

How to Devise Passwords That Drive Hackers Away. Within weeks, I set up unique, complex passwords for every Web site, enabled two-step authentication for my e-mail accounts, and even covered up my computer’s Web camera with a piece of masking tape — a precaution that invited ridicule from friends and co-workers who suggested it was time to get my head checked.
But recent episodes offered vindication. I removed the webcam tape — after a friend convinced me that it was a little much — only to see its light turn green a few days later, suggesting someone was in my computer and watching. More recently, I received a text message from Google with the two-step verification code for my Gmail account. That’s the string of numbers Google sends after you correctly enter the password to your Gmail account, and it serves as a second password. (Do sign up for it.) It is absurdly easy to get hacked. Chances are, most people will get hacked at some point in their lifetime. OR JUST JAM ON YOUR KEYBOARD For sensitive accounts, Mr. Stop au cyber-harcèlement : campagne-choc avec ressources et conseils. Un enregistreur des frappes de clavier de smartphone peut voler vos mots de passe ou vos SMS.
Quand vous tapez au clavier sur votre smartphone, vous devez sûrement apprécier le fait que les touches que vous saisissez sur le clavier virtuel de votre écran tactile s’affichent en étant agrandies : Si cela est bien pratique pour la lisibilité de ce que vous êtes en train de taper, c’est aussi un très bon moyen pour un logiciel d’enregistrer ce que vous êtes en train d’écrire à l’aide d’une simple caméra vidéo.
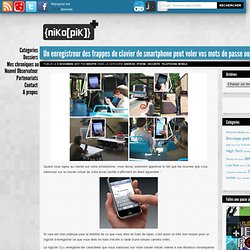
Le logiciel iSpy enregistre les caractères que vous saisissez sur votre clavier virtuel, même à une distance conséquente ou à partir d’un reflet de l’écran sur une paire de lunettes ou dans une fenêtre ! The Spy files. Smartphone et vie privée : un ami qui vous veut du bien ? Cette année encore, le smartphone sera en bonne place au pied du sapin de Noël. iPhone, Android, Windows Phone, BlackBerry… Ces "téléphones intelligents" ont déjà séduit 17 millions de Français grâce à leurs nombreuses fonctionnalités et aux tarifs alléchants proposés par les opérateurs.

La CNIL a cherché à mieux comprendre les pratiques des Français avec ces nouveaux accessoires technologiques. Guide pour gérer les aspects juridiques du Web 2.0 en milieu scolaire. Supercookies: What You Need to Know About the Web's Latest Tracking Device. Christian Olsen is the head of Levick Strategic Communications’ social and digital media practice.
Follow him on Twitter @cfolsendc. Recently, online properties like Hulu, MSN and Flixster have been caught using a tougher version of the common cookie. These “supercookies” (aka "Flash cookies" and “zombie cookies”) serve the same purpose as regular cookies by tracking user preferences and browsing histories. Unlike their popular cousins, however, this breed is difficult to detect and subsequently remove. These cookies secretly collect user data beyond the limitations of common industry practice, and thus raise serious privacy concerns. How Google collects data about you and the Internet. Google has, perhaps more than any other company, realized that information is power.
Information about the Internet, information about innumerable trends, and information about its users, YOU. So how much does Google know about you and your online habits? It’s only when you sit down and actually start listing all of the various Google services you use on a regular basis that you begin to realize how much information you’re handing over to Google. Moteur de recherche identité numérique : Yatedo et Youseemii.
How we found the rudest cities in the world – Analytics @ foursquare. Feb 28th With over 400 million check-ins in the last year, it’s safe to say that our servers log a lot of data.
We use that data to do a lot of interesting analysis, from finding the most popular local bars in any city, to recommending people you might know, and even for drawing pretty pictures. However, until recently, our data was only stored in production databases and log files. Most of the time this was fine, but whenever someone non-technical wanted to do some data exploration, it required them knowing scala and being able to query against production databases. This has become a larger problem as of late, as many of our business development managers, venue specialists, and upper management eggheads need access to the data in order to inform some important decisions. In short, without easy access to this data, we are not able to make smart decisions at any level of the company.
Thus we needed two things: De la difficulté de la rupture amoureuse à l’ère des réseaux sociaux » Article » OWNI, Digital Journalism. 34535427protege-ta-vie-privee-pdf.pdf (Objet application/pdf)
Where Have All The Old Tweets Gone? Looking for old tweets?
You won’t find any that are more than a week or so old on Twitter. Put the blame on all the massive number of new tweets coming in. The engines, they canna hold captain! Or that is, the search index behind Twitter Search can’t hold it all. NOTE: Since this was written, Google has launched an archive of old tweets. To see this in action, consider a search for “happy new year,” date restricted to New Year’s Day 2010. Loppsi 2 : caravanes, yourtes, troglos ? tout ça bientôt interdit ??? Tous ceux qui veulent vivre et habiter autrement sont en danger :
Centre de confidentialité. Masquer les exemples Afficher des exemples.
