

Is Foursquare's Dennis Crowley Silicon Alley's Pied Piper? Things - Why yes, that is a Galaxy Tab 10.1 in my pocket. Knowing that we’re going to have to think about Android tablet development at some point, it was a matter of time before we picked one up.

The perfect storm of frugality swooped in this week as Staples had a $100 off coupon for tablets, excluding the Nook, TouchPad, and one or two others. This coupon, plus a few rebate cards I’d been saving meant I was able to snag a Samsung Galaxy Tab 10.1 for about $227. Sweet deal. Photos show the cultural difference between Black Hat and Defcon hacker events. Thousands of security professionals, hackers, federal agents and media descended on Las Vegas this week to attend the Black Hat and Defcon conferences.
The two conferences exhibit the extremes of hacker and security culture, with federal agents and major corporations descending on Black Hat in large numbers and mohawk-styled hackers and Electronic Frontier Foundation lawyers attending Defcon. It’s like the difference between law enforcement and pranksterism, where both have the object of protecting freedom. Defcon (named after the old code for nuclear war, or defense condition) is now in its 19th year. It was started in 1993 by Jeff Moss, a hacker also known as Dark Tangent. Defcon began as a party for a visiting Canadian hacker. The Web at 20: It Changed Everything. Army sending robo-jeeps to Afghanistan. This is the week of the robot-controlled vehicle.
Sometimes, it works wonderfully. And sometimes it crashes into another car that looks just like it. Still, the U.S. Is G+ Putting Facebook On The Defensive? Editor’s note: This guest post is written by Tom Anderson, the former President, founder and first friend on MySpace.

You can now find Tom on Facebook, Twitter, and Google+. If it’s not obvious yet, Google+ is going to be able to “undercut” Facebook when it comes to game developers and platform transactions. Instead of taking a 30% cut of all Farmville seeds (or whatever people are buying), Google will be able to take a smaller percentage for themselves. The Growing Portrait Of Google As A Big, Scary, Expanding Everywhere Copy Monster. Twice this year, Google’s been fairly frank and vocal about something competitors have done that it feels is unfair.
Twice, I’ve watched the technosphere largely react by beating the company over the head with a “You do whatever you want and copy everyone else” stick. Does that measure up, and more so than for Google than other companies? The first time was this happened was in the wake of Google’s accusations that Bing was copying its search results. The death of Web 2.0 is nigh. Publisher Tim O'Reilly at a recent conference.
Photograph: esri.com Perhaps it was the spurious precision of the headline that caught my eye. "Web 2.0 will end on October 1 2012", it said. The idea of a meme – an infectious idea – having a definite termination point was peculiar enough; but a meme as nebulous as Web 2.0? Of course the phrase had become ubiquitous in PR-speak over the past few years. Yahoo Wins Over Users, but Not Advertisers.
The problem has persisted despite many executive changes, revampings and rebranding campaigns that have tried to make Yahoo a destination as highly valued by its advertisers as its users.
Yahoo is second only to Google as the most-visited Web destination in the United States market, bringing in 178 million unique visitors monthly in June, according to comScore. That is a 27 percent increase over June 2008. But the company’s market capitalization is little changed from 2003. DEF CON: The event that scares hackers. The "Wall of Sheep" displays partially obscured usernames and passwords obtained by DEF CON hackers.
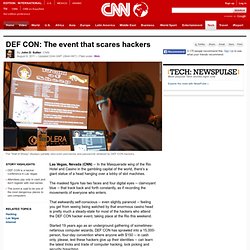
DEF CON is a hacker conference in Las Vegas Attendees pay only in cash and don't register with real names The event is said to be one of the most dangerous places to use computers Las Vegas, Nevada (CNN) -- In the Masquerade wing of the Rio Hotel and Casino in the gambling capital of the world, there's a giant statue of a head hanging over a lobby of slot machines. The masked figure has two faces and four digital eyes -- clairvoyant blue -- that track back and forth constantly, as if recording the movements of everyone who enters. Group hacks US law enforcement sites, steals data.