

Spring with Hibernate persistence and transactions example - byteslounge.com. Now we define the configuration file used for this example: Spring XML configuration file <?
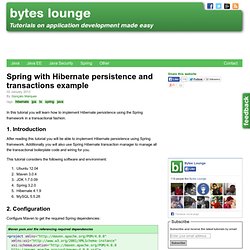
Xml version="1.0" encoding="UTF-8"? Important things to note in the configuration file: We define a datasource bean pointing to our MySQL instance. The sessionFactory bean represents the Hibernate session factory that will create sessions to interact with the database. We needed to define the packages where the container should look for Entities. There is also a transactionManager bean. Tx:annotation-driven element defines that we are declaring transactions using annotations in our classes (remember @Transactional annotations in our service layer?).
Note: In this example we used MySQL as the data repository so we need to specify the correct MySQL Driver in the dataSource bean. Securing session cookies in Tomcat with httpOnly and secure=true - Require a Secure Connection secure=true Using the Secure option you can tell the browser (or other http clients) to only send the cookie over SSL connections.
This means the cookie will not be available to any part of the site that is not secure will not have access to the cookie, but it also makes it much less likely that you’ll accidentally send the cookie across as cleartext. If you serve both http and https content, the non-secure http connection will then use URL re-writing with the long ";jsessionid=XXXXXXX" appended to every URL. You should set this to true ONLY if you are only serving https content, for mixed content this setting in NOT recomended.
Protect Against XSS Exploits with httpOnly. Security - How do you configure HttpOnly cookies in tomcat / java webapps. Seven Security (Mis)Configurations in Java web.xml Files. There are a lot of articles about configuring authentication and authorization in Java web.xml files.
Instead of rehashing how to configure roles, protect web resources, and set up different types of authentication let's look at some of the most common security misconfigurations in Java web.xml files. By default Java web applications display detailed error messages that disclose the server version and detailed stack trace information that can, in some situations, wind up displaying snippets of Java code. This information is a boon to hackers who are looking for as much information about their victims as possible. Fortunately it's very easy to configure web.xml to display custom error pages. Using the following configuration a nice error page will be displayed whenever the application responds with an HTTP 500 error. Additionally, web.xml needs to be configured to prevent detailed stack traces from being displayed by specifying the <exception-type> shown below.
Session Cookie HttpOnly Flag Java. What is it and why should I care?
Session cookies (or, to Java folks, the cookie containing the JSESSIONID) are the cookies used to perform session management for Web applications. These cookies hold the reference to the session identifier for a given user, and the same identifier − along with any session-scoped data related to that session id − is maintained server-side. Because cookies are transmitted on every request, they are the most common mechanism used for session management in Web applications. The HttpOnly flag is an additional flag that is used to prevent an XSS (Cross-Site Scripting) exploit from gaining access to the session cookie. Because one of the most common results of an XSS attack is access to the session cookie, and to subsequently hijack the victim’s session, the HttpOnly flag is a useful prevention mechanism. What should I do about it?
Here’s an example of how a session cookie might look without the HttpOnly flag: Cookie: jsessionid=AS348AF929FK219CKA9FK3B79870H; How to control cookies. All recent versions of popular browsers give users a level of control over cookies.
Users can set their browsers to accept or reject all, or certain, cookies. Users can also set their browser to prompt them each time a cookie is offered. The main browser types are listed below. If you have a different browser type, please contact us. You can also control Adobe Local Shared Objects on your computer, also known as LSOs or Flash cookies, but not with your browser. Windows PC Google Chrome Click on the "Tools" menu and select "Options". Google Chrome allows all cookies by default, but you can restrict the behaviour of first-party and third-party cookies or even block them completely. Click on the Close button when you've finished. Internet Explorer 8.0 Choose Tools and then Internet Options Click the Privacy tab Move the slider to choose your preferred settings. Internet Explorer 7.0 Choose Tools and then Internet Options Click the Privacy tab Move the slider to choose your preferred settings.
Opera. HttpOnly Cookies using web.xml servlet 3.0 in JBoss AS7 « JBoss. Hi,

Spring Security. Secure Cookies explained - Cookie Controller. A secure cookie, also known as an httpOnly cookie, is a file that is stored on a user’s hard drive.

It is used for transmitting http or https over the internet. HTTPS is a secure protocol and provides a secure method of sending data over your internet connection. It was a Microsoft extension originally. This mechanism was developed by Microsoft for IE6 SP1 to add some security.