release HERE. This post will cover steps I used to build my ASA with Soucefire lab. You will need a version of the 2nd generation ASA with a SSD drive (NOTE: Sourcefire is not available in 1st generation ASAs).
NOTE: You can only run one additional feature package on the ASA. How to Setup Cisco ASA High Availability Failover Configuration for Firewall and VPN. Cisco ASA stands for Cisco Adaptive Security Appliance. Cisco ASA acts as both firewall and VPN device. Firewall - NAT one public IP to two inside servers on ASA 8.4. CLI Book 2: Cisco ASA Series Firewall CLI Configuration Guide, 9.3 - ASA FirePOWER (SFR) Module [Cisco ASA 5500-X Series Next-Generation Firewalls] The ASA FirePOWER Module The ASA FirePOWER module supplies next-generation firewall services, including Next-Generation Intrusion Prevention System (NGIPS), Application Visibility and Control (AVC), URL filtering, and Advanced Malware Protection (AMP).You can use the module in single or multiple context mode, and in routed or transparent mode.
The module is also known as ASA SFR. Although the module has a basic command line interface (CLI) for initial configuration and troubleshooting, you configure the security policy on the device using a separate application, FireSIGHT Management Center, which can be hosted on a separate FireSIGHT Management Center appliance or as a virtual appliance running on a VMware server. ASA: Active Directory LDAP for VPN Authentication. Below is a short sequence describing the steps an ASA takes when authenticating VPN users. PIX/ASA: Upgrade a Software Image using ASDM or CLI Configuration Example. Introduction. Upgrade to ASA 9.3 and ASDM 7.3. Released: August 21, 2014 Updated: December 1, 2014 Upgrade Path See the following table for the upgrade path for your version.
Some versions require an interim upgrade before you can upgrade to the latest version. Note. Cisco ASA Series CLI Configuration Guide, 9.0 - Configuring Clientless SSL VPN [Cisco ASA 5500-X Series Next-Generation Firewalls] Step 7 In some cases, the server may set the same cookie regardless of whether the authentication was successful or not, and such a cookie is unacceptable for SSO purposes. To confirm that the cookies are different, repeat Step 1 through Step 6 using invalid login credentials and then compare the “failure” cookie with the “success” cookie.You now have the necessary parameter data to configure the ASA for SSO with HTTP Form protocol.Configuring SSO for Plug-insPlug-ins support single sign-on (SSO).
They use the same credentials (username and password) entered to authenticate the clientless SSL VPN session. Because the plug-ins do not support macro substitution, you do not have the option to perform SSO on different fields, such as the internal domain password or the attribute on a RADIUS or LDAP server.To configure SSO support for a plug-in, you install the plug-in and add a bookmark entry to display a link to the server, specifying SSO support using the csco_sso=1 parameter. Upgrading a Cisco ASA Active/Standby Pair with Zero Downtime.