

Scenario 3: VPC with Public and Private Subnets and Hardware VPN Access - Amazon Virtual Private Cloud. The configuration for this scenario includes a virtual private cloud (VPC) with a public subnet and a private subnet, and a virtual private gateway to enable communication with your own network over an IPsec VPN tunnel.
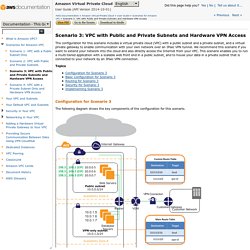
We recommend this scenario if you want to extend your network into the cloud and also directly access the Internet from your VPC. This scenario enables you to run a multi-tiered application with a scalable web front end in a public subnet, and to house your data in a private subnet that is connected to your network by an IPsec VPN connection. Configuration for Scenario 3 The following diagram shows the key components of the configuration for this scenario. Important For this scenario, the Amazon VPC Network Administrator Guide describes what your network administrator needs to do to configure the Amazon VPC customer gateway on your side of the VPN connection.
Basic Configuration for Scenario 3 A virtual private cloud (VPC) of size /16 (example CIDR: 10.0.0.0/16). Tip Note. Ec2-wg.pdf. Ec2-ug.pdf. Vpc-ug.pdf. Imagination Cubed. TOGAF®, an Open Group standard. Online Diagram Software to draw Flowcharts, UML & more. Zachman International® - The Official Home of The Zachman Framework™
Online diagramming application. Technology Research. Chapter 3 - Design Guidelines for Application Performance. Improving .NET Application Performance and Scalability J.D.
Meier, Srinath Vasireddy, Ashish Babbar, Rico Mariani, and Alex Mackman Microsoft Corporation May 2004 Related Links Home Page for Improving .NET Application Performance and Scalability Chapter 4 — Architecture and Design Review of a .NET Application for Performance and Scalability Checklist: Architecture and Design Review for Performance and Scalability Send feedback to Scale@microsoft.com patterns & practices Library Summary: This chapter presents a set of performance guidelines and principles for application architects and designers. Contents ObjectivesOverviewHow to Use This ChapterPrinciplesDeployment ConsiderationsScale Up vs. Objectives Learn design tradeoffs for performance and scalability. Overview Performance and scalability are two quality-of-service (QoS) considerations. During your design phase, identify performance objectives. How to Use This Chapter Jump to topics or read from beginning to end.
Principles Design Principles. KML FAQ - Keyhole Markup Language. What is KML?
KML is a file format used to display geographic data in an Earth browser, such as Google Earth, Google Maps, and Google Maps for mobile. You can create KML files to pinpoint locations, add image overlays, and expose rich data in new ways. KML is an international standard maintained by the Open Geospatial Consortium, Inc. (OGC). Who uses KML? The KML community is wide and varied, as you'll see when you visit the Google Earth community forum. How do I create KML files? There are three main tools for creating KML files. Excel To KML. Western United States only, in a number of formats.

Used in place of Latitude and Longitude or Position. The Quarter/Quarter closest to our example position 39° 18' 40.58" N 102° 17' 30.47" W is the SE 1/4 of the NW 1/4 of Section 35, Range 44 West, Township 8 South, Sixth Meridian, Colorado. Verbose, forward and reversed SE 1/4 of the NW 1/4 of Section 35, Range 44 West, Township 8 South, Sixth Meridian, Colorado Colorado, Sixth Meridian, Township 8 South, Range 44 West, Section 35, SE 1/4 of the NW 1/4 Abbreviated, forward and reversed SENW 35 44W 8S 6th CO CO 6th 8S 44W 35 SENW If there is no possibility of duplication, the state or the meridian can be dropped.
Amazon VPC Limits - Amazon Virtual Private Cloud. Using Putty to login AWS linux from Windows. DMZ in Network Security - Part1. Jeanne Ross of MIT CISR on Enterprise Architecture. Network Design.png. Download OpenSSH 6.7 Open Source Software Package. OpenSSH. IP Chicken - Whats my IP address? ip address lookup. SHA1 Hash Generator For File And Text. Wikispaces. Class Profile. Fedex Box-to-Fountain.kml. Network Design.jpg. Implementation plan.docx. Amazon Web Services Sign In. WiseMapping- Login.