

Internet Security. By Robert Hansen (SecTheory) & Jeremiah Grossman (WhiteHat Security) Date: 09/12/2008 Overview: Typically there is one type of attack - cross site request forgeries (CSRF) that can interact with functions on other websites.
The primary defense against CSRF is to create one time tokens (nonces) that are placed on the page and validated on supplemental pages, to ensure that the browser indeed picked up the nonce. Nonce evasion requires that the browser somehow gains access to data in another domain. Barring any client side vulnerabilities, reading cross domain is supposed to be disallowed by virtue of the browser's same origin policy. Clickjacking, however, evades the need for this cross domain reading, and instead directly places the mouse over the target area to click on the link or form that contains the nonce - thereby bypassing the need for client side cross domain read exploitation.
To understand the attack, let's dissect the various components. nLite - Deployment Tool for the bootable Unattended Windows installation. XN Resource Editor. XN Resource Editor is a free, powerful, fully featured resource editor and PE module explorer for Windows 98, Windows 2000 and Windows XP.
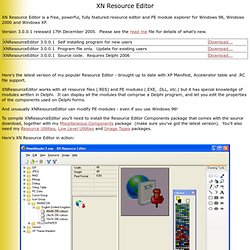
Version 3.0.0.1 released 17th December 2005. Please see the read me file for details of what's new. Here's the latest version of my popular Resource Editor - brought up to date with XP Manifest, Accelerator table and .RC file support. XNResourceEditor works with all resource files (.RES) and PE modules (.EXE, .DLL, etc.) but it has special knowledge of modules written in Delphi. It can display all the modules that comprise a Delphi program, and let you edit the properties of the components used on Delphi forms. And unusually XNResourceEditor can modify PE modules - even if you use Windows 98! To compile XNResourceEditor you'll need to install the Resource Editor Components package that comes with the source download, together with my Miscellaneous Components package (make sure you've got the latest version). Here's XN Resource Editor in action:
Is Your Son a Computer Hacker? As you can imagine, I was amazed.
A computer hacker in my own house! I began to monitor my son's habits, to make certain that Cindy wasn't just telling stories, as she is prone to doing at times. After a few days of investigation, and some research into computer hacking, I confronted Peter with the evidence. I'm afraid to say, this was the only time I have ever been truly disappointed in one of my children. We raised them to be honest and to have integrity, and Peter betrayed the principles we tried to encourage in him, when he refused point blank to admit to his activities. After going through this ordeal with my own family, I was left pondering how I could best help others in similar situations. To this end, I have decided to publish the top ten signs that your son is a hacker. 1.
Most American families use trusted and responsible Internet Service Providers, such as AOL. I would advise all parents to refuse this request. 2.