

Montage, câblage, branchement d’un télérupteur et boutons poussoirs : Comment brancher un télérupteur ? MiniFablab – How to make almost anything. Bricole it Yourself: comment monter son fablab? 10 commandements Massimo Menichinelli est un chercheur italien fondateur de openp2pdesign, un site de recherche sur le design de processus et outils pour les communautés et leurs projets ouverts.
Dans un article publié en 2013, il listait les « 10 choses à faire pour ouvrir un fablab ». 1. Partir du contexte local et de ses spécificités. 2. Identifier sa communauté et l’impliquer. 3. Coffee Filter Dryer: 8 Steps. 6 Ways to Repair Broken Plastic. DIY Arduino CNC Drawing Machine: 17 Steps. AdWords We use AdWords to deploy digital advertising on sites supported by AdWords.
Ads are based on both AdWords data and behavioral data that we collect while you’re on our sites. The data we collect may include pages you’ve visited, trials you’ve initiated, videos you’ve played, purchases you’ve made, and your IP address or device ID. This information may be combined with data that AdWords has collected from you. We use the data that we provide to AdWords to better customize your digital advertising experience and present you with more relevant ads. LiveRamp We use LiveRamp to deploy digital advertising on sites supported by LiveRamp. Doubleclick We use Doubleclick to deploy digital advertising on sites supported by Doubleclick. RocketFuel We use RocketFuel to deploy digital advertising on sites supported by RocketFuel.
Twitter We use Twitter to deploy digital advertising on sites supported by Twitter. Facebook We use Facebook to deploy digital advertising on sites supported by Facebook. DIY balles au crochet - Idées conseils et tuto Crochet et tricot. - Commencez par enrouler le fil 2 fois autour de votre index et majeur.- Glissez ensuite le crochet dans la boucle puis faites une maille serrée.

R1 - 6 mailles serrées, 1 mc ds la 1ère m.R2 - 1 m en l'air, 2 ms dans chacune des mailles du rg précédent, 1 m coulée dans la 1ère maille (12m)R3 - 1m en l'air, *1ms, 2ms dans la m suivante*, répéter sur tout le rang, terminer par 1mc dans la 1ère maille (18m)R4 - 1 maille en l'air, * 2ms, 2ms dans la maille suivante*, répéter sur tout le rang. Mini CNC Drawbot from CD/DVD drive parts by manespgav. DVD-Plotter by kkman2266. Cd rom stepper motor linear rail system by tibuck. Dotter - Huge Arduino Based Dot Matrix Printer: 13 Steps. Share WiFi With Ethernet Port on a Raspberry Pi: 7 Steps. Dot Matrix Printer From a CD/DVD Reader With Arduino: 17 Steps. 8x8x8 LED Cube DIY Kit - How To Build and Review - Maker Advisor.
Data Recovery Forensic Tools & Equipment. Professional HDD Repair & Data Recovery Hardware-Software tools. ACELab Europe s.r.o., The Czech Republic. The PC-3000 SSD Software System operates in tandem with one of the three up-to-date hardware platforms – PC-3000 Express, PC-3000 UDMA, or PC-3000 Portable – and it is intended for SSD repair and diagnosis and for data recovery from SSDs with SATA, PATA, mSATA, and M.2 (NGFF) interfaces and the capacity from 64 GB to 1 Tb produced by different manufacturers, such as OCZ, Corsair, Crucial, RunCore, A-DATA, G.Skill, Micron, Plextor, Intel, Samsung, Seagate, Kingston and others.
OpenWRT/Belgacom Box2 (bbox2) OpenWRT workshop - Hackerspace Brussels. Port openwrt to the bbox2 Create openwrt packages that can be installed on the stock belgacom firmware (similar to /optware) JTAG access to the box Reflash the bootloader with another one Create an ikanos branch for openwrt (add Orange Livebox2, AliceGate, Sagem F@st 3464) Register on Doodle: of course some dudes left us, slackers, far behind : Go check Here a google translate [g.translate] Hello.
Belgacom Box 2 (Bbox2) - .[ZooBaB]. The Belgacom Box 2 (BBOX2) is a router used by Belgacom, the most popular Internet Service Provider (ISP) of Belgium, to provide access to thousands of subscribers in the country.
![Belgacom Box 2 (Bbox2) - .[ZooBaB].](http://cdn.pearltrees.com/s/pic/th/belgacom-box-2-bbox2-zoobab-168046650)
Statistics says that there are more then 300.000 of those boxes in circulation. It runs a modified version of Linux by default (OpenRG), and has 1 USB2.0 ports that allows people to modify it, and extend its features. 1 USB22 FXS1 switch 4 ports1 serial1 wifi atherosVDSL2Flash 16MBRAM 64MB1 JTAG Put here some pictures on where to solder a 4 pins header for obtaining the serial console. Build Your Own Savonius VAWT (Vertical Axis Wind Turbine): 8 Steps. DIY 1000 Watt Wind Turbine: 5 Steps. Netgear Wireless Cable Gateway CG3100D-2. Technovelty - Netgear CG3100D-2 investigation. The Netgear CG3100D-2 is the default cable-modem you get for Telstra Cable, at least at one time.
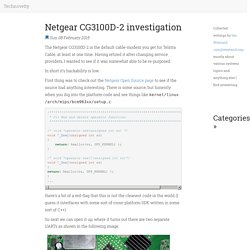
Having retired it after changing service providers, I wanted to see if it was somewhat able to be re-purposed. In short it's hackability is low. First thing was to check out the Netgear Open Source page to see if the source had anything interesting. There is some source, but honestly when you dig into the platform code and see things like kernel/linux/arch/mips/bcm963xx/setup.c: /*************************************************************************** * C++ New and delete operator functions ***************************************************************************/ /* void *operator new(unsigned int sz) */void *_Znwj(unsigned int sz){ return( kmalloc(sz, GFP_KERNEL) );} /* void *operator new[](unsigned int sz)*/void *_Znaj(unsigned int sz){return( kmalloc(sz, GFP_KERNEL) );}...
So next we can open it up, where it turns out there are two separate UARTs as shown in the following image. .JTAG NT. .CG3100D Cable modem. 12V DIY Stirling Generator Plans. The displacer cylinder : The displacer cylinder is made from a stainless steel water pasta container.
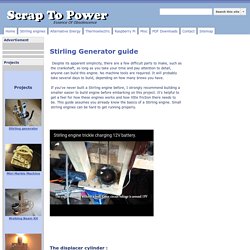
It's about 95mm diameter and cut down to be around 235 mm tall. Stainless steel can hold up to intense heat, and will not corrode easily, so it is a good choice. It's not a good idea to substitute an aluminium container, the performance is abysmal compared to a stainless steel bottle. Keep the lid from the pasta container, you'll need it for the diaphragm. I bent some flanges around the top to allow it to be secured solidly to the wooden parts.
How to make Mosquito Insect Killer at home. Reprap-Windturbine: Home. Moteur solaire et une éolienne avec une imprimante 3D. Fabriquez un moteur solaire et une éolienne avec une imprimante 3D Andreas Haeuser est un ingénieur en aéronautique basé en Allemagne.
Pendant plusieurs décennies, il utilisait des procédés de fabrication traditionnels tels que le fraisage CNC, mais depuis ces 5 dernières années, il s’est mis à utiliser des imprimantes 3D pour mener ses projets à bien. Une éolienne à axe vertical -4- En attendant de pouvoir travailler à nouveau sur le modèle taille réelle, j'ai réalisé une maquette, histoire de m'amuser un peu et de projeter plus facilement la mise en œuvre de solutions techniques sur l'éolienne tonneau.
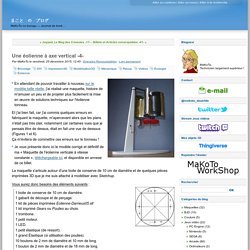
Et j'ai bien fait, car j'ai commis quelques erreurs en fabriquant la maquette, m'apercevant alors que les plans n'était pas très clair, notamment car certaines vues que je pensais être de dessus, était en fait une vue de dessous (Figures 1 et 6). Ça m'évitera de commettre ces erreurs sur le tonneau ! Je vous présente donc ici le modèle corrigé et définitif de ma « Maquette de l'éolienne verticale à vitesse constante », téléchargeable ici, et disponible en annexe de ce billet.
La maquette s'articule autour d'une boite de conserve de 10 cm de diamètre et de quelques pièces imprimées 3D que je me suis attaché à modéliser avec Sketchup. Vous aurez donc besoins des éléments suivants : Niveau outillage, pas besoin de grand chose, de quoi découper et percer. USB Virus Scanner - RaspberryPi. Cernés que nous sommes par les machines sous Windows®, en ce temps ou les virus courent si vite et où les cléUsb circulent trop facilement, il est souvent difficile de faire appliquer les règles de sécurités élémentaires à l'humain lambda, tant elles sont perçues comme barbantes et contraignantes, souvent à juste titre… Pour autant rien n'est perdu, un petit objet simple d'utilisation et d'aspect plutôt ludique pourrait se révéler être un pon début sur le chemin de la sensibilisation à la sécurité informatique.
FAN ESPEED CONTROL. 7 Répulsifs Naturels Contre les Insectes à l'Efficacité REDOUTABLE. Aïe, aïe, aïe ! Vous avez des fourmis dans votre évier ? Des tiques dans vos chaussettes ? Des moustiques qui bourdonnent dans votre oreille la nuit ? En été, tout le monde déteste ces invasions d’insectes. FAN STOPPED WORKING? Fix it!
Table fan malfunction, diagnosis and repair.