

HOME. Turning Nuclear Weapons into Nuclear Power. Nikolas Martelaro March 23, 2017 Submitted as coursework for PH241, Stanford University, Winter 2017 Introduction Though nuclear war has not been overbearing threat since the end of the Cold War, there are still fairly large stockpiles of nuclear weapons across the world.

As of 2015, the US still has approximately 2000 deployed warheads, 2000 reserve warheads, and 2000 waiting to be dismantled. [1] These stockpiles present a clear danger to humanity. However, it is possible to convert these weapons of mass destruction into usable energy for civilian usage. How much energy can we get from nuclear weapons? Energy Calculation The energy contained in bombs is listed in tonnes of TNT. As short example, we convert the energy of the Fat Man bomb dropped on Nagasaki. The corresponding amount of electric energy is 2/3 of this heat energy, or 5.5 × 1013 J. Quantum Politics. The Talon Conspiracy » The (in)Complete Library. TALON’s web minions are volunteers, and while we do update the site regularly, this page rarely gets touched!

For the most up to date listing of our available titles please check out our Site Map or start at the main page and scroll back. A mega collection of password cracking word lists. BlackwaterBay Forums. Download a free Emsisoft Decrypter for the latest file encryption ransomware. WireGuard: fast, modern, secure VPN tunnel. Hyc/fcrackzip: A braindead program for cracking encrypted ZIP archives. Forked from. SSTIC2018 Slides EN Backdooring your server through its BMC the HPE iLO4 case perigaud gazet czarny. LM, NTLM, Net-NTLMv2, oh my! – Péter Gombos. When attacking AD, passwords are stored and sent in different ways, depending on both where you find it and the age of the domain.
Most of these hashes are confusingly named, and both the hash name and the authentication protocol is named almost the same thing. It doesn’t help that every tool, post and guide that mentions credentials on Windows manage to add to the confusion. Ol-coyote/ExploitBuilderToolkit: Toolkit for basic bufferoverflow exploit building utilizing common metasploit tools in a graphical interface. Sécurité informatique - Ethical Hacking. Cosmos Search. A Review of the HackRF PortaPack (With Havok Firmware) - rtl-sdr.com. The PortaPack is a US$220 add-on for the HackRF software defined radio (HackRF + PortaPack + Accessory Amazon bundle) which allows you to go portable with the HackRF and a battery pack.
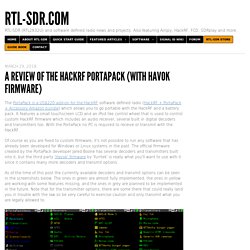
It features a small touchscreen LCD and an iPod like control wheel that is used to control custom HackRF firmware which includes an audio receiver, several built in digital decoders and transmitters too. With the PortaPack no PC is required to receive or transmit with the HackRF. Of course as you are fixed to custom firmware, it's not possible to run any software that has already been developed for Windows or Linux systems in the past. Pentest Box. Hashcat/hashcat: World's fastest and most advanced password recovery utility. Pentest Tips and Tricks – EK. Manisso/fsociety: fsociety Hacking Tools Pack – A Penetration Testing Framework.
NullArray/AutoSploit: Automated Mass Exploiter. Untitled. Posted by Felix, January 2017.
Author contact: Twitter | Mail | LinkedIn Tags: buffer overflow, shellcode, exploit, dll trampolining, visual studio. The Open Source Windows Previlege Escalation Cheat Sheet. This document is an open source markdown document that can be contributed to via github.
If you see a typo, a bug or a mistake, an improvment, or a vector that we've missed please send me a pull request to the master brunch via the repo link and I will review it and approve if approperiate asap. This document is meant for pen-testers, red teams, and the like. ** Needless to state: You're responosible for what you're doing :-) commands should be copiable from the boxes; windows inline command comments are noted as command &:: comment, so it still should work without messing your easy copy-paste style commands.
Think of it as the hash # in Linux.if two commands are required to run it's better to combine them into one line using the & delimiterif a command is an alternative to another; use the || delimiter so when command1 fails the second gets executed.AK | Author and Maintainer amAK.xyz, @xxByte Let's get to it! In this stage you want to learn as much as possible about the operating system. Reverse Shell Cheat Sheet. If you’re lucky enough to find a remote command execution vulnerability, you’ll more often than not want to connect back to your attacking machine to leverage an interactive shell.
Below are a collection of reverse shells that use commonly installed programming languages, or commonly installed binaries (nc, telnet, bash, etc). At the bottom of the post are a collection of uploadable reverse shells, present in Kali Linux. Setup Listening Netcat Your remote shell will need a listening netcat instance in order to connect back.
Set your Netcat listening shell on an allowed port Use a port that is likely allowed via outbound firewall rules on the target network, e.g. 80 / 443 To setup a listening netcat instance, enter the following: Install Lazykali, Hackpack and Kali linux Tools. To begin with, we are going to install lazykali, hackpack and kali linux tools today.
We will install lazykali and hackpack in kali linux and kali linux default tools in Ubuntu for those who like kali linux tools but prefer using other operating systems. Moreover, You can also use the same commands and scripts to install these tools into any other Debian based operating systems. Kali for Hackers: LazyKali script for Kali Linux. LazyKali is an awesome script written in bash shell.
It can automate the whole update and install new tools in your hack repository. As the name suggests, you can get all the updates on Kali Linux and your repositories in one place by running this script. Please read the description of the project here to know what tools are there that are going to be added when you run the script. Download lazykali.sh. * Warning: Disable firewall or Internet Security application if your Kali Linux is installed in a virtual machine. Exploit Exercises. Ferreirasc/oscp: oscp study. Enaqx/awesome-pentest: A collection of awesome penetration testing resources, tools and other shiny things. 0x00sec - The Home of the Hacker. Hacker Noon. 7. FlAWS. How to: Recon and Content Discovery. Exploit-db. Fully Featured Backdoor - Telegram C&C: BrainDamage. CyberPunk » Post Exploitation A python based backdoor which uses Telegram as C&C server.
Features PersistanceUSB spreadingPort ScannerRouter FinderRun shell commandsKeyloggerInsert keystrokesRecord audioWebserverScreenshot loggingDownload files in the hostExecute shutdown, restart, logoff, lockSend drive tree structureSet email templateRename FilesChange wallpaperOpen websiteSend Password for ChromeMozillaFilezillaCore FTPCyberDuckFTPNavigatorWinSCPOutlookPuttySkypeGeneric NetworkCookie stealerSend active windowsGather system information Drives listInternal and External IPIpconfig /all outputPlatform Setup Usage Run eclipse.py on host On first run: Files will be copied to startup pathRegistry entry will be madeWarning message will appear that file is corrupted.Folders will be made and set to hidden state.Passwords and cookies will be sent.Timestamps will be changedControl host from the Telegram app by sending commands. Tools. Amazon Price:N/A(as of December 25, 2017 08:32 – Details).
Product prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on the Amazon site at the time of purchase will apply to the purchase of this product. The Expansion Box Option adds more interfaces, ports and versatility to your Image MASSter Solo-4 Expansion Ready unit. Dissecting the Costs of Cybercriminal Operations. Let’s Enhance! How we found @rogerkver’s $1,000 wallet obfuscated private key. 3 — QR code standard part 1 It was important to understand how QR codes work and the limits of their ECC capabilities in restoring a damaged QR code. Wikipedia is a good start but everything we needed was in the ISO/IEC 18004 standard (There is a free version of the first edition on Swisseduc). How to build a 8 GPU password cracker — #_shellntel. Kamkar: PoisonTap - exploiting locked computers over USB. Created by @SamyKamkar || When PoisonTap (Raspberry Pi Zero & Node.js) is plugged into a locked/password protected computer, it: emulates an Ethernet device over USB (or Thunderbolt)hijacks all Internet traffic from the machine (despite being a low priority/unknown network interface)siphons and stores HTTP cookies and sessions from the web browser for the Alexa top 1,000,000 websitesexposes the internal router to the attacker, making it accessible remotely via outbound WebSocket and DNS rebinding (thanks Matt Austin for rebinding idea!)
Live demonstration and more details available in the video: A How-To in Homebrew Design, Fab, and Assembly with Structural Framing Systems. At this point, the internet is crawling with butt-kicking homebrew 3D printers made with extruded profiles, but it’s easy to underestimate the difficulty in getting there. Sure, most vendors sell a suite of interlocking connectors, but how well do these structural framing systems actually fare when put to the task of handling a build with sub-millimeter tolerances? I’ve been playing around with these parts for about two years. What I’ve found is that, yes, precise and accurate results are possible.
Nevertheless, those results came to me after I failed and–dry, rinse, repeat–failed again! Only after I understood the limits of both the materials and assembly processes was I able to deliver square, dimensionally accurate gantries that could carry a laser beam around a half-square-meter workbed. But First a Brief History Lesson.
Next Generation Web Scanner - WhatWeb. WhatWeb identifies websites. Its goal is to answer the question, “What is that Website?”. WhatWeb recognises web technologies including content management systems (CMS), blogging platforms, statistic/analytics packages, JavaScript libraries, web servers, and embedded devices. WhatWeb has over 1500 plugins, each to recognise something different. WhatWeb also identifies version numbers, email addresses, account IDs, web framework modules, SQL errors, and more. How to hack wifi password. How to hack wifi password kali linux tutorial. The Tactical Activists.
By Sakej, November 21, 2016 (via Facebook) Secure Desktops with Qubes: Compartmentalization. This is the third article in my series about Qubes. CyberPunk: Open Source CyberSecurity. Python tool for fetching "some" (usable) proxies. Bus Pirate. Neutralize ME firmware on SandyBridge and IvyBridge platforms. Author: persmule Mail: persmule@tya.email, persmule@gmail.com 00 ME: Management Engine. A Beginner Friendly Comprehensive Guide to Installing and Using A Safer Anonymous Operating System v1.0.2. Brutal Toolkit - Create Various Payload, PowerShell & Virus Attack on Kali Linux 2016.2. Pi Zero - Has anyone been able to install Kali Linux? : raspberry_pi.
Developer-Y/cs-video-courses: List of Computer Science courses with video lectures. Gridlock. Exercises. Vulnerable By Design ~ VulnHub. Practice. How to make USB Killer! Earth First! Mechanic's Guild. 20 Popular Wireless Hacking Tools. Last year, I wrote an article covering popular wireless hacking tools to crack or recover password of wireless network. We added 13 tools in that article which were popular and work great. Index of / I Got You01 This one weird trick will secure your web server David Coursey. How to hack a router remotely - millions of routers still vulnerable 2016.
A router is a gateway that connects a device to the internet with certain protocols. Hacking a router can be really serious, the attacker can take control over the whole network setup. Ncrack [RDP Bruteforce] Mr. Robot Hacks — Null Byte « Wonder How To. Programming Music 02. How to Evade AV Detection with Veil-Evasion. GitHub - goliate/hidden-tear: ransomware open-sources. HackTub. Main Page. Best Linux Distributions for Hacking and Penetration Testing in 2016. w4rri0r - Hacking Is Not A Crime - It's an art of Awareness. China Hacked Federal Deposit Insurance Corporation Via Backdoor Malware.
Integrating a Honey Pot into Your Network. Ethical Hacking with Kali Linux – Part 1: Objective. Online investigation tool - IP, DNS, MX, WHOIS and SEO tools. Parrot OS 3.0 (Lithium) - Friendly OS designed for Pentesting, Computer Forensic, Hacking, Cloud pentesting, Privacy/Anonimity and Cryptography. Enaqx/awesome-pentest. DigitalMunition - Ethical Hacking & Computer Security. Metasploit commands - Hacking Tutorials. Untitled. Grsecurity. Matriux - The Open Source Security Distribution for Ethical Hackers and Penetration Testers and Forensic Experts. Powershell - Referencing system.management.automation.dll in Visual Studio.
GitHub - Cn33liz/p0wnedShell: PowerShell Runspace Post Exploitation Toolkit. PowerOPS: PowerShell for Offensive Operations. Reversing and Exploiting Embedded Devices: The Software Stack (Part 1) 2000 cuts with Binary Ninja – Trail of Bits Blog. Garage Tech - Tech reviews and tutorials. MiniPwner Home. SWORD OpenWRT Hacking GUI. Anonymous Community. 6 addons Firefox que tout hacker doit avoir ! Live Hacking. Untitled. Airprobe. HackTub. Google Hacking Database, GHDB, Google Dorks. Google Hacking Diggity Project Resources - Bishop Fox. How To Build Your Own Rogue GSM BTS For Fun And Profit - Simone Margaritelli.