

HTTP Strict Transport Security. HTTP Strict Transport Security (HSTS) is a web security policy mechanism whereby a web server declares that complying user agents (such as a web browser) are to interact with it using only secure HTTPS connections (i.e.
HTTP layered over TLS/SSL[1]). HSTS is an IETF standards track protocol and is specified in RFC 6797. The HSTS Policy[2] is communicated by the server to the user agent via a HTTP response header field named "Strict-Transport-Security". HSTS Policy specifies a period of time during which the user agent shall access the server in only secure fashion. Specification history[edit] The HSTS specification was published as RFC 6797 on 19 November 2012 after being approved on 2 October 2012 by the IESG for publication as a Proposed Standard RFC.[3] The authors originally submitted it as an Internet-Draft on 17 June 2010.
The last so-called "community version" of the then-named "STS" specification was published on 18 December 2009, with revisions based on community feedback.[5] HTTP Strict Transport Security. Da Wikipedia, l'enciclopedia libera.
Icona del lucchetto di HTTPS. HTTP Strict Transport Security o HSTS (in italiano sicurezza rigida per il trasporto di HTTP) è una procedura che implementa una politica di sicurezza per le comunicazioni web, necessaria a proteggere il canale HTTPS da attacchi di degrado della sicurezza (downgrade) e assai utile per la protezione dai dirottamenti di sessione. HSTS permette al server web di dichiarare che i browser e ogni altro tipo di client debbano comunicare con esso esclusivamente attraverso connessioni sicure su protocollo HTTPS e non sul semplice HTTP[1]. La procedura è uno standard di Internet della IETF, normato dal RFC 6797. La politica HSTS[2] è indicata dal server allo user agent specificando una particolare intestazione nei messaggi di risposta HTTP, denominata «Strict-Transport-Security» che specifica il periodo di tempo durante il quale il client dovrà accedere al server in modalità necessariamente sicura.
Note[modifica | modifica wikitesto] Strict-Transport-Security - HTTP. The HTTP Strict-Transport-Security response header (often abbreviated as HSTS) is a security feature that lets a web site tell browsers that it should only be communicated with using HTTPS, instead of using HTTP.
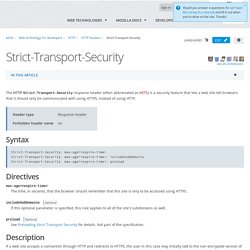
SyntaxEdit Strict-Transport-Security: max-age=<expire-time> Strict-Transport-Security: max-age=<expire-time>; includeSubDomains Strict-Transport-Security: max-age=<expire-time>; preload DirectivesEdit max-age=<expire-time> The time, in seconds, that the browser should remember that this site is only to be accessed using HTTPS. includeSubDomains Optional If this optional parameter is specified, this rule applies to all of the site's subdomains as well. preload Optional See Preloading Strict Transport Security for details.
DescriptionEdit If a web site accepts a connection through HTTP and redirects to HTTPS, the user in this case may initially talk to the non-encrypted version of the site before being redirected, if, for example, the user types or even just foo.com. An example scenario. HTTP Strict Transport Security Cheat Sheet. Last revision (mm/dd/yy): 09/11/2017 HTTP Strict Transport Security (HSTS) is an opt-in security enhancement that is specified by a web application through the use of a special response header.
Once a supported browser receives this header that browser will prevent any communications from being sent over HTTP to the specified domain and will instead send all communications over HTTPS. It also prevents HTTPS click through prompts on browsers. The specification has been released and published end of 2012 as RFC 6797 (HTTP Strict Transport Security (HSTS)) by the IETF. (Reference see in the links at the bottom.) Threats HSTS addresses the following threats: Examples Simple example, using a long (1 year) max-age. Strict-Transport-Security: max-age=31536000 This example is useful if all present and future subdomains will be HTTPS.
Strict-Transport-Security: max-age=31536000; includeSubDomains. Hyperlink. Definitions & Terminology, Networks.