

Securing Your Lan. Securing Your Lan I was fortunate to learn about the security (or lack of) of a full time connection shortly after I was connected to my cable modem service.
The folks at my previous cable modem ISP, MediaOne, were on the ball and alerted me to the fact that their networks were being hacked via my proxy server and told me what to do about it. If you take the time to read all the pages on this topic, you should have a nice, secure shared Internet connection. However, if you're in a hurry, here's a guide to what's here: Mac Users: You can ignore the information in these pages that refers to Microsoft Networking related problems. 1.
It doesn't take a full-time connection to be hacked! Read this information about how I recently ended up with the netlog worm on my dialup connected system! So the precautions in this section apply to you whether you are connected via a full-time or connect-as-needed dial-up connection. IT Security Cookbook - Securing LAN/WAN Networks. Previous Next Top Detailed TOC Network security is vital.

Many applications (IBM 3270 telnet emulation, Telnet, ftp...) send unencrypted passwords across the network. Although a network cannot be completely secured, the weakest links should be protected. It is not realistic to expect the Network to be ever 100% secure. The are two principal tendencies in network security today: New applications being developed are often designed so that they can transfer data securely across insecure networks. i.e. some type of authentication / encryption is built-in. Network security could easily be enhanced if Vendors replaced relics such as ftp, telnet and rlogin with more secure alternatives such as ssh (see the "Mechanisms" chapter), if NIS+ and/or Kerberos clients were bundled with all major OSs and a secure email system such as pgp were fully integrated into vendors email clients.
Centralised network management is important for maintaining network security. 11.1 Network Model (OSI) 11.3.1 Ethernet. DMZ - Demilitarized Zone in Computer Networking. DMZ (computing) In computer security, a DMZ or Demilitarized Zone (sometimes referred to as a perimeter network) is a physical or logical subnetwork that contains and exposes an organization's external-facing services to a larger and untrusted network, usually the Internet.
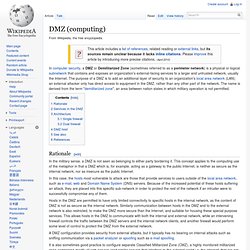
The purpose of a DMZ is to add an additional layer of security to an organization's local area network (LAN); an external attacker only has direct access to equipment in the DMZ, rather than any other part of the network. The name is derived from the term "demilitarized zone", an area between nation states in which military operation is not permitted. In the military sense, a DMZ is not seen as belonging to either party bordering it. This concept applies to the computing use of the metaphor in that a DMZ which is, for example, acting as a gateway to the public Internet, is neither as secure as the internal network, nor as insecure as the public Internet. Diagram of a typical network employing DMZ using dual firewalls.
IT Security - The Industry's Web Resource. Information security. Information Security Attributes: or qualities, i.e., Confidentiality, Integrity and Availability (CIA).
Information Systems are composed in three main portions, hardware, software and communications with the purpose to help identify and apply information security industry standards, as mechanisms of protection and prevention, at three levels or layers: physical, personal and organizational. Essentially, procedures or policies are implemented to tell people (administrators, users and operators) how to use products to ensure information security within the organizations.
Information security, sometimes shortened to InfoSec, is the practice of defending information from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction. It is a general term that can be used regardless of the form the data may take (electronic, physical, etc...)[1] Two major aspects of information security are: History[edit] Definitions[edit] 1. 2. 3. 4. 6. 7. 8.